Merge branch 'master' of git.komect.net:ISG/secogateway
This commit is contained in:
commit
7eb76604a1
libs/src/libreswan-3.27
.gitignore.travis.ymlCHANGESCODE_OF_CONDUCT.mdCOPYINGCREDITSCROSSCOMPILE.shINSTALLLIBRESWAN-GPG-KEY.txtLICENSEMakefileMakefile.incMakefile.verREADME.KLIPSREADME.mdREADME.nssREADME.x509TRADEMARKbuildwin.sh
contrib
README
c-swan
cisco-decrypt
cisco-pcf
ipsec-dyndns
labeled-ipsec
ldsaref
lucent
munin
patching
python-swan
scripts
updown-example
docs
CHANGES.freeswan.plutoCHANGES.openswanCREDITS.freeswanCREDITS.openswanPlutoFlow.pngPlutoFlow.svgProgrammingConventions.txtREADME.IANA-PENREADME.OCFREADME.XAUTHREADME.labeledipsecREADME.rfcs
diagrams
examples
hub-spoke.confipv6.confl2tp-cert.confl2tp-psk.conflinux-linux.confmast-l2tp-psk.confoe-authnull.confoe-dnssec-client.confoe-dnssec-server.confoe-exclude-dns.confoe-letsencrypt-README.txtoe-letsencrypt-client.confoe-letsencrypt-server.confoe-upgrade-authnull.confsysctl.confxauth.conf
ipsecsaref.pngklips-mast
klips-using-kernel-crypto
l2tp-overhead.txtnss-howto.txtopportunistic-v1.historic
pluto-internals.txttesting
win2k-notes.txtwindows-cross-compile.txt|
|
@ -0,0 +1,32 @@
|
|||
*~
|
||||
.*.sw?
|
||||
\#*\#
|
||||
.\#*
|
||||
BACKUP
|
||||
RESULTS
|
||||
DEADJOE
|
||||
OBJ.*
|
||||
*.rej
|
||||
*.orig
|
||||
*.bak
|
||||
*.pyc
|
||||
*.o
|
||||
TAGS
|
||||
tags
|
||||
modobj
|
||||
modobj24
|
||||
modobj26
|
||||
testing/*/*/OUTPUT*
|
||||
testing/x509/*/*
|
||||
testing/x509/index.*
|
||||
testing/x509/crlnumber.*
|
||||
testing/x509/serial*
|
||||
testing/x509/nss-pw
|
||||
osxApp/build
|
||||
Makefile.inc.local
|
||||
.ycm_extra_conf.py
|
||||
cscope.out
|
||||
testing/baseconfigs/all/etc/bind/signed/*.signed
|
||||
testing/baseconfigs/all/etc/bind/keys/*.key
|
||||
testing/baseconfigs/all/etc/bind/keys/*.private
|
||||
testing/baseconfigs/all/etc/bind/dsset/dsset*
|
||||
|
|
@ -0,0 +1,26 @@
|
|||
sudo: required
|
||||
|
||||
services: docker
|
||||
|
||||
language: c
|
||||
|
||||
os:
|
||||
- linux
|
||||
|
||||
compiler:
|
||||
- gcc
|
||||
|
||||
before_install:
|
||||
- echo $PWD
|
||||
- git rev-parse --abbrev-ref HEAD
|
||||
- git checkout $TRAVIS_BRANCH
|
||||
#
|
||||
# 'make travis-docker-image' reads the branch name
|
||||
# <travis>-<distro>-<rel> or default to Fedora 27
|
||||
#
|
||||
- make travis-docker-image
|
||||
- sudo docker run -h west --privileged --net=none --name swanbase -v $PWD:/home/build/libreswan -v /sys/fs/cgroup:/sys/fs/cgroup:ro -d swanbase
|
||||
|
||||
script:
|
||||
- sudo docker exec -ti swanbase /bin/bash -c 'cd /home/build/libreswan && make base'
|
||||
- sudo docker exec -ti swanbase /bin/bash -c 'cd /home/build/libreswan && make install-base'
|
||||
File diff suppressed because it is too large
Load Diff
|
|
@ -0,0 +1,24 @@
|
|||
# Contributor Code of Conduct
|
||||
|
||||
As contributors and maintainers of this project, and in the interest of fostering an open and welcoming community, we pledge to respect all people who contribute through reporting issues, posting feature requests, updating documentation, submitting pull requests or patches, and other activities.
|
||||
|
||||
We are committed to making participation in this project a harassment-free experience for everyone, regardless of level of experience, gender, gender identity and expression, sexual orientation, disability, personal appearance, body size, race, ethnicity, age, religion, or nationality.
|
||||
|
||||
Examples of unacceptable behavior by participants include:
|
||||
|
||||
* The use of sexualized language or imagery
|
||||
* Personal attacks
|
||||
* Trolling or insulting/derogatory comments
|
||||
* Public or private harassment
|
||||
* Publishing other's private information, such as physical or electronic addresses, without explicit permission
|
||||
* Other unethical or unprofessional conduct
|
||||
|
||||
Project maintainers have the right and responsibility to remove, edit, or reject comments, commits, code, wiki edits, issues, and other contributions that are not aligned to this Code of Conduct, or to ban temporarily or permanently any contributor for other behaviors that they deem inappropriate, threatening, offensive, or harmful.
|
||||
|
||||
By adopting this Code of Conduct, project maintainers commit themselves to fairly and consistently applying these principles to every aspect of managing this project. Project maintainers who do not follow or enforce the Code of Conduct may be permanently removed from the project team.
|
||||
|
||||
This code of conduct applies both within project spaces and in public spaces when an individual is representing the project or its community.
|
||||
|
||||
Instances of abusive, harassing, or otherwise unacceptable behavior may be reported by contacting a project maintainer at abuse@libreswan.org. All complaints will be reviewed and investigated and will result in a response that is deemed necessary and appropriate to the circumstances. Maintainers are obligated to maintain confidentiality with regard to the reporter of an incident.
|
||||
|
||||
This Code of Conduct is adapted from the [Contributor Covenant](https://contributor-covenant.org), version 1.3.0, available at [https://contributor-covenant.org/version/1/3/0/](https://contributor-covenant.org/version/1/3/0/)
|
||||
|
|
@ -0,0 +1,339 @@
|
|||
GNU GENERAL PUBLIC LICENSE
|
||||
Version 2, June 1991
|
||||
|
||||
Copyright (C) 1989, 1991 Free Software Foundation, Inc.,
|
||||
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
|
||||
Everyone is permitted to copy and distribute verbatim copies
|
||||
of this license document, but changing it is not allowed.
|
||||
|
||||
Preamble
|
||||
|
||||
The licenses for most software are designed to take away your
|
||||
freedom to share and change it. By contrast, the GNU General Public
|
||||
License is intended to guarantee your freedom to share and change free
|
||||
software--to make sure the software is free for all its users. This
|
||||
General Public License applies to most of the Free Software
|
||||
Foundation's software and to any other program whose authors commit to
|
||||
using it. (Some other Free Software Foundation software is covered by
|
||||
the GNU Lesser General Public License instead.) You can apply it to
|
||||
your programs, too.
|
||||
|
||||
When we speak of free software, we are referring to freedom, not
|
||||
price. Our General Public Licenses are designed to make sure that you
|
||||
have the freedom to distribute copies of free software (and charge for
|
||||
this service if you wish), that you receive source code or can get it
|
||||
if you want it, that you can change the software or use pieces of it
|
||||
in new free programs; and that you know you can do these things.
|
||||
|
||||
To protect your rights, we need to make restrictions that forbid
|
||||
anyone to deny you these rights or to ask you to surrender the rights.
|
||||
These restrictions translate to certain responsibilities for you if you
|
||||
distribute copies of the software, or if you modify it.
|
||||
|
||||
For example, if you distribute copies of such a program, whether
|
||||
gratis or for a fee, you must give the recipients all the rights that
|
||||
you have. You must make sure that they, too, receive or can get the
|
||||
source code. And you must show them these terms so they know their
|
||||
rights.
|
||||
|
||||
We protect your rights with two steps: (1) copyright the software, and
|
||||
(2) offer you this license which gives you legal permission to copy,
|
||||
distribute and/or modify the software.
|
||||
|
||||
Also, for each author's protection and ours, we want to make certain
|
||||
that everyone understands that there is no warranty for this free
|
||||
software. If the software is modified by someone else and passed on, we
|
||||
want its recipients to know that what they have is not the original, so
|
||||
that any problems introduced by others will not reflect on the original
|
||||
authors' reputations.
|
||||
|
||||
Finally, any free program is threatened constantly by software
|
||||
patents. We wish to avoid the danger that redistributors of a free
|
||||
program will individually obtain patent licenses, in effect making the
|
||||
program proprietary. To prevent this, we have made it clear that any
|
||||
patent must be licensed for everyone's free use or not licensed at all.
|
||||
|
||||
The precise terms and conditions for copying, distribution and
|
||||
modification follow.
|
||||
|
||||
GNU GENERAL PUBLIC LICENSE
|
||||
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
|
||||
|
||||
0. This License applies to any program or other work which contains
|
||||
a notice placed by the copyright holder saying it may be distributed
|
||||
under the terms of this General Public License. The "Program", below,
|
||||
refers to any such program or work, and a "work based on the Program"
|
||||
means either the Program or any derivative work under copyright law:
|
||||
that is to say, a work containing the Program or a portion of it,
|
||||
either verbatim or with modifications and/or translated into another
|
||||
language. (Hereinafter, translation is included without limitation in
|
||||
the term "modification".) Each licensee is addressed as "you".
|
||||
|
||||
Activities other than copying, distribution and modification are not
|
||||
covered by this License; they are outside its scope. The act of
|
||||
running the Program is not restricted, and the output from the Program
|
||||
is covered only if its contents constitute a work based on the
|
||||
Program (independent of having been made by running the Program).
|
||||
Whether that is true depends on what the Program does.
|
||||
|
||||
1. You may copy and distribute verbatim copies of the Program's
|
||||
source code as you receive it, in any medium, provided that you
|
||||
conspicuously and appropriately publish on each copy an appropriate
|
||||
copyright notice and disclaimer of warranty; keep intact all the
|
||||
notices that refer to this License and to the absence of any warranty;
|
||||
and give any other recipients of the Program a copy of this License
|
||||
along with the Program.
|
||||
|
||||
You may charge a fee for the physical act of transferring a copy, and
|
||||
you may at your option offer warranty protection in exchange for a fee.
|
||||
|
||||
2. You may modify your copy or copies of the Program or any portion
|
||||
of it, thus forming a work based on the Program, and copy and
|
||||
distribute such modifications or work under the terms of Section 1
|
||||
above, provided that you also meet all of these conditions:
|
||||
|
||||
a) You must cause the modified files to carry prominent notices
|
||||
stating that you changed the files and the date of any change.
|
||||
|
||||
b) You must cause any work that you distribute or publish, that in
|
||||
whole or in part contains or is derived from the Program or any
|
||||
part thereof, to be licensed as a whole at no charge to all third
|
||||
parties under the terms of this License.
|
||||
|
||||
c) If the modified program normally reads commands interactively
|
||||
when run, you must cause it, when started running for such
|
||||
interactive use in the most ordinary way, to print or display an
|
||||
announcement including an appropriate copyright notice and a
|
||||
notice that there is no warranty (or else, saying that you provide
|
||||
a warranty) and that users may redistribute the program under
|
||||
these conditions, and telling the user how to view a copy of this
|
||||
License. (Exception: if the Program itself is interactive but
|
||||
does not normally print such an announcement, your work based on
|
||||
the Program is not required to print an announcement.)
|
||||
|
||||
These requirements apply to the modified work as a whole. If
|
||||
identifiable sections of that work are not derived from the Program,
|
||||
and can be reasonably considered independent and separate works in
|
||||
themselves, then this License, and its terms, do not apply to those
|
||||
sections when you distribute them as separate works. But when you
|
||||
distribute the same sections as part of a whole which is a work based
|
||||
on the Program, the distribution of the whole must be on the terms of
|
||||
this License, whose permissions for other licensees extend to the
|
||||
entire whole, and thus to each and every part regardless of who wrote it.
|
||||
|
||||
Thus, it is not the intent of this section to claim rights or contest
|
||||
your rights to work written entirely by you; rather, the intent is to
|
||||
exercise the right to control the distribution of derivative or
|
||||
collective works based on the Program.
|
||||
|
||||
In addition, mere aggregation of another work not based on the Program
|
||||
with the Program (or with a work based on the Program) on a volume of
|
||||
a storage or distribution medium does not bring the other work under
|
||||
the scope of this License.
|
||||
|
||||
3. You may copy and distribute the Program (or a work based on it,
|
||||
under Section 2) in object code or executable form under the terms of
|
||||
Sections 1 and 2 above provided that you also do one of the following:
|
||||
|
||||
a) Accompany it with the complete corresponding machine-readable
|
||||
source code, which must be distributed under the terms of Sections
|
||||
1 and 2 above on a medium customarily used for software interchange; or,
|
||||
|
||||
b) Accompany it with a written offer, valid for at least three
|
||||
years, to give any third party, for a charge no more than your
|
||||
cost of physically performing source distribution, a complete
|
||||
machine-readable copy of the corresponding source code, to be
|
||||
distributed under the terms of Sections 1 and 2 above on a medium
|
||||
customarily used for software interchange; or,
|
||||
|
||||
c) Accompany it with the information you received as to the offer
|
||||
to distribute corresponding source code. (This alternative is
|
||||
allowed only for noncommercial distribution and only if you
|
||||
received the program in object code or executable form with such
|
||||
an offer, in accord with Subsection b above.)
|
||||
|
||||
The source code for a work means the preferred form of the work for
|
||||
making modifications to it. For an executable work, complete source
|
||||
code means all the source code for all modules it contains, plus any
|
||||
associated interface definition files, plus the scripts used to
|
||||
control compilation and installation of the executable. However, as a
|
||||
special exception, the source code distributed need not include
|
||||
anything that is normally distributed (in either source or binary
|
||||
form) with the major components (compiler, kernel, and so on) of the
|
||||
operating system on which the executable runs, unless that component
|
||||
itself accompanies the executable.
|
||||
|
||||
If distribution of executable or object code is made by offering
|
||||
access to copy from a designated place, then offering equivalent
|
||||
access to copy the source code from the same place counts as
|
||||
distribution of the source code, even though third parties are not
|
||||
compelled to copy the source along with the object code.
|
||||
|
||||
4. You may not copy, modify, sublicense, or distribute the Program
|
||||
except as expressly provided under this License. Any attempt
|
||||
otherwise to copy, modify, sublicense or distribute the Program is
|
||||
void, and will automatically terminate your rights under this License.
|
||||
However, parties who have received copies, or rights, from you under
|
||||
this License will not have their licenses terminated so long as such
|
||||
parties remain in full compliance.
|
||||
|
||||
5. You are not required to accept this License, since you have not
|
||||
signed it. However, nothing else grants you permission to modify or
|
||||
distribute the Program or its derivative works. These actions are
|
||||
prohibited by law if you do not accept this License. Therefore, by
|
||||
modifying or distributing the Program (or any work based on the
|
||||
Program), you indicate your acceptance of this License to do so, and
|
||||
all its terms and conditions for copying, distributing or modifying
|
||||
the Program or works based on it.
|
||||
|
||||
6. Each time you redistribute the Program (or any work based on the
|
||||
Program), the recipient automatically receives a license from the
|
||||
original licensor to copy, distribute or modify the Program subject to
|
||||
these terms and conditions. You may not impose any further
|
||||
restrictions on the recipients' exercise of the rights granted herein.
|
||||
You are not responsible for enforcing compliance by third parties to
|
||||
this License.
|
||||
|
||||
7. If, as a consequence of a court judgment or allegation of patent
|
||||
infringement or for any other reason (not limited to patent issues),
|
||||
conditions are imposed on you (whether by court order, agreement or
|
||||
otherwise) that contradict the conditions of this License, they do not
|
||||
excuse you from the conditions of this License. If you cannot
|
||||
distribute so as to satisfy simultaneously your obligations under this
|
||||
License and any other pertinent obligations, then as a consequence you
|
||||
may not distribute the Program at all. For example, if a patent
|
||||
license would not permit royalty-free redistribution of the Program by
|
||||
all those who receive copies directly or indirectly through you, then
|
||||
the only way you could satisfy both it and this License would be to
|
||||
refrain entirely from distribution of the Program.
|
||||
|
||||
If any portion of this section is held invalid or unenforceable under
|
||||
any particular circumstance, the balance of the section is intended to
|
||||
apply and the section as a whole is intended to apply in other
|
||||
circumstances.
|
||||
|
||||
It is not the purpose of this section to induce you to infringe any
|
||||
patents or other property right claims or to contest validity of any
|
||||
such claims; this section has the sole purpose of protecting the
|
||||
integrity of the free software distribution system, which is
|
||||
implemented by public license practices. Many people have made
|
||||
generous contributions to the wide range of software distributed
|
||||
through that system in reliance on consistent application of that
|
||||
system; it is up to the author/donor to decide if he or she is willing
|
||||
to distribute software through any other system and a licensee cannot
|
||||
impose that choice.
|
||||
|
||||
This section is intended to make thoroughly clear what is believed to
|
||||
be a consequence of the rest of this License.
|
||||
|
||||
8. If the distribution and/or use of the Program is restricted in
|
||||
certain countries either by patents or by copyrighted interfaces, the
|
||||
original copyright holder who places the Program under this License
|
||||
may add an explicit geographical distribution limitation excluding
|
||||
those countries, so that distribution is permitted only in or among
|
||||
countries not thus excluded. In such case, this License incorporates
|
||||
the limitation as if written in the body of this License.
|
||||
|
||||
9. The Free Software Foundation may publish revised and/or new versions
|
||||
of the General Public License from time to time. Such new versions will
|
||||
be similar in spirit to the present version, but may differ in detail to
|
||||
address new problems or concerns.
|
||||
|
||||
Each version is given a distinguishing version number. If the Program
|
||||
specifies a version number of this License which applies to it and "any
|
||||
later version", you have the option of following the terms and conditions
|
||||
either of that version or of any later version published by the Free
|
||||
Software Foundation. If the Program does not specify a version number of
|
||||
this License, you may choose any version ever published by the Free Software
|
||||
Foundation.
|
||||
|
||||
10. If you wish to incorporate parts of the Program into other free
|
||||
programs whose distribution conditions are different, write to the author
|
||||
to ask for permission. For software which is copyrighted by the Free
|
||||
Software Foundation, write to the Free Software Foundation; we sometimes
|
||||
make exceptions for this. Our decision will be guided by the two goals
|
||||
of preserving the free status of all derivatives of our free software and
|
||||
of promoting the sharing and reuse of software generally.
|
||||
|
||||
NO WARRANTY
|
||||
|
||||
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
|
||||
FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
|
||||
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES
|
||||
PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED
|
||||
OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
|
||||
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS
|
||||
TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
|
||||
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING,
|
||||
REPAIR OR CORRECTION.
|
||||
|
||||
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
|
||||
WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR
|
||||
REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES,
|
||||
INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING
|
||||
OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED
|
||||
TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY
|
||||
YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER
|
||||
PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
|
||||
POSSIBILITY OF SUCH DAMAGES.
|
||||
|
||||
END OF TERMS AND CONDITIONS
|
||||
|
||||
How to Apply These Terms to Your New Programs
|
||||
|
||||
If you develop a new program, and you want it to be of the greatest
|
||||
possible use to the public, the best way to achieve this is to make it
|
||||
free software which everyone can redistribute and change under these terms.
|
||||
|
||||
To do so, attach the following notices to the program. It is safest
|
||||
to attach them to the start of each source file to most effectively
|
||||
convey the exclusion of warranty; and each file should have at least
|
||||
the "copyright" line and a pointer to where the full notice is found.
|
||||
|
||||
<one line to give the program's name and a brief idea of what it does.>
|
||||
Copyright (C) <year> <name of author>
|
||||
|
||||
This program is free software; you can redistribute it and/or modify
|
||||
it under the terms of the GNU General Public License as published by
|
||||
the Free Software Foundation; either version 2 of the License, or
|
||||
(at your option) any later version.
|
||||
|
||||
This program is distributed in the hope that it will be useful,
|
||||
but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
GNU General Public License for more details.
|
||||
|
||||
You should have received a copy of the GNU General Public License along
|
||||
with this program; if not, write to the Free Software Foundation, Inc.,
|
||||
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
|
||||
|
||||
Also add information on how to contact you by electronic and paper mail.
|
||||
|
||||
If the program is interactive, make it output a short notice like this
|
||||
when it starts in an interactive mode:
|
||||
|
||||
Gnomovision version 69, Copyright (C) year name of author
|
||||
Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
|
||||
This is free software, and you are welcome to redistribute it
|
||||
under certain conditions; type `show c' for details.
|
||||
|
||||
The hypothetical commands `show w' and `show c' should show the appropriate
|
||||
parts of the General Public License. Of course, the commands you use may
|
||||
be called something other than `show w' and `show c'; they could even be
|
||||
mouse-clicks or menu items--whatever suits your program.
|
||||
|
||||
You should also get your employer (if you work as a programmer) or your
|
||||
school, if any, to sign a "copyright disclaimer" for the program, if
|
||||
necessary. Here is a sample; alter the names:
|
||||
|
||||
Yoyodyne, Inc., hereby disclaims all copyright interest in the program
|
||||
`Gnomovision' (which makes passes at compilers) written by James Hacker.
|
||||
|
||||
<signature of Ty Coon>, 1 April 1989
|
||||
Ty Coon, President of Vice
|
||||
|
||||
This General Public License does not permit incorporating your program into
|
||||
proprietary programs. If your program is a subroutine library, you may
|
||||
consider it more useful to permit linking proprietary applications with the
|
||||
library. If this is what you want to do, use the GNU Lesser General
|
||||
Public License instead of this License.
|
||||
|
|
@ -0,0 +1,28 @@
|
|||
The following people have contributed major resources or significant
|
||||
patches to The Libreswan Project.
|
||||
|
||||
Avesh Agarwal <avagarwa@redhat.com>
|
||||
Antony Antony <antony@phenome.org>
|
||||
Richard Guy Briggs <rgb@tricolour.ca>
|
||||
Andrew Cagney <andrew.cagney@gmail.com>
|
||||
Daniel Kahn Gillmor <dkg@fifthhorseman.net>
|
||||
Wes Hardaker <opensource@hardakers.net>
|
||||
Kim B. Heino <b@bbbs.net>
|
||||
David McCullough <david_mccullough@mcafee.com>
|
||||
Amir Naftali <amir@fortycloud.com>
|
||||
Wolfgang Nothdurft <wolfgang@linogate.de>
|
||||
Hugh Redelmeier <hugh@mimosa.com>
|
||||
Lubomir Rintel <lkundrak@v3.sk>
|
||||
Matt Rogers <mrogers@redhat.com>
|
||||
Tuomo Soini <tis@foobar.fi>
|
||||
Philippe Vouters <Philippe.Vouters@laposte.net>
|
||||
Paul Wouters <pwouters@redhat.com>
|
||||
Herbert Xu <herbert@gondor.apana.org.au>
|
||||
|
||||
Libreswan is a fork of the Openswan 2.6.38 codebase.
|
||||
Please see the docs/CREDITS.openswan file from Openswan for details on
|
||||
original work.
|
||||
|
||||
Openswan is a fork of the FreeS/WAN 2.04 codebase.
|
||||
Please see the doc/CREDITS.freeswan file from FreeS/WAN for details on
|
||||
original work.
|
||||
|
|
@ -0,0 +1,41 @@
|
|||
#!/bin/sh
|
||||
#
|
||||
# cross compile example
|
||||
#
|
||||
|
||||
|
||||
#export PREFIX=/volquad/arm-4.0.2
|
||||
export PREFIX=/usr/local/arm_tools
|
||||
export DESTDIR=/tmp/libreswan.arm
|
||||
|
||||
export ARCH=arm
|
||||
export CC=$PREFIX/bin/arm-elf-gcc
|
||||
export GCC=$PREFIX/bin/arm-elf-gcc
|
||||
export LD=$PREFIX/bin/arm-elf-ld
|
||||
export RANLIB=$PREFIX/bin/arm-elf-ranlib
|
||||
export AR=$PREFIX/bin/arm-elf-ar
|
||||
export AS=$PREFIX/bin/arm-elf-as
|
||||
export STRIP=$PREFIX/bin/arm-elf-strip
|
||||
export LD_LIBRARY_PATH=$PREFIX/lib/gcc-lib/arm-elf/3.0/
|
||||
export PATH=$PATH:$PREFIX/bin
|
||||
export USERCOMPILE="-Wl,-elf2flt -DCOMPILER_HAS_NO_PRINTF_LIKE -O3 -g ${PORTDEFINE} -I$PREFIX/arm-elf/inc -L$PREFIX/lib/gcc-lib -DGCC_LINT -Dlinux -D__linux__"
|
||||
export WERROR=' '
|
||||
|
||||
#now you can run:
|
||||
# make programs
|
||||
#and binaries will appear in OBJ.linux.$ARCH/
|
||||
#and run:
|
||||
# make install
|
||||
#and the install will go into $DESTDIR/
|
||||
|
||||
# note: the arm_tools I had failed to compile PRINTF_LIKE(x), so the code
|
||||
# for that was ifdef'ed with #ifndef COMPILER_HAS_NO_PRINTF_LIKE statements.
|
||||
# Add -DCOMPILER_HAS_NO_PRINTF_LIKE to enable the workaround.
|
||||
|
||||
# EXECUTABLE FILE FORMAT
|
||||
#
|
||||
# Some uClibc/busybox combinations use different executable files formats from
|
||||
# ELF. This is configured during Linux kernel build. One common format is
|
||||
# the BLFT file format. Do not manually convert ELF binaries to BLTF using
|
||||
# elf2flt as that will create invalid binaries. Instead add -Wl,-elf2flt to
|
||||
# your flags (CFLAGS / LDFLAGS / USERCOMPILE)
|
||||
|
|
@ -0,0 +1,57 @@
|
|||
|
||||
Please read the documentation in docs or at https://libreswan.org/
|
||||
|
||||
Specific vendors/distribution build instructions available in packaging/
|
||||
|
||||
Build requirements
|
||||
------------------
|
||||
bison flex pkgconfig gcc make xmlto
|
||||
nss-devel nspr-devel libevent-devel
|
||||
|
||||
for systemd: pkgconfig hostname systemd-devel
|
||||
for pam/xauth: pam-devel
|
||||
for dnssec support: unbound-devel ldns-devel
|
||||
for FIPS support: fipscheck-devel
|
||||
for libcap-ng support: libcap-ng-devel
|
||||
for CRL fetching support: libcurl-devel
|
||||
for CRL ldap fetching support: openldap-devel
|
||||
for audit support: audit-libs-devel
|
||||
|
||||
Building userland
|
||||
-----------------
|
||||
|
||||
make all
|
||||
sudo make install
|
||||
|
||||
For a minimal install (no manpages) type:
|
||||
|
||||
make base
|
||||
sudo make install-base
|
||||
|
||||
The file Makefile.inc.local can be used to enable/disable features
|
||||
configured by mk/config.mk and mk/userland-cflags.mk
|
||||
|
||||
Optional building alternative KLIPS IPsec stack
|
||||
-----------------------------------------------
|
||||
|
||||
On Linux 2.6 or higher for the running kernel:
|
||||
|
||||
make module
|
||||
sudo make module_install
|
||||
|
||||
Build for a kernel different from the running kernel:
|
||||
|
||||
make KERNELSRC=//usr/src/kernel/linux-9.42 module
|
||||
|
||||
Building KLIPS kernel module for the old Linux 2.4 kernel
|
||||
|
||||
make module24
|
||||
sudo make minstall24
|
||||
|
||||
When using KLIPS with OCF:
|
||||
|
||||
make CONFIG_KLIPS_OCF=y MODULE_DEF_INCLUDE=$${LIBRESWANSRCDIR}/packaging/ocf/config-all.hmodules module module_install
|
||||
|
||||
When called in openwrt/packaging/libreswan/Makefile to build kmod-libreswan
|
||||
|
||||
make MODULE_DEFCONFIG=$${LIBRESWANSRCDIR}/packaging/openwrt/defconfig MODULE_DEF_INCLUDE=$${LIBRESWANSRCDIR}/packaging/openwrt/config-all.h module
|
||||
|
|
@ -0,0 +1,58 @@
|
|||
-----BEGIN PGP PUBLIC KEY BLOCK-----
|
||||
Version: GnuPG v1.4.13 (GNU/Linux)
|
||||
|
||||
mQINBFDjilcBEAChkfasfBKTzGys9DwgBsmDVsPConW60uyKnu16+wO1kIKMFWi6
|
||||
wGllwKUJmCBY2FSQHbOBy5eHPPT1ijJhYt4j7WU+YJVh5Ca5RE3trFt31FX0vzp+
|
||||
KMqdQ8HOofA7jO6bgyHUwOJ539YkqYj1jHKfrdRqOnzB9fFyEb7485sq1F8j/rHk
|
||||
cSar1Hd9QfGAZHxXqgncgHFobB/xXEGRJIi+4kNL5SYasbw9tfYUGPrUXVol1+pn
|
||||
tsG92736O5Qe5K+wH2nAS4hwPJ1Xr4XIKeNNwxQW25wWqn4mLa4Vly+PA2uSE7ZP
|
||||
RcxE3yBCaLFMlw4rLhFAzd6TeslQONZ+9K51yfBYm7m0vWM3Ixq8yuD8E49OkKr8
|
||||
QRMaA2g89NW3AuNLExiTE0zQzAs/g6eX8WZdeWCvKxhRTAUYkw0QTimFgv6LXIeS
|
||||
//5DOAAO9WwzlseTGmUgek3BbnnJJiGHVLBgnLaqWLOZ1Y8ON1uC8lQnbIeYbTQq
|
||||
EE5R0cbVLVXBJoKakBF8gwHF51HC2pSBYmHNZsSbjMuHpJWJM4fVldNWPNaqriKC
|
||||
OkL8QgvNoapgk20k1ajLl/ibv32k7QBKy3cTMtbQYPdreXcoZuMw38ysQcgFxPCs
|
||||
Zh92aaWW0ceWowkJ7CFnes2jdPcMSOYE37wodmV3/VV7cusmTD8wikyUdQARAQAB
|
||||
tCxMaWJyZXN3YW4gKFNpZ25pbmcgS2V5KSA8dGVhbUBsaWJyZXN3YW4ub3JnPokC
|
||||
OAQTAQIAIgUCUOOKVwIbAwYLCQgHAwIGFQgCCQoLBBYCAwECHgECF4AACgkQhf9L
|
||||
Q7MPxvkHyRAAgSq/QhdBurBaIjzqM4jZpaHEOURPlL38wHTBBeH4U5IZcwiPul9X
|
||||
Et1HqwHLDv89YjljHj76oOLt5xR14exgV0xWolZaLVpji3S6/NbCh37UMoWIBCSP
|
||||
j6/S6oAXxtX+oCI1lXmS4w60ZDDuYgVUrtAv77ODlQoPVf5TM0tU7Gb2Y3WB47DS
|
||||
XioIzwjFwJmtK3RzDRtF4oC2YFN3DBovVHmv6hbIt7NDNp7+NYRlx+wdi+XYFcNv
|
||||
+ZIARFkoc1Sr4HDk+lA2qx5jfvgZvabTn7OCTlCKwkSwO5sK0ICNcLmG9nb4ZNrU
|
||||
C2GXryTNQOMLcdvZAyBvxtgNzI7qqMAxeipsyCz5ypp5S3SwzHjqeCUJJ4pv7Ebn
|
||||
BnYIOgdLkq/WPsS6om7qwr3EdkR8iTZnuTi2Fejw7WnQP8dYLVXwG/90vNCU/HTE
|
||||
IYhal4ob7p0SsyLYF47U/iKl/b6ZErOcbq3YF0fMe8iusAtNLeIN4BLk9tpclGde
|
||||
weTPuB+MhRuDsLCF764ZB/R5v0CjWFVcBxnRXQbjlrm6dMlEXPFKjjV1fHL1HZhB
|
||||
GXopPmsw+NIf9sTSjcgNnLZGJFGGBsIxQD18AN6nzi2vtGRksB/FqLY7gIeGWaPu
|
||||
HlUI1qHdRLS7aus9nrS/RQTTUdCOsn1fRVozX2eVklAWgLuoz58oPhiJARwEEAEI
|
||||
AAYFAlDlHbkACgkQ5xgGprXMJ+Hc8Qf/Sd4NJMJifpU8hYET7IzMSgAdGZkkFV7/
|
||||
3/YCoEIVQS18xx+66L/TrUrAtJnlHLpmNUMA1wVFTtGJ/CRwFt3LsZYVM1jCwdRe
|
||||
AF492OHxEWXAboVnGRnGfJ3yhfCTd3XgRbthqBwR/8BSWCzs9Gy9YA5N6oceNf6q
|
||||
QkkLKk3YwdSNnW3b7o/AVdNcFbwkE+amNQ2mhWUtzzuvlsmgOrnCpUlq3djhnEKs
|
||||
pbl+T/apqvn7JRsOvuy/26kjoTbVrb7OpFmAjlIqbbxokaONFuDpqn/mtgG7Bk0r
|
||||
3Pv501mRItACslhaKPJ02oPufAmzBrphjzzhCYlR1TeEek++9qoHyLkCDQRQ44pX
|
||||
ARAA1wzfaN4nMg8vorcuOQrEH6NX/OMS+qCSIAixhsJt0RT4Ds3YMWhO04i81tjQ
|
||||
bovsh8sOPFkU8WfVwuh7Riox+lz7z+ZxePMLLO7Y80Tc5jYE6exuOx5Ft5Q9FWF+
|
||||
DanwpsUCvYE16G9fiRZlpBF5F5mWINnW59URLR29N8d+9GeeO6473aaKUFuo2ksN
|
||||
AueegzsW/cHiai6gHdrmTuJ8Ibg7P1TPkMsvvzJR0257Jp2CDKMwyzJh2dTzHiZU
|
||||
xTzH2qWrsfVA04EOXcC49hYkP7hDM731b1tt4cZaVlR7HHMGUe+zzA7eDW4/+0JT
|
||||
iCqYIndq/EsgZoYxE9rv1EksxWMyvCdlo6C3MYrjE8K5zOm926orkg1DABKDTfNe
|
||||
Am6c+siwdsMirOTe2QP5VSzRPDFe7aPDg8MNZ0tmww3+fyTDbeWlrv4jtmwa2BN9
|
||||
C6h0d20lekD+eyZ87pzPWOFdQZxCmFteAPfq0R9ZNXuQrkubasaUrm54hfNAHVMj
|
||||
4xfK1zmNFEQ+s2NLOPONzX/Uza/JHv9ZmqixJFABdNwMAUfKM9uO8pbu+aveMraW
|
||||
FBSQJDXqqZPF8qaiiTFXJeDXxD/d9CUfNrBozcpVbv2+BLKin5pKFPFRTNZX7mql
|
||||
9btmQ6FKRtiKP86XldO0UNCkx3SgXo84sdiDdE+1uBtCV3MAEQEAAYkCHwQYAQIA
|
||||
CQUCUOOKVwIbDAAKCRCF/0tDsw/G+SkfD/43VjVVcO+P6Aj7be/Vda9FzeCNGQU0
|
||||
GYCqdyZmXXGZUtlM8eLtVYcXHrw0O34f2eWNcQwYfiCsBfN4SSl8uevjyQZWCBo3
|
||||
NhkxJlNcqOBPYrnT6uehRW+nnpV9agX8SNGR3VoM1pq7Zwheucxk5nmDKXJOGbin
|
||||
SQF9gDOpFnAYpLeI0/0qq3EvLf3blkUklYopMFw/Gj3sQM/V7nsyPstxMbqbf5al
|
||||
MlbQld7dP4FkQDLsKzB/0QARD02kHZsSs4tDpDA5R4cHl2VoNP7d9ly4YZsuH/99
|
||||
DYSmJ57Tev6XTQ2/L4p+Tj9jEciQxyMpANh2XGL43WUuN/j24rqgwkyCzL8VA2I8
|
||||
R7M4BIXi2q4kb5kcBNR0Y2VjU8xk41IMr/N11IayKAJYDFctrUAGrSmzVWAJ+XZg
|
||||
NDQgyp0rM2rON4AKUko4dlF5qv6MMKVY+s2B3KFdIHQriydQTy7LTdGRjvoPnkaU
|
||||
yPe/v9OLIM/4SJg7Juxtw4p3q7PxQ2nm7aTEc1bIYeZSIFQZwk9+oXR1vG7sogIE
|
||||
ULY6u21/CSzeBK5sZauGt9zmHO0xjQt4xUZuF0mOkVAzHeroUQ+YSmQdjfGs9O/e
|
||||
tNyu53Pd8d9grmpRwiQ/jO2dv4/a90903MuvaDPqYD+PMMkqPlxBhwjOThu2DTYi
|
||||
fMUPyfgigsi0FQ==
|
||||
=X982
|
||||
-----END PGP PUBLIC KEY BLOCK-----
|
||||
|
|
@ -0,0 +1,28 @@
|
|||
Except for the exceptions listed below, this software is under the GNU
|
||||
General Public License (GPLv2+), see the file COPYING.
|
||||
|
||||
See the file CREDITS and docs/CREDITS.openswan and docs/CREDITS.freeswan
|
||||
for contribution details.
|
||||
|
||||
The linux/net/ipsec/radij.c code is derived from BSD 4.4lite code
|
||||
from sys/net/radix.c.
|
||||
|
||||
In addition to the terms set out under the GPLv2+, permission is granted to
|
||||
link the software against the libdes, md5c.c, and radij.c libraries just
|
||||
mentioned.
|
||||
|
||||
The following additional notes apply if you are NOT using CrytpoAPI:
|
||||
|
||||
The DES library is under a BSD style license, see
|
||||
linux/crypto/ciphers/des/COPYRIGHT.
|
||||
Note that this software has a advertising clause in it.
|
||||
|
||||
|
||||
The MD5 implementation is from RSADSI, so this package must include the
|
||||
following phrase:
|
||||
|
||||
"derived from the RSA Data Security, Inc. MD5 Message-Digest Algorithm".
|
||||
It is not under the GPL; see details in linux/net/ipsec/ipsec_md5c.c.
|
||||
|
||||
Code in lib/libswan/nss_copies.c is used under the Mozilla Public License
|
||||
Version 2.0. https://www.mozilla.org/MPL/2.0/
|
||||
|
|
@ -0,0 +1,656 @@
|
|||
# Libreswan master makefile
|
||||
#
|
||||
# Copyright (C) 1998-2002 Henry Spencer.
|
||||
# Copyright (C) 2003-2004 Xelerance Corporation
|
||||
# Copyright (C) 2017, Richard Guy Briggs <rgb@tricolour.ca>
|
||||
# Copyright (C) 2015-2018 Andrew Cagney
|
||||
#
|
||||
# This program is free software; you can redistribute it and/or modify it
|
||||
# under the terms of the GNU General Public License as published by the
|
||||
# Free Software Foundation; either version 2 of the License, or (at your
|
||||
# option) any later version. See <https://www.gnu.org/licenses/gpl2.txt>.
|
||||
#
|
||||
# This program is distributed in the hope that it will be useful, but
|
||||
# WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY
|
||||
# or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License
|
||||
# for more details.
|
||||
#
|
||||
|
||||
ifndef top_srcdir
|
||||
include mk/dirs.mk
|
||||
endif
|
||||
|
||||
LIBRESWANSRCDIR?=$(shell pwd)
|
||||
|
||||
include ${LIBRESWANSRCDIR}/Makefile.inc
|
||||
|
||||
SRCDIR?=$(shell pwd)/
|
||||
|
||||
# dummy default rule
|
||||
def help:
|
||||
@echo
|
||||
@echo "To build and install on a recent Linux kernel that has NETKEY:"
|
||||
@echo
|
||||
@echo " make all && sudo make install"
|
||||
@echo
|
||||
@echo "For a minimal install (no manpages) type:"
|
||||
@echo
|
||||
@echo " make base && sudo make install-base"
|
||||
@echo
|
||||
@echo "See the files INSTALL and README for more general information,"
|
||||
@echo "and details on how to build / install on KLIPS and other systems"
|
||||
@echo
|
||||
@echo "To build debian packages: make deb"
|
||||
@echo "To build fedora/rhel/centos rpms, see packaging/"
|
||||
@echo
|
||||
@false
|
||||
|
||||
.PHONY: def help
|
||||
|
||||
PATCHES=linux
|
||||
# where KLIPS goes in the kernel
|
||||
# note, some of the patches know the last part of this path
|
||||
KERNELKLIPS=$(KERNELSRC)/net/ipsec
|
||||
KERNELCRYPTODES=$(KERNELSRC)/crypto/ciphers/des
|
||||
KERNELLIBFREESWAN=$(KERNELSRC)/lib/libfreeswan
|
||||
KERNELLIBZLIB=$(KERNELSRC)/lib/zlib
|
||||
KERNELINCLUDE=$(KERNELSRC)/include
|
||||
|
||||
MAKEUTILS=packaging/utils
|
||||
ERRCHECK=${MAKEUTILS}/errcheck
|
||||
KVUTIL=${MAKEUTILS}/kernelversion
|
||||
KVSHORTUTIL=${MAKEUTILS}/kernelversion-short
|
||||
|
||||
SUBDIRS?=lib programs initsystems testing
|
||||
|
||||
TAGSFILES=$(wildcard include/*.h lib/lib*/*.[ch] programs/*/*.[ch] linux/include/*.h linux/include/libreswan/*.h linux/net/ipsec/*.[ch])
|
||||
|
||||
tags: $(TAGSFILES)
|
||||
@LC_ALL=C ctags $(CTAGSFLAGS) ${TAGSFILES}
|
||||
|
||||
cscope:
|
||||
@ls ${TAGSFILES} > cscope.files
|
||||
@cscope -b
|
||||
|
||||
TAGS: $(TAGSFILES)
|
||||
@LC_ALL=C etags $(ETAGSFLAGS) ${TAGSFILES}
|
||||
|
||||
.PHONY: dummy
|
||||
dummy:
|
||||
|
||||
|
||||
# Run regress stuff after the other check targets.
|
||||
.PHONY: regress
|
||||
check: regress
|
||||
regress: local-check recursive-check
|
||||
ifneq ($(strip(${REGRESSRESULTS})),)
|
||||
mkdir -p ${REGRESSRESULTS}
|
||||
-perl testing/utils/regress-summarize-results.pl ${REGRESSRESULTS}
|
||||
endif
|
||||
@echo "======== End of make check target. ========"
|
||||
|
||||
include ${LIBRESWANSRCDIR}/mk/subdirs.mk
|
||||
|
||||
# kernel details
|
||||
# what variant of our patches should we use, and where is it
|
||||
KERNELREL=$(shell ${KVSHORTUTIL} ${KERNELSRC}/Makefile)
|
||||
|
||||
# directories visited by all recursion
|
||||
|
||||
# declaration for make's benefit
|
||||
.PHONY: def insert kpatch patches _patches _patches2.4 \
|
||||
klipsdefaults programs man install \
|
||||
precheck verset confcheck kernel \
|
||||
module module24 module26 kinstall minstall minstall24 minstall26 \
|
||||
moduleclean mod24clean module24clean mod26clean module26clean \
|
||||
backup unpatch uninstall \
|
||||
check \
|
||||
|
||||
kpatch: unapplypatch applypatch klipsdefaults
|
||||
npatch: unapplynpatch applynpatch
|
||||
sarefpatch: unapplysarefpatch applysarefpatch
|
||||
|
||||
unapplypatch:
|
||||
@echo "info: making unapplypatch in `pwd` and KERNELSRC=\"${KERNELSRC}\";"
|
||||
-@if [ -f ${KERNELSRC}/libreswan.patch ]; then \
|
||||
echo Undoing previous patches; \
|
||||
cat ${KERNELSRC}/libreswan.patch | (cd ${KERNELSRC} && patch -p1 -R --force -E -z .preipsec --reverse --ignore-whitespace ); \
|
||||
fi
|
||||
|
||||
applypatch:
|
||||
@echo "info: Now performing forward patches in `pwd`";
|
||||
${MAKE} kernelpatch${KERNELREL} | tee ${KERNELSRC}/libreswan.patch | (cd ${KERNELSRC} && patch -p1 -b -z .preipsec --forward --ignore-whitespace )
|
||||
|
||||
unapplynpatch:
|
||||
@echo "info: making unapplynpatch (note the second N) in `pwd`";
|
||||
-@if [ -f ${KERNELSRC}/natt.patch ]; then \
|
||||
echo Undoing previous NAT patches; \
|
||||
cat ${KERNELSRC}/natt.patch | (cd ${KERNELSRC} && patch -p1 -R --force -E -z .preipsec --reverse --ignore-whitespace ); \
|
||||
fi
|
||||
|
||||
applynpatch:
|
||||
@echo "info: Now performing forward NAT patches in `pwd`";
|
||||
${MAKE} nattpatch${KERNELREL} | tee ${KERNELSRC}/natt.patch | (cd ${KERNELSRC} && patch -p1 -b -z .preipsec --forward --ignore-whitespace )
|
||||
|
||||
unapplysarefpatch:
|
||||
@echo "info: making unapplysarefpatch in `pwd`";
|
||||
-@if [ -f ${KERNELSRC}/saref.patch ]; then \
|
||||
echo Undoing previous saref patches; \
|
||||
cat ${KERNELSRC}/saref.patch | (cd ${KERNELSRC} && patch -p1 -R --force -E -z .preng --reverse --ignore-whitespace ); \
|
||||
fi
|
||||
|
||||
applysarefpatch:
|
||||
@echo "info: Now performing SAref patches in `pwd`";
|
||||
${MAKE} sarefpatch${KERNELREL} | tee ${KERNELSRC}/klipsng.patch | (cd ${KERNELSRC} && patch -p1 -b -z .preng --forward --ignore-whitespace )
|
||||
|
||||
# patch kernel
|
||||
PATCHER=packaging/utils/patcher
|
||||
|
||||
_patches:
|
||||
echo "===============" >>out.kpatch
|
||||
echo "`date` `cd $(KERNELSRC) ; pwd`" >>out.kpatch
|
||||
$(MAKE) __patches$(KERNELREL) >>out.kpatch
|
||||
|
||||
# Linux-2.4.0 version
|
||||
__patches2.4:
|
||||
@$(PATCHER) -v -c $(KERNELSRC) Documentation/Configure.help \
|
||||
'CONFIG_KLIPS' $(PATCHES)/Documentation/Configure.help.fs2_2.patch
|
||||
@$(PATCHER) -v $(KERNELSRC) net/Config.in \
|
||||
'CONFIG_KLIPS' $(PATCHES)/net/Config.in.fs2_4.patch
|
||||
@$(PATCHER) -v $(KERNELSRC) net/Makefile \
|
||||
'CONFIG_KLIPS' $(PATCHES)/net/Makefile.fs2_4.patch
|
||||
@$(PATCHER) -v $(KERNELSRC) net/ipv4/af_inet.c \
|
||||
'CONFIG_KLIPS' $(PATCHES)/net/ipv4/af_inet.c.fs2_4.patch
|
||||
@$(PATCHER) -v $(KERNELSRC) net/ipv4/udp.c \
|
||||
'CONFIG_KLIPS' $(PATCHES)/net/ipv4/udp.c.fs2_4.patch
|
||||
@$(PATCHER) -v $(KERNELSRC) include/net/sock.h \
|
||||
'CONFIG_KLIPS' $(PATCHES)/include/net/sock.h.fs2_4.patch
|
||||
# Removed patches, will unpatch automatically.
|
||||
@$(PATCHER) -v $(KERNELSRC) include/linux/proc_fs.h
|
||||
@$(PATCHER) -v $(KERNELSRC) net/core/dev.c
|
||||
@$(PATCHER) -v $(KERNELSRC) net/ipv4/protocol.c
|
||||
@$(PATCHER) -v $(KERNELSRC) drivers/net/Space.c
|
||||
@$(PATCHER) -v $(KERNELSRC) include/linux/netlink.h
|
||||
@$(PATCHER) -v $(KERNELSRC) net/netlink/af_netlink.c
|
||||
@$(PATCHER) -v $(KERNELSRC) net/netlink/netlink_dev.c
|
||||
@$(PATCHER) -v $(KERNELSRC) drivers/isdn/isdn_net.c
|
||||
|
||||
klipsdefaults:
|
||||
@KERNELDEFCONFIG=$(KERNELSRC)/arch/$(ARCH)/defconfig ; \
|
||||
KERNELCONFIG=$(KCFILE) ; \
|
||||
if ! egrep -q 'CONFIG_KLIPS' $$KERNELDEFCONFIG ; \
|
||||
then \
|
||||
set -x ; \
|
||||
cp -a $$KERNELDEFCONFIG $$KERNELDEFCONFIG.orig ; \
|
||||
chmod u+w $$KERNELDEFCONFIG ; \
|
||||
cat $$KERNELDEFCONFIG $(KERNELKLIPS)/defconfig \
|
||||
>$$KERNELDEFCONFIG.tmp ; \
|
||||
rm -f $$KERNELDEFCONFIG ; \
|
||||
cp -a $$KERNELDEFCONFIG.tmp $$KERNELDEFCONFIG ; \
|
||||
rm -f $$KERNELDEFCONFIG.tmp ; \
|
||||
fi ; \
|
||||
if ! egrep -q 'CONFIG_KLIPS' $$KERNELCONFIG ; \
|
||||
then \
|
||||
set -x ; \
|
||||
cp -a $$KERNELCONFIG $$KERNELCONFIG.orig ; \
|
||||
chmod u+w $$KERNELCONFIG ; \
|
||||
cat $$KERNELCONFIG $(KERNELKLIPS)/defconfig \
|
||||
>$$KERNELCONFIG.tmp ; \
|
||||
rm -f $$KERNELCONFIG ; \
|
||||
cp -a $$KERNELCONFIG.tmp $$KERNELCONFIG ; \
|
||||
rm -f $$KERNELCONFIG.tmp ; \
|
||||
fi
|
||||
|
||||
|
||||
|
||||
# programs
|
||||
|
||||
ABSOBJDIR:=$(shell mkdir -p ${OBJDIR}; cd ${OBJDIR} && pwd)
|
||||
OBJDIRTOP=${ABSOBJDIR}
|
||||
|
||||
# Recursive clean dealt with elsewhere.
|
||||
local-clean-base: moduleclean
|
||||
$(foreach file,$(RPMTMPDIR) $(RPMDEST) out.*build out.*install, \
|
||||
rm -rf $(file) ; ) # but leave out.kpatch
|
||||
|
||||
# Delete absolutely everything.
|
||||
#
|
||||
# Since "clean" is a recursive target and requires the existence of
|
||||
# $(OBJDIR), "distclean" does not depend on it. If it did, "make
|
||||
# distclean" would have the quirky behaviour of first creating
|
||||
# $(OBJDIR) only to then delete it.
|
||||
distclean: moduleclean module24clean module26clean clean-kvm-keys
|
||||
rm -f $(RPMTMPDIR) $(RPMDEST) out.*
|
||||
rm -rf testing/pluto/*/OUTPUT*
|
||||
rm -rf OBJ.* $(OBJDIR)
|
||||
rm -rf BACKUP
|
||||
|
||||
# proxies for major kernel make operations
|
||||
|
||||
# do-everything entries
|
||||
KINSERT_PRE=precheck verset insert
|
||||
PRE=precheck verset kpatch
|
||||
POST=confcheck programs kernel install
|
||||
MPOST=confcheck programs module install
|
||||
|
||||
# preliminaries
|
||||
precheck:
|
||||
@if test ! -d $(KERNELSRC) -a ! -L $(KERNELSRC) ; \
|
||||
then \
|
||||
echo '*** cannot find directory "$(KERNELSRC)"!!' ; \
|
||||
echo '*** may be necessary to add symlink to kernel source' ; \
|
||||
exit 1 ; \
|
||||
fi
|
||||
@if ! cd $(KERNELSRC) ; \
|
||||
then \
|
||||
echo '*** cannot "cd $(KERNELSRC)"!!' ; \
|
||||
echo '*** may be necessary to add symlink to kernel source' ; \
|
||||
exit 1 ; \
|
||||
fi
|
||||
@if test ! -f $(KCFILE) ; \
|
||||
then \
|
||||
echo '*** cannot find "$(KCFILE)"!!' ; \
|
||||
echo '*** perhaps kernel has never been configured?' ; \
|
||||
echo '*** please do that first; the results are necessary.' ; \
|
||||
exit 1 ; \
|
||||
fi
|
||||
@if test ! -f $(VERFILE) ; \
|
||||
then \
|
||||
echo '*** cannot find "$(VERFILE)"!!' ; \
|
||||
echo '*** perhaps kernel has never been compiled?' ; \
|
||||
echo '*** please do that first; the results are necessary.' ; \
|
||||
exit 1 ; \
|
||||
fi
|
||||
|
||||
# configuring (exit statuses disregarded, something fishy here sometimes)
|
||||
xcf:
|
||||
-cd $(KERNELSRC) ; $(MAKE) $(KERNMAKEOPTS) xconfig
|
||||
mcf:
|
||||
-cd $(KERNELSRC) ; $(MAKE) $(KERNMAKEOPTS) menuconfig
|
||||
pcf:
|
||||
-cd $(KERNELSRC) ; $(MAKE) $(KERNMAKEOPTS) config
|
||||
|
||||
ocf:
|
||||
-cd $(KERNELSRC) ; $(MAKE) $(KERNMAKEOPTS) oldconfig
|
||||
|
||||
rcf:
|
||||
cd $(KERNELSRC) ; $(MAKE) $(KERNMAKEOPTS) ${NONINTCONFIG} </dev/null
|
||||
cd $(KERNELSRC) ; $(MAKE) $(KERNMAKEOPTS) dep >/dev/null
|
||||
|
||||
kclean:
|
||||
-cd $(KERNELSRC) ; $(MAKE) $(KERNMAKEOPTS) clean
|
||||
|
||||
confcheck:
|
||||
@if test ! -f $(KCFILE) ; \
|
||||
then echo '*** no kernel configuration file written!!' ; exit 1 ; \
|
||||
fi
|
||||
@if ! egrep -q '^CONFIG_KLIPS=[my]' $(KCFILE) ; \
|
||||
then echo '*** IPsec not in kernel config ($(KCFILE))!!' ; exit 1 ; \
|
||||
fi
|
||||
@if ! egrep -q 'CONFIG_KLIPS[ ]+1' $(ACFILE) && \
|
||||
! egrep -q 'CONFIG_KLIPS_MODULE[ ]+1' $(ACFILE) ; \
|
||||
then echo '*** IPsec in kernel config ($(KCFILE)),' ; \
|
||||
echo '*** but not in config header file ($(ACFILE))!!' ; \
|
||||
exit 1 ; \
|
||||
fi
|
||||
@if egrep -q '^CONFIG_KLIPS=m' $(KCFILE) && \
|
||||
! egrep -q '^CONFIG_MODULES=y' $(KCFILE) ; \
|
||||
then echo '*** IPsec configured as module in kernel with no module support!!' ; exit 1 ; \
|
||||
fi
|
||||
@if ! egrep -q 'CONFIG_KLIPS_AH[ ]+1' $(ACFILE) && \
|
||||
! egrep -q 'CONFIG_KLIPS_ESP[ ]+1' $(ACFILE) ; \
|
||||
then echo '*** IPsec configuration must include AH or ESP!!' ; exit 1 ; \
|
||||
fi
|
||||
|
||||
# kernel building, with error checks
|
||||
kernel:
|
||||
rm -f out.kbuild out.kinstall
|
||||
# undocumented kernel folklore: clean BEFORE dep.
|
||||
# we run make dep separately, because there is no point in running ERRCHECK
|
||||
# on the make dep output.
|
||||
# see LKML thread "clean before or after dep?"
|
||||
( cd $(KERNELSRC) ; $(MAKE) $(KERNMAKEOPTS) $(KERNCLEAN) $(KERNDEP) )
|
||||
( cd $(KERNELSRC) ; $(MAKE) $(KERNMAKEOPTS) $(KERNEL) ) 2>&1 | tee out.kbuild
|
||||
@if egrep -q '^CONFIG_MODULES=y' $(KCFILE) ; \
|
||||
then set -x ; \
|
||||
( cd $(KERNELSRC) ; \
|
||||
$(MAKE) $(KERNMAKEOPTS) modules 2>&1 ) | tee -a out.kbuild ; \
|
||||
fi
|
||||
${ERRCHECK} out.kbuild
|
||||
|
||||
# module-only building, with error checks
|
||||
ifneq ($(strip $(MOD24BUILDDIR)),)
|
||||
${MOD24BUILDDIR}/Makefile : ${LIBRESWANSRCDIR}/packaging/makefiles/module24.make
|
||||
mkdir -p ${MOD24BUILDDIR}
|
||||
cp ${LIBRESWANSRCDIR}/packaging/makefiles/module24.make ${MOD24BUILDDIR}/Makefile
|
||||
|
||||
module:
|
||||
@if [ -f ${KERNELSRC}/README.libreswan-2 ] ; then \
|
||||
echo "WARNING: Kernel source ${KERNELSRC} has already been patched with libreswan-2, out of tree build might fail!"; \
|
||||
fi;
|
||||
@if [ -f ${KERNELSRC}/README.openswan ] ; then \
|
||||
echo "WARNING: Kernel source ${KERNELSRC} has already been patched with openswan, out of tree build might fail!"; \
|
||||
fi;
|
||||
@if [ -f ${KERNELSRC}/README.openswan-2 ] ; then \
|
||||
echo "WARNING: Kernel source ${KERNELSRC} has already been patched with openswan-2, out of tree build might fail!"; \
|
||||
fi;
|
||||
@if [ -f ${KERNELSRC}/README.freeswan ] ; then \
|
||||
echo "ERROR: Kernel source ${KERNELSRC} has already been patched with freeswan, out of tree build will fail!"; \
|
||||
fi;
|
||||
@if [ -f ${KERNELSRC}/Rules.make ] ; then \
|
||||
echo "Building module for a 2.4 kernel"; ${MAKE} module24 ; \
|
||||
else echo "Building module for a 2.6 kernel"; ${MAKE} module26; \
|
||||
fi;
|
||||
|
||||
modclean moduleclean:
|
||||
@if [ -f ${KERNELSRC}/Rules.make ] ; then \
|
||||
echo "Cleaning module for a 2.4 kernel"; ${MAKE} module24clean ; \
|
||||
else echo "Cleaning module for a 2.6 kernel"; ${MAKE} module26clean; \
|
||||
fi;
|
||||
|
||||
module24:
|
||||
@if [ ! -f ${KERNELSRC}/Rules.make ] ; then \
|
||||
echo "Warning: Building for a 2.4 kernel in what looks like a 2.6 tree"; \
|
||||
fi ; \
|
||||
${MAKE} ${MOD24BUILDDIR}/Makefile
|
||||
${MAKE} -C ${MOD24BUILDDIR} LIBRESWANSRCDIR=${LIBRESWANSRCDIR} ARCH=${ARCH} V=${V} ${MODULE_FLAGS} MODULE_DEF_INCLUDE=${MODULE_DEF_INCLUDE} TOPDIR=${KERNELSRC} -f Makefile ipsec.o
|
||||
@echo
|
||||
@echo '========================================================='
|
||||
@echo
|
||||
@echo 'KLIPS24 module built successfully. '
|
||||
@echo ipsec.o is in ${MOD24BUILDDIR}
|
||||
@echo
|
||||
@(cd ${MOD24BUILDDIR}; ls -l ipsec.o)
|
||||
@(cd ${MOD24BUILDDIR}; size ipsec.o)
|
||||
@echo
|
||||
@echo 'use make minstall as root to install it'
|
||||
@echo
|
||||
@echo '========================================================='
|
||||
@echo
|
||||
|
||||
mod24clean module24clean:
|
||||
rm -rf ${MOD24BUILDDIR}
|
||||
|
||||
#autoodetect 2.4 and 2.6
|
||||
module_install minstall install-module:
|
||||
@if [ -f $(KERNELSRC)/Rules.make ] ; then \
|
||||
$(MAKE) minstall24 ; \
|
||||
else \
|
||||
$(MAKE) minstall26 ; \
|
||||
fi;
|
||||
|
||||
# Extract the value of MODLIB from the output of $(MAKE). Also hide
|
||||
# the sup-process $(MAKE) so that GNU Make doesn't always invoke the
|
||||
# target ("make -n" ignored).
|
||||
#
|
||||
# If $(MAKE) directly appears in a target (for instance in minstall26)
|
||||
# then GNU Make will assume that it is a recursive make invocation and
|
||||
# invoke the target regardless of -n.
|
||||
#
|
||||
# XXX: minstall24 should also use this.
|
||||
|
||||
osmodlib-from-make = \
|
||||
OSMODLIB=$$($(MAKE) $(1) 2>/dev/null | sed -n -e 's/^MODLIB[ :=]*\([^;]*\).*/\1/p' | head -1) ; \
|
||||
test -z "$$OSMODLIB" || echo "OSMODLIB=$$OSMODLIB ($(MAKE) $(1))"
|
||||
|
||||
# module-only install, with error checks
|
||||
minstall24:
|
||||
( OSMODLIB=`${MAKE} -C $(KERNELSRC) -p dummy | ( sed -n -e '/^MODLIB/p' -e '/^MODLIB/q' ; cat > /dev/null ) | sed -e 's/^MODLIB[ :=]*\([^;]*\).*/\1/'` ; \
|
||||
if [ -z "$$OSMODLIB" ] ; then \
|
||||
OSMODLIB=`${MAKE} -C $(KERNELSRC) -n -p modules_install | ( sed -n -e '/^MODLIB/p' -e '/^MODLIB/q' ; cat > /dev/null ) | sed -e 's/^MODLIB[ :=]*\([^;]*\).*/\1/'` ; \
|
||||
fi ; \
|
||||
if [ -z "$$OSMODLIB" ] ; then \
|
||||
echo "No known place to install module. Aborting." ; \
|
||||
exit 93 ; \
|
||||
fi ; \
|
||||
set -x ; \
|
||||
mkdir -p $$OSMODLIB/kernel/$(OSMOD_DESTDIR) ; \
|
||||
cp $(MOD24BUILDDIR)/ipsec.o $$OSMODLIB/kernel/$(OSMOD_DESTDIR) ; \
|
||||
if [ -f /sbin/depmod ] ; then /sbin/depmod -a ; fi; \
|
||||
if [ -n "$(OSMOD_DESTDIR)" ] ; then \
|
||||
mkdir -p $$OSMODLIB/kernel/$(OSMOD_DESTDIR) ; \
|
||||
if [ -f $$OSMODLIB/kernel/ipsec.o -a -f $$OSMODLIB/kernel/$(OSMOD_DESTDIR)/ipsec.o ] ; then \
|
||||
echo "WARNING: two ipsec.o modules found in $$OSMODLIB/kernel:" ; \
|
||||
ls -l $$OSMODLIB/kernel/ipsec.o $$OSMODLIB/kernel/$(OSMOD_DESTDIR)/ipsec.o ; \
|
||||
exit 1; \
|
||||
fi ; \
|
||||
fi ; \
|
||||
set -x ) ;
|
||||
|
||||
|
||||
else
|
||||
module:
|
||||
echo 'Building in place is no longer supported. Please set MOD24BUILDDIR='
|
||||
exit 1
|
||||
|
||||
endif
|
||||
|
||||
# module-only building, with error checks
|
||||
ifneq ($(strip $(MODBUILDDIR)),)
|
||||
${MODBUILDDIR}/Makefile : ${LIBRESWANSRCDIR}/packaging/makefiles/module.make
|
||||
mkdir -p ${MODBUILDDIR}
|
||||
echo ln -s -f ${LIBRESWANSRCDIR}/linux/net/ipsec/des/*.S ${MODBUILDDIR}
|
||||
(rm -f ${MODBUILDDIR}/des; mkdir -p ${MODBUILDDIR}/des && cd ${MODBUILDDIR}/des && ln -s -f ${LIBRESWANSRCDIR}/linux/net/ipsec/des/* . && ln -s -f Makefile.fs2_6 Makefile)
|
||||
(rm -f ${MODBUILDDIR}/aes; mkdir -p ${MODBUILDDIR}/aes && cd ${MODBUILDDIR}/aes && ln -s -f ${LIBRESWANSRCDIR}/linux/net/ipsec/aes/* . && ln -s -f Makefile.fs2_6 Makefile)
|
||||
mkdir -p ${MODBUILDDIR}/aes
|
||||
cp ${LIBRESWANSRCDIR}/packaging/makefiles/module.make ${MODBUILDDIR}/Makefile
|
||||
ln -s -f ${LIBRESWANSRCDIR}/linux/net/ipsec/match*.S ${MODBUILDDIR}
|
||||
|
||||
module26:
|
||||
@if [ -f ${KERNELSRC}/Rules.make ] ; then \ echo "Warning: Building for a 2.6+ kernel in what looks like a 2.4 tree"; \
|
||||
fi ; \
|
||||
${MAKE} ${MODBUILDDIR}/Makefile
|
||||
${MAKE} -C ${KERNELSRC} ${KERNELBUILDMFLAGS} BUILDDIR=${MODBUILDDIR} SUBDIRS=${MODBUILDDIR} INITSYSTEM=$(INITSYSTEM) MODULE_DEF_INCLUDE=${MODULE_DEF_INCLUDE} MODULE_DEFCONFIG=${MODULE_DEFCONFIG} MODULE_EXTRA_INCLUDE=${MODULE_EXTRA_INCLUDE} ARCH=${ARCH} V=${V} modules
|
||||
@echo
|
||||
@echo '========================================================='
|
||||
@echo
|
||||
@echo 'KLIPS module built successfully. '
|
||||
@echo ipsec.ko is in ${MODBUILDDIR}
|
||||
@echo
|
||||
@(cd ${MODBUILDDIR}; ls -l ipsec.ko)
|
||||
@(cd ${MODBUILDDIR}; size ipsec.ko)
|
||||
@echo
|
||||
@echo 'use make minstall as root to install it'
|
||||
@echo
|
||||
@echo '========================================================='
|
||||
@echo
|
||||
|
||||
mod26clean module26clean:
|
||||
rm -rf ${MODBUILDDIR}
|
||||
|
||||
# module-only install, with error checks
|
||||
minstall26:
|
||||
$(call osmodlib-from-make,-C $(KERNELSRC) -p help) ; \
|
||||
if [ -z "$$OSMODLIB" ] ; then \
|
||||
$(call osmodlib-from-make,-C $(KERNELSRC) -n -p modules_install) ; \
|
||||
fi ; \
|
||||
if [ -z "$$OSMODLIB" ] ; then \
|
||||
echo "No known place to install module. Aborting." ; \
|
||||
exit 93 ; \
|
||||
fi ; \
|
||||
set -x ; \
|
||||
mkdir -p $$OSMODLIB/kernel/$(OSMOD_DESTDIR) ; \
|
||||
cp $(MODBUILDDIR)/ipsec.ko $$OSMODLIB/kernel/$(OSMOD_DESTDIR) ; \
|
||||
if [ -f /sbin/depmod ] ; then \
|
||||
/sbin/depmod -a ; \
|
||||
fi ; \
|
||||
if [ -n "$(OSMOD_DESTDIR)" ] ; then \
|
||||
mkdir -p $$OSMODLIB/kernel/$(OSMOD_DESTDIR) ; \
|
||||
if [ -f $$OSMODLIB/kernel/ipsec.ko -a -f $$OSMODLIB/kernel/$(OSMOD_DESTDIR)/ipsec.ko ] ; then \
|
||||
echo "WARNING: two ipsec.ko modules found in $$OSMODLIB/kernel:" ; \
|
||||
ls -l $$OSMODLIB/kernel/ipsec.ko $$OSMODLIB/kernel/$(OSMOD_DESTDIR)/ipsec.ko ; \
|
||||
exit 1; \
|
||||
fi ; \
|
||||
fi
|
||||
|
||||
|
||||
else
|
||||
module26:
|
||||
echo 'Building in place is no longer supported. Please set MODBUILDDIR='
|
||||
exit 1
|
||||
|
||||
endif
|
||||
|
||||
# kernel install, with error checks
|
||||
kinstall:
|
||||
rm -f out.kinstall
|
||||
>out.kinstall
|
||||
# undocumented kernel folklore: modules_install must precede install (observed on RHL8.0)
|
||||
@if egrep -q '^CONFIG_MODULES=y' $(KCFILE) ; \
|
||||
then set -x ; \
|
||||
( cd $(KERNELSRC) ; \
|
||||
$(MAKE) $(KERNMAKEOPTS) modules_install 2>&1 ) | tee -a out.kinstall ; \
|
||||
fi
|
||||
( cd $(KERNELSRC) ; $(MAKE) $(KERNMAKEOPTS) install ) 2>&1 | tee -a out.kinstall
|
||||
${ERRCHECK} out.kinstall
|
||||
|
||||
kernelpatch3 kernelpatch3.5 kernelpatch2.6 kernelpatch:
|
||||
packaging/utils/kernelpatch 2.6
|
||||
|
||||
kernelpatch2.4:
|
||||
packaging/utils/kernelpatch 2.4
|
||||
|
||||
nattpatch:
|
||||
if [ -f ${KERNELSRC}/Makefile ]; then \
|
||||
${MAKE} nattpatch${KERNELREL}; \
|
||||
else echo "Cannot determine Linux kernel version. Perhaps you need to set KERNELSRC? (eg: export KERNELSRC=/usr/src/linux-`uname -r`/)"; exit 1; \
|
||||
fi;
|
||||
|
||||
sarefpatch2.6:
|
||||
#cat patches/kernel/2.6.38/0001-SAREF-add-support-for-SA-selection-through-sendmsg.patch
|
||||
#packaging/utils/sarefpatch 2.6
|
||||
echo ""
|
||||
|
||||
nattpatch2.6:
|
||||
packaging/utils/nattpatch 2.6
|
||||
|
||||
nattpatch2.4:
|
||||
packaging/utils/nattpatch 2.4
|
||||
|
||||
nattupdate:
|
||||
(cd UMLPOOL && diff -u plain26/net/ipv4/udp.c.orig plain26/net/ipv4/udp.c; exit 0) >nat-t/net/ipv4/udp.c.os2_6.patch
|
||||
|
||||
# take all the patches out of the kernel
|
||||
# (Note, a couple of files are modified by non-patch means; they are
|
||||
# included in "make backup".)
|
||||
unpatch:
|
||||
@echo \"make unpatch\" is obsolete. See make unapplypatch.
|
||||
exit 1
|
||||
|
||||
_unpatch:
|
||||
for f in `find $(KERNELSRC)/. -name '*.preipsec' -print` ; \
|
||||
do \
|
||||
echo "restoring $$f:" ; \
|
||||
dir=`dirname $$f` ; \
|
||||
core=`basename $$f .preipsec` ; \
|
||||
cd $$dir ; \
|
||||
mv -f $$core.preipsec $$core ; \
|
||||
rm -f $$core.wipsec $$core.ipsecmd5 ; \
|
||||
done
|
||||
|
||||
# at the moment there is no difference between snapshot and release build
|
||||
snapready: buildready
|
||||
relready: buildready
|
||||
ready: devready
|
||||
|
||||
# set up for build
|
||||
buildready:
|
||||
rm -f dtrmakefile cvs.datemark
|
||||
# obsolete cd doc ; $(MAKE) -s
|
||||
|
||||
rpm:
|
||||
@echo To build an rpm, use: rpmbuild -ba packaging/XXX/libreswan.spec
|
||||
@echo where XXX is your rpm based vendor
|
||||
rpmbuild -bs packaging/fedora/libreswan.spec
|
||||
|
||||
tarpkg:
|
||||
@echo "Generating tar.gz package to install"
|
||||
@rm -rf /var/tmp/libreswan-${USER}
|
||||
@make DESTDIR=/var/tmp/libreswan-${USER} programs install
|
||||
@rm /var/tmp/libreswan-${USER}/etc/ipsec.conf
|
||||
@(cd /var/tmp/libreswan-${USER} && tar czf - . ) >libreswan-${IPSECVERSION}.tgz
|
||||
@ls -l libreswan-${IPSECVERSION}.tgz
|
||||
@rm -rf /var/tmp/libreswan-${USER}
|
||||
|
||||
|
||||
env:
|
||||
@env | sed -e "s/'/'\\\\''/g" -e "s/\([^=]*\)=\(.*\)/\1='\2'/"
|
||||
|
||||
#
|
||||
# A target that does nothing intesting is sometimes interesting...
|
||||
war:
|
||||
@echo "Not Love?"
|
||||
|
||||
showversion:
|
||||
@echo ${IPSECVERSION} | sed "s/^v//"
|
||||
showdebversion:
|
||||
@echo ${IPSECVERSION} | sed "s/^v//" | sed -e "s/\([0-9]\{1,3\}\)\.\([0-9]\{1,3\}\)\(.*\)/\1.\2~\3/" | sed "s/~-/~/"
|
||||
showrpmversion:
|
||||
@echo ${IPSECVERSION} | sed "s/^v//" | sed -e "s/^v//;s/\([0-9]\{1,3\}\)\.\([0-9]\{1,3\}\)\(.*\)/\1.\2_\3/;s/-/_/g;s/__/_/g"
|
||||
showrpmrelease:
|
||||
@echo ${IPSECVERSION} | sed "s/^v//" | sed "s/^[^-]*-\(.*\)/\1/"
|
||||
showobjdir:
|
||||
@echo $(OBJDIR)
|
||||
|
||||
# these need to move elsewhere and get fixed not to use root
|
||||
|
||||
deb:
|
||||
cp -r packaging/debian .
|
||||
grep "IPSECBASEVERSION" debian/changelog && \
|
||||
sed -i "s/@IPSECBASEVERSION@/`make -s showdebversion`/g" debian/changelog || \
|
||||
echo "missing IPSECBASEVERSION in debian/changelog. This is not git repository?"
|
||||
debuild -i -us -uc -b
|
||||
rm -fr debian
|
||||
#debuild -S -sa
|
||||
@echo "to build optional KLIPS kernel module, run make deb-klips"
|
||||
|
||||
deb-klips:
|
||||
sudo module-assistant prepare -u .
|
||||
sudo dpkg -i ../libreswan-modules-source_`make -s showdebversion`_all.deb
|
||||
sudo module-assistant -u . prepare
|
||||
sudo module-assistant -u . build libreswan
|
||||
|
||||
|
||||
release:
|
||||
packaging/utils/makerelease
|
||||
|
||||
local-install:
|
||||
@if test -z "$(DESTDIR)" -a -x /usr/sbin/selinuxenabled -a $(PUBDIR) != "$(DESTDIR)/usr/sbin" ; then \
|
||||
if /usr/sbin/selinuxenabled ; then \
|
||||
echo -e "\n************************** WARNING ***********************************" ; \
|
||||
echo "SElinux is present on this system and the prefix path is not /usr." ; \
|
||||
echo "This can cause software failures if selinux is running in Enforcing mode"; \
|
||||
echo -e "unless selinux policies are updated manually to allow this.\n" ; \
|
||||
echo "The following commands fix a common issue of /usr/local/ being mislabeled"; \
|
||||
echo " restorecon /usr/local/sbin -Rv"; \
|
||||
echo " restorecon /usr/local/libexec/ipsec -Rv"; \
|
||||
if test -x /usr/sbin/getenforce ; then \
|
||||
echo -e "\nSElinux is currently running in `/usr/sbin/getenforce` mode" ; \
|
||||
fi ; \
|
||||
echo -e "**********************************************************************\n" ; \
|
||||
fi \
|
||||
fi
|
||||
@if test ! -f $(DESTDIR)/etc/pam.d/pluto ; then \
|
||||
mkdir -p $(DESTDIR)/etc/pam.d/ ; \
|
||||
$(INSTALL) $(INSTCONFFLAGS) pam.d/pluto $(DESTDIR)/etc/pam.d/pluto ; \
|
||||
else \
|
||||
echo -e "\n************************** WARNING ***********************************" ; \
|
||||
echo "We are not installing a new copy of the pam.d/pluto file, as one" ; \
|
||||
echo "was already present. You may wish to update it yourself if desired." ; \
|
||||
echo -e "**********************************************************************\n" ; \
|
||||
fi
|
||||
|
||||
# Test only target (run by swan-install) that generates FIPS .*.hmac
|
||||
# file for pluto that will be verified by fipscheck.
|
||||
#
|
||||
# (should really use fipshmac -d /usr/lib64/fipscheck but then
|
||||
# we need to hassle with multilib)
|
||||
# Without this fipscheck (run in FIPS mode) will fail.
|
||||
|
||||
.PHONY: install-fipshmac
|
||||
install-fipshmac:
|
||||
fipshmac $(LIBEXECDIR)/pluto
|
||||
|
||||
include ${LIBRESWANSRCDIR}/mk/docker-targets.mk
|
||||
include ${LIBRESWANSRCDIR}/mk/kvm-targets.mk
|
||||
include ${LIBRESWANSRCDIR}/mk/web-targets.mk
|
||||
|
|
@ -0,0 +1,2 @@
|
|||
# For compatibility, new code should include mk/config.mk directly.
|
||||
include ${LIBRESWANSRCDIR}/mk/config.mk
|
||||
|
|
@ -0,0 +1,2 @@
|
|||
# For compatibility, new code should include mk/version.mk directly.
|
||||
include ${LIBRESWANSRCDIR}/mk/version.mk
|
||||
|
|
@ -0,0 +1,149 @@
|
|||
#########################################################################
|
||||
# KLIPS Libreswan 3.X Release Notes
|
||||
#########################################################################
|
||||
|
||||
KLIPS is an alternative IPsec stack for the Linux kernel. It features:
|
||||
|
||||
- ipsecX devices for easy firewalling and tcpdumping
|
||||
- OCF support (crypto hardware offload) with many hardware drivers
|
||||
- SAref tracking for IPsec transport mode connections with NAT.
|
||||
- First+Last packet caching
|
||||
- Extensive debugging output (enabled via ipsec klipsdebug)
|
||||
- Native AES/3DES and MD5/SHA1 support as well as some CryptoAPI support
|
||||
|
||||
#########################################################################
|
||||
# REQUIREMENTS
|
||||
#########################################################################
|
||||
|
||||
A recent Linux distribution based on either Kernel 2.4.x, 2.6.x or 3.x,
|
||||
with the required tools to compile kernel modules.
|
||||
|
||||
#########################################################################
|
||||
# Compiling KLIPS
|
||||
#########################################################################
|
||||
|
||||
make module
|
||||
sudo make module_install
|
||||
|
||||
This builds a module against the running kernel. It is the equivalent of
|
||||
running:
|
||||
|
||||
make KERNELSRC=/lib/modules/`uname -r`/build module
|
||||
sudo make KERNELSRC=/lib/modules/`uname -r`/build module_install
|
||||
|
||||
To compile a module for another kernel, one can set KERNELSRC to point to
|
||||
directory with kernel headers or a full kernel source tree (eg /usr/src/kernels/)
|
||||
|
||||
#########################################################################
|
||||
# NAT TRAVERSAL
|
||||
#########################################################################
|
||||
|
||||
For Linux 2.6 Kernels before 2.6.23, including 2.4 linux systems, the kernel
|
||||
requires patching if NAT-T support is required. The full kernel source is
|
||||
required as some of the actual kernel source files need to be patched.
|
||||
|
||||
See your distribution documentation on how to build and install a new kernel
|
||||
|
||||
Add NAT-T support (if required).
|
||||
|
||||
From the Libreswan source directory:
|
||||
|
||||
make KERNELSRC=/usr/src/linux nattpatch | patch -d /usr/src/linux -p1
|
||||
|
||||
#########################################################################
|
||||
# SAref tracking support
|
||||
#########################################################################
|
||||
|
||||
|
||||
Premade patches for some distributions kernels can be found
|
||||
in patches/kernel/ directory of the libreswan source directory. If there is
|
||||
no patch for your exact kernel version, pick the version of the patch that matches
|
||||
your kernel closest - but don't pick a higher version than the kernel you have.
|
||||
|
||||
Documentation on SAref/MAST can be found in docs/HACKING/Mast* and
|
||||
doc/klips/mast.xml. To understand what SAref tracking does, see
|
||||
doc/ipsecsaref.png and the overlapip= entry in the ipsec.conf man page.
|
||||
|
||||
#########################################################################
|
||||
# OCF support
|
||||
#########################################################################
|
||||
|
||||
For OCF HW offloading support, you need a kernel that has support for an OCF
|
||||
kernel module, or has been patched with OCF support.
|
||||
See: http://ocf-linux.sourceforge.net/ for more details.
|
||||
|
||||
Compile a module with MODULE_DEFCONFIG= set to packaging/ocf/config-all.h, eg:
|
||||
|
||||
make module MODULE_DEFCONFIG=/opt/build/libreswan/packaging/ocf/config-all.h
|
||||
sudo make module_install
|
||||
|
||||
To test if KLIPS is properly compiled:
|
||||
|
||||
modprobe ocf
|
||||
modprobe ipsec
|
||||
dmesg
|
||||
|
||||
packaging/ocf/config-all.h can be modified to enable specific hardware crypto
|
||||
processors. This usually requires vendor source code to compile. The "software
|
||||
module" works with the NETKEY/XFRM stack as well and can accelerate NETKEY/XFRM
|
||||
over multiple CPU's. The kernel module ocf_bench can be used for benchmarking.
|
||||
The ocf_bench module is designed to "fail" loading into the kernel. A benchmark
|
||||
can be done using:
|
||||
|
||||
modprobe ocf_bench
|
||||
dmesg
|
||||
|
||||
#########################################################################
|
||||
# SUPPORT
|
||||
#########################################################################
|
||||
|
||||
Mailing Lists:
|
||||
|
||||
https://lists.libreswan.org is home of the mailing lists
|
||||
|
||||
Wiki:
|
||||
|
||||
https://libreswan.org is home to the Libreswan WIKI. It has the most
|
||||
up to date documentation, interop guides and other related information.
|
||||
|
||||
IRC:
|
||||
|
||||
Libreswan developers and users can be found on IRC, on #swan
|
||||
irc.freenode.net.
|
||||
|
||||
#########################################################################
|
||||
# BUGS
|
||||
#########################################################################
|
||||
|
||||
Bugs with the package can be filed into our bug tracking system, at
|
||||
https://bugs.libreswan.org
|
||||
|
||||
#########################################################################
|
||||
# SECURITY HOLES
|
||||
#########################################################################
|
||||
|
||||
All security vulnerabilities found that require public disclosure will
|
||||
receive proper CVE tracking numbers (see http://mitre.org/) and co-ordinated
|
||||
via the vendor-sec (or successor) mailing list. A complete list of known
|
||||
security vulnerabilities is available at: https://www.libreswan.org/security/
|
||||
|
||||
#########################################################################
|
||||
# DEVELOPMENT
|
||||
#########################################################################
|
||||
|
||||
Those interested in the development, patches, beta releases of Libreswan
|
||||
can join the development mailing list (http://lists.libreswan.org -
|
||||
dev@lists.libreswan.org) or join the development team on IRC in #swan
|
||||
on irc.freenode.net
|
||||
|
||||
For those who want to track things a bit more closely, the
|
||||
commits@lists.libreswan.org mailinglist will mail all the commit messages.
|
||||
|
||||
#########################################################################
|
||||
# DOCUMENTATION
|
||||
#########################################################################
|
||||
|
||||
The most up to date docs are in the man pages and at https://libreswan.org/
|
||||
|
||||
The bulk of this software is under the GNU General Public License; see
|
||||
LICENSE. Some parts of it are not; see CREDITS for the details.
|
||||
|
|
@ -0,0 +1,182 @@
|
|||
# Libreswan
|
||||
The Libreswan Project https://libreswan.org/
|
||||
|
||||
Libreswan is an IPsec implementation for Linux. It has support for most
|
||||
of the extensions (RFC + IETF drafts) related to IPsec, including
|
||||
IKEv2, X.509 Digital Certificates, NAT Traversal, and many others.
|
||||
Libreswan uses the native Linux IPsec stack (NETKEY/XFRM) per default.
|
||||
For more information about the alternative Libreswan kernel IPsec stack,
|
||||
see README.KLIPS.
|
||||
|
||||
Libreswan was forked from Openswan 2.6.38, which was forked from
|
||||
FreeS/WAN 2.04. See the CREDITS files for contributor acknowledgments.
|
||||
|
||||
It can be downloaded from:
|
||||
|
||||
https://download.libreswan.org/
|
||||
|
||||
A Git repository is available at:
|
||||
|
||||
https://github.com/libreswan/libreswan/
|
||||
|
||||
## License
|
||||
The bulk of libreswan is licensed under the GNU General Public License
|
||||
version 2; see the LICENSE and CREDIT.* files. Some smaller parts have
|
||||
a different license.
|
||||
|
||||
## Requirements
|
||||
Recent Linux distributions based on kernel 2.x, 3.x or 4.x
|
||||
are supported platforms. Libreswan has been ported to
|
||||
Win2k/BSD/OSX in the past as well.
|
||||
|
||||
Most distributions have native packaged support for Libreswan. Libreswan is
|
||||
available for RHEL, Fedora, Ubuntu, Debian, Arch, OpenWrt and more.
|
||||
|
||||
Unless a source-based build is truly needed, it is often best to use
|
||||
the pre-built version of the distribution you are using.
|
||||
|
||||
There are a few packages required for Libreswan to compile from source:
|
||||
|
||||
For Debian/Ubuntu
|
||||
|
||||
apt-get install libnss3-dev libnspr4-dev pkg-config libpam-dev \
|
||||
libcap-ng-dev libcap-ng-utils libselinux-dev \
|
||||
libcurl3-nss-dev flex bison gcc make libldns-dev \
|
||||
libunbound-dev libnss3-tools libevent-dev xmlto \
|
||||
libsystemd-dev
|
||||
|
||||
(there is no fipscheck library for these, set USE_FIPSCHECK=false)
|
||||
(unbound is build without event api, set USE_DNSSEC=false)
|
||||
|
||||
For Fedora/RHEL7/CentOS7
|
||||
|
||||
yum install audit-libs-devel bison curl-devel fipscheck-devel flex \
|
||||
gcc ldns-devel libcap-ng-devel libevent-devel \
|
||||
libseccomp-devel libselinux-devel make nspr-devel nss-devel \
|
||||
pam-devel pkgconfig systemd-devel unbound-devel xmlto
|
||||
|
||||
(on rhel/centos unbound is too old, set USE_DNSSEC=false)
|
||||
|
||||
For RHEL6/CentOS6
|
||||
|
||||
yum install audit-libs-devel bison curl-devel fipscheck-devel flex \
|
||||
gcc libcap-ng-devel libevent2-devel libseccomp-devel \
|
||||
libselinux-devel make nspr-devel nss-devel pam-devel \
|
||||
pkgconfig systemd-devel xmlto
|
||||
|
||||
(unbound is too old to build dnssec support, set USE_DNSSEC=false)
|
||||
|
||||
Runtime requirements (usually already present on the system)
|
||||
|
||||
nss, iproute2, iptables, sed, awk, bash, cut, procps-ng, which
|
||||
|
||||
(note: the Busybox version of "ip" does not support 'ip xfrm', so
|
||||
ensure you enable the iproute(2) package for busybox)
|
||||
|
||||
Python is used for "ipsec verify", which helps debugging problems
|
||||
python-ipaddress is used for "ipsec show", which shows tunnels
|
||||
|
||||
## Compiling the userland and IKE daemon
|
||||
|
||||
make programs
|
||||
sudo make install
|
||||
|
||||
If you want to build without creating and installing manual pages, run:
|
||||
|
||||
make base
|
||||
sudo make install-base
|
||||
|
||||
Note: The ipsec-tools package or setkey is not needed. Instead the iproute2
|
||||
packakge (>= 2.6.8) is required. Run `ipsec verify` to determine if your
|
||||
system misses any of the requirements. This will also tell you if any of
|
||||
the kernel sysctl values needs changing.
|
||||
|
||||
## Starting Libreswan
|
||||
The install will detect the init system used (systemd, upstart, sysvinit,
|
||||
openrc) and should integrate with the linux distribution. The service
|
||||
name is called "ipsec". For example, on RHEL7, one would use:
|
||||
|
||||
systemctl enable ipsec.service
|
||||
systemctl start ipsec.service
|
||||
|
||||
If unsure of the specific init system used on the system, the "ipsec"
|
||||
command can also be used to start or stop the ipsec service:
|
||||
|
||||
ipsec start
|
||||
ipsec stop
|
||||
|
||||
## Configuration
|
||||
Most of the libreswan configuration is stored in /etc/ipsec.conf and
|
||||
/etc/ipsec.secrets. Include files may be present in /etc/ipsec.d/
|
||||
See the respective man pages for more information.
|
||||
|
||||
## NSS initialisation
|
||||
Libreswan uses NSS to store private keys and X.509 certificates. The NSS
|
||||
database should have been initialised by the package installer. If not,
|
||||
the NSS database can be initialised using:
|
||||
|
||||
ipsec initnss
|
||||
|
||||
PKCS#12 certificates (.p12 files) can be imported using:
|
||||
|
||||
ipsec import /path/to/your.p12
|
||||
|
||||
See README.NSS and `certutil --help` for more details on using NSS and
|
||||
migrating from the old Openswan `/etc/ipsec.d/` directories to using NSS.
|
||||
|
||||
## Upgrading
|
||||
If you are upgrading from FreeS/WAN 1.x or Openswan 2.x to Libreswan 3.x,
|
||||
you might need to adjust your config files, although great care has been
|
||||
put into making the configuration files full backwards compatible. See
|
||||
also: https://libreswan.org/wiki/HOWTO:_openswan_to_libreswan_migration
|
||||
|
||||
See 'man ipsec.conf' for the list of options to find any new features.
|
||||
|
||||
You can run `make install` on top of your old version - it will not
|
||||
overwrite your your `/etc/ipsec.*` configuration files. The default install
|
||||
target installs in `/usr/local`. Ensure you do not install libreswan twice,
|
||||
one from a distribution package in /usr and once manually in /usr/local.
|
||||
|
||||
## Support
|
||||
|
||||
Mailing lists:
|
||||
|
||||
https://lists.libreswan.org/ is home of all our the mailing lists
|
||||
|
||||
Wiki:
|
||||
|
||||
https://libreswan.org is home to the Libreswan wiki. it contains
|
||||
documentation, interop guides and other useful information.
|
||||
|
||||
IRC:
|
||||
|
||||
Libreswan developers and users can be found on IRC, on #swan
|
||||
irc.freenode.net.
|
||||
|
||||
## Bugs
|
||||
Bugs can be reported on the mailing list or using our bug tracking system,
|
||||
at https://bugs.libreswan.org/
|
||||
|
||||
## Security Information
|
||||
All security issues found that require public disclosure will
|
||||
receive proper CVE tracking numbers (see https://www.mitre.org/) and
|
||||
will be co-ordinated via the vendor-sec / oss-security lists. A
|
||||
complete list of known security vulnerabilities is available at:
|
||||
|
||||
https://libreswan.org/security/
|
||||
|
||||
## Development
|
||||
Those interested in the development, patches, and beta releases of
|
||||
Libreswan can join the development mailing list "swan-dev" or talk to the
|
||||
development team on IRC in #swan on irc.freenode.net
|
||||
|
||||
For those who want to track things a bit more closely, the
|
||||
swan-commits@lists.libreswan.org mailing list will mail all the commit
|
||||
messages when they happen. This list is quite busy during active
|
||||
development periods.
|
||||
|
||||
## Documentation
|
||||
The most up to date documentation consists of the man pages that come
|
||||
with the software. Further documentation can be found at https://libreswan.org/
|
||||
and the wiki at https://libreswan.org/wiki/
|
||||
|
||||
|
|
@ -0,0 +1,268 @@
|
|||
|
||||
#########################################################################
|
||||
# Using the NSS crypto library with Pluto (Libreswan)
|
||||
# Based on initial documentation by Avesh Agarwal <avagarwa@redhat.com>
|
||||
#########################################################################
|
||||
|
||||
For detailed developer information about NSS, see
|
||||
https://www.mozilla.org/projects/security/pki/nss/
|
||||
|
||||
The NSS crypto library is a user space library. It is only used with the
|
||||
libreswan userspace IKE daemon pluto for cryptographic operations. NSS
|
||||
does not perform IPsec crypto operations inside the kernel (KLIPS
|
||||
nor NETKEY)
|
||||
|
||||
The NSS library exports a PKCS#11 API for the application to
|
||||
communicate to a cryptographic device. The cryptographic device is
|
||||
usually the "soft token" but can also be a Hardware Security Module
|
||||
(HSM).
|
||||
|
||||
The advantage of using NSS is that pluto does need to know in detail how
|
||||
the cryptographic device works. Pluto does not access any private keys or
|
||||
data itself. Instead, it uses the PK11 wrapper API of NSS irrespective
|
||||
of the cryptographic device used. Pluto hands over work using the PK11
|
||||
interface to NSS and never has direct access to the private key material
|
||||
itself. Both IKEv1 and IKEv2 operations are performed using NSS. Private
|
||||
RSA keys (raw RSA as well as X.509 based private RSA keys) are stored
|
||||
inside NSS. RSA keys are still referenced in /etc/ipsec.secrets. X.509
|
||||
keys and certificates are referenced using their "nickname" instead of
|
||||
their filename in /etc/ipsec.conf.
|
||||
|
||||
While PreShared Key (PSK) calculations are done using NSS, the actual
|
||||
preshared key ("secret") is still stored in /etc/ipsec.secrets.
|
||||
|
||||
NSS as shipped by Red Hat is a FIPS certified library. Libreswan is
|
||||
currently being FIPS certified for RHEL7.
|
||||
|
||||
#########################################################################
|
||||
# The NSS command line tools used with libreswan
|
||||
#########################################################################
|
||||
|
||||
- certutil: Look and modify the NSS db. "ipsec initnss" and "ipsec look"
|
||||
use certutil under the hood.
|
||||
|
||||
https://www.mozilla.org/projects/security/pki/nss/tools/certutil.html
|
||||
|
||||
- pk12util: import and export certificates and keys from and to the NSS db.
|
||||
The "ipsec import" command is a simple wrapper around this utility.
|
||||
|
||||
https://www.mozilla.org/projects/security/pki/nss/tools/pk12util.html
|
||||
|
||||
- modutil: Put NSS into FIPS mode
|
||||
|
||||
https://www.mozilla.org/projects/security/pki/nss/tools/modutil.html
|
||||
|
||||
#########################################################################
|
||||
# Creating the NSS db for use with libreswan's pluto IKE daemon
|
||||
#########################################################################
|
||||
|
||||
If you are not using a packaged libreswan version, you might need to
|
||||
create a new NSS db before you can start libreswan. This can be done
|
||||
using:
|
||||
|
||||
ipsec initnss
|
||||
|
||||
By default the NSS db is created in /etc/ipsec.d/ on RHEL/Fedora/CentOS
|
||||
but in /var/lib/ipsec/nss/ on Debian/Ubuntu. The remainder of this file
|
||||
uses /etc/ipsec.d/ in the examples.
|
||||
|
||||
When creating a database, you are prompted for a password. The default
|
||||
libreswan package install for RHEL/Fedora/CentOS uses an empty password.
|
||||
It is up to the administrator to decide on whether to use a password
|
||||
or not. However, a non-empty database password must be provided when
|
||||
running in FIPS mode.
|
||||
|
||||
To change the empty password, run:
|
||||
|
||||
certutil -W -d sql:/etc/ipsec.d
|
||||
|
||||
Enter return for the "old password", then enter your new password.
|
||||
|
||||
If you create the database with a password, and want to run NSS in FIPS
|
||||
mode, you must create a password file with the name "nsspassword" in
|
||||
the /etc/ipsec.d direcotry before starting libreswan. The "nsspassword"
|
||||
file must contain the password you provided when creating NSS database.
|
||||
|
||||
If the NSS db is protected with a non-empty password, the "nsspassword"
|
||||
file must exist for pluto to start.
|
||||
|
||||
The syntax of the "nsspassword" file is:
|
||||
|
||||
token_1_name:the_password
|
||||
token_2_name:the_password
|
||||
|
||||
The name of NSS softtoken (the default software NSS db) when NOT running
|
||||
in FIPS mode is "NSS Certificate DB". If you wish to use software NSS
|
||||
db with password "secret", you would have the following entry in the
|
||||
nsspassword file:
|
||||
|
||||
NSS Certificate DB:secret
|
||||
|
||||
If running NSS in FIPS mode, the name of NSS softtoken is
|
||||
"NSS FIPS 140-2 Certificate DB". If there are smartcards in the system, the
|
||||
entries for passwords should be entered in this file as well.
|
||||
|
||||
Note: do not enter any spaces before or after the token name or password.
|
||||
|
||||
#########################################################################
|
||||
# Using raw RSA keys with NSS
|
||||
#########################################################################
|
||||
|
||||
The "ipsec newhostkey" and "ipsec rsasigkey" utilities are used for
|
||||
creating raw RSA keys. If a non-default NSS directory is used, this can
|
||||
be specified using the --nssdir option.
|
||||
|
||||
ipsec newhostkey --nssdir /tmp/ipsec.d [--password password]
|
||||
|
||||
The password is only required if the NSS database is protected with a
|
||||
non-empty password.
|
||||
|
||||
Public key information is available via the "ipsec showhostkey" command
|
||||
can be used to generate left/rightrsasigkey= entries for /etc/ipsec.conf.
|
||||
|
||||
#########################################################################
|
||||
# Using certificates with NSS
|
||||
#########################################################################
|
||||
|
||||
Any X.509 certificate management system can be used to generate Certificate
|
||||
Agencies, certificates, pkcs12 files and CRLs. Common tools people use are
|
||||
the openssl command, the GTK utility tinyca2, or the NSS certutil command.
|
||||
|
||||
An example using openssl can be found as part of the libreswan test suite at
|
||||
https://github.com/libreswan/libreswan/tree/master/testing/x509
|
||||
|
||||
Below, we will be using the nss tools to generate certificates
|
||||
|
||||
* To create a certificate authority (CA certificate):
|
||||
|
||||
certutil -S -k rsa -n "ExampleCA" -s "CN=Example CA Inc" -v 12 \
|
||||
-t "CT,," -x -d sql:/etc/ipsec.d
|
||||
|
||||
It creates a certificate with RSA keys (-k rsa) with the nickname
|
||||
"ExampleCA", and with common name "Example CA Inc". The option
|
||||
"-v" specifies the certificates validy period. "-t" specifies the attributes
|
||||
of the certificate. "C" is required for creating a CA certificate. "-x" mean
|
||||
self signed. "-d" specifies the path of the database directory. The directory
|
||||
path should be prefixed with 'sql:' in order to use the SQLite format.
|
||||
|
||||
NOTE: It is not a requirement to create the CA in NSS database. The CA
|
||||
certificate can be obtained from anywhere in the world.
|
||||
|
||||
* To create a user certificate signed by the above CA
|
||||
|
||||
certutil -S -k rsa -c "ExampleCA" -n "user1" -s "CN=User Common Name" \
|
||||
-v 12 -t "u,u,u" -d sql:/etc/ipsec.d
|
||||
|
||||
It creates a user cert with nickname "user1" with attributes
|
||||
"u,u,u" signed by the CA cert "ExampleCA".
|
||||
|
||||
NOTE: You must provide a nick name when creating a user certificate,
|
||||
because pluto reads the user certificate from the NSS database based on
|
||||
the user certificate's nickname.
|
||||
|
||||
|
||||
#########################################################################
|
||||
# Configuring certificates in ipsec.conf and ipsec.secrets
|
||||
#########################################################################
|
||||
|
||||
In ipsec.conf, the leftcert= option takes a certificate nickname as argument.
|
||||
For example if the nickname of the user cert is "hugh", then it can be
|
||||
"leftcert=hugh".
|
||||
|
||||
NOTE: if you are migrating from openswan, you are used to specifying
|
||||
a filename for the leftcert= option. Filenames
|
||||
are not valid for the left/rightcert= options in libreswan.
|
||||
|
||||
In ipsec.secrets, we need to list the certificate nickname to inform pluto
|
||||
there is a certificate within the NSS db.
|
||||
This is specified using:
|
||||
|
||||
: RSA nickname
|
||||
|
||||
NOTE: In openswan and freeswan it was required to specify a file name or
|
||||
password. With libreswan, this is not required.
|
||||
NOTE: openswan and freeswan stored private keys in /etc/ipsec.d/private/
|
||||
This directory does not exist for libreswan.
|
||||
|
||||
The directories /etc/ipsec.d/cacerts/ and /etc/ipsec.d/crls/ can still be used.
|
||||
|
||||
NOTE: the freeswan and openswan directories /etc/ipsec.d/aacerts/ and
|
||||
/etc/ipsec.d/acerts/ are not used with libreswan.
|
||||
|
||||
If you use an external CA certificate, you can either import it into
|
||||
the NSS db or place it in the /etc/ipsec.d/cacerts/ directory. Note that
|
||||
the preferred method is to store it inside the NSS db.
|
||||
|
||||
#########################################################################
|
||||
# Importing third-party certificates into NSS
|
||||
#########################################################################
|
||||
|
||||
If you do not have the third-party certificate in PKCS#12 format, use openssl
|
||||
to create a PKCS#12 file:
|
||||
|
||||
openssl pkcs12 -export -in cert.pem -inkey key.pem \
|
||||
-certfile cacert.pem -out certkey.p12 [-name YourName]
|
||||
|
||||
Now you can import the file into the NSS db:
|
||||
|
||||
ipsec import certkey.p12
|
||||
|
||||
If you did not pick a name using the -name option, you can use
|
||||
certutil -L -d sql:/etc/ipsec.d to figure out the name NSS picked during
|
||||
the import.
|
||||
|
||||
Add following to /etc/ipsec.secrets file:
|
||||
|
||||
: RSA "YourName"
|
||||
|
||||
To specify the certificate in ipsec.conf, use a line like:
|
||||
|
||||
leftcert=YourName
|
||||
|
||||
#########################################################################
|
||||
# Exporting a CA(?) certificate to load on another libreswan machine
|
||||
#########################################################################
|
||||
|
||||
|
||||
Paul: wouldn't this also include the private key which we don't want?????
|
||||
Paul: add "ipsec export" ?
|
||||
|
||||
To export the CA certificate:
|
||||
|
||||
pk12util -o cacert1.p12 -n cacert1 -d sql:/etc/ipsec.d
|
||||
|
||||
Copy the file "cacert1.p12" to the new machine and import it using:
|
||||
|
||||
ipsec import cacert1.p12
|
||||
certutil -M -n cacert1 -t "CT,," -d sql:/etc/ipsec.d
|
||||
|
||||
Example connection for ipsec.conf:
|
||||
|
||||
conn pluto-1-2
|
||||
left=1.2.3.4
|
||||
leftid="CN=usercert1"
|
||||
leftrsasigkey=%cert
|
||||
leftcert=usercert1
|
||||
right=5.6.7.8
|
||||
rightid="CN=usercert2"
|
||||
rightrsasigkey=%cert
|
||||
auto=add
|
||||
|
||||
#########################################################################
|
||||
# Configuring a smartcard with NSS
|
||||
#########################################################################
|
||||
|
||||
Required library: libcoolkey
|
||||
|
||||
To make smartcard tokens visible through NSS
|
||||
|
||||
modutil -add <module_name> -libfile libcoolkeypk11.so \
|
||||
-dbdir <nss_database_dir_name> \
|
||||
-mechanisms <mechanisms_separted_by_colons>
|
||||
|
||||
An example of mechanisms can be
|
||||
RC2:RC4:DES:DH:SHA1:MD5:MD2:SSL:TLS:AES:CAMELLIA.
|
||||
|
||||
To check whether the token is visible or not, please run
|
||||
|
||||
modutil -list -dbdir <nss_database_dir_name>
|
||||
|
|
@ -0,0 +1,3 @@
|
|||
|
||||
See README.nss or check the wiki at https://libreswan.org/
|
||||
|
||||
|
|
@ -0,0 +1,9 @@
|
|||
|
||||
placeholder: this should contain information to demonstrate trademark
|
||||
use similar to debian's policy, eg https://wiki.mako.cc/Draft_Debian_trademark_policy
|
||||
or Mozilla's https://www.mozilla.org/foundation/trademarks/faq.html
|
||||
|
||||
The goal is to make it free to everyone, but avoid future problems where
|
||||
third parties claim to own the name, trademark, logo or code.
|
||||
|
||||
|
||||
|
|
@ -0,0 +1,4 @@
|
|||
#!/bin/sh
|
||||
|
||||
make OS=cygwin BUILDENV=cygwin32-linux programs
|
||||
|
||||
|
|
@ -0,0 +1,10 @@
|
|||
|
||||
Unmaintained contrib files - mostly outdated and unwise to use
|
||||
|
||||
cisco-decrypt - decrypt cisco obfuscation secrets in cisco *.pcf files
|
||||
cisco-pcf - convert cisco PCF configuration files to libreswan config files
|
||||
ldsaref - SAref example implementation
|
||||
lucent - interop hacking with some proprietary lucent gateway
|
||||
patching - klips patching scripts from/between klips trees (unused)
|
||||
scripts - perl scripts for emulating ipsec eroute output when using NETKEY
|
||||
python-swan - python module to determine if traffic to a destination would get encrypted
|
||||
|
|
@ -0,0 +1,25 @@
|
|||
.PHONY: clean
|
||||
|
||||
CFLAGS += \
|
||||
-I/usr/include/nspr4 \
|
||||
-I../../include \
|
||||
-I../../linux/include
|
||||
|
||||
LIBSRC = \
|
||||
../../lib/libswan/initsubnet.c \
|
||||
../../lib/libswan/ip_address.c \
|
||||
../../lib/libswan/sameaddr.c \
|
||||
../../lib/libswan/subnettypeof.c \
|
||||
../../lib/libswan/ttoaddr.c \
|
||||
../../lib/libswan/ttosubnet.c \
|
||||
../../lib/libswan/ttoul.c \
|
||||
../../linux/net/ipsec/addrtot.c \
|
||||
../../linux/net/ipsec/addrtypeof.c \
|
||||
../../linux/net/ipsec/anyaddr.c \
|
||||
../../linux/net/ipsec/initaddr.c \
|
||||
../../linux/net/ipsec/ultot.c
|
||||
|
||||
is_encrypted: is_encrypted.c swan.c $(LIBSRC)
|
||||
|
||||
clean:
|
||||
rm -f is_encrypted
|
||||
|
|
@ -0,0 +1,77 @@
|
|||
/*
|
||||
* Is connection encrypted? -utility.
|
||||
*
|
||||
* Copyright (C) 2018 Kim B. Heino <b@bbbs.net>
|
||||
*
|
||||
* This program is free software; you can redistribute it and/or modify
|
||||
* it under the terms of the GNU General Public License as published by
|
||||
* the Free Software Foundation; either version 2 of the License, or
|
||||
* (at your option) any later version.
|
||||
*
|
||||
* This program is distributed in the hope that it will be useful,
|
||||
* but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
* GNU General Public License for more details.
|
||||
*
|
||||
* You should have received a copy of the GNU General Public License along
|
||||
* with this program; if not, write to the Free Software Foundation, Inc.,
|
||||
* 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
|
||||
*/
|
||||
|
||||
#include <stdio.h>
|
||||
#include <stdlib.h>
|
||||
#include <getopt.h>
|
||||
#include <string.h>
|
||||
#include "swan.h"
|
||||
|
||||
/* Parse args and call is_encrypted() from swan.c */
|
||||
int main(int argc, char *argv[])
|
||||
{
|
||||
char source_ip[IPLEN + 1], dest_ip[IPLEN + 1];
|
||||
int debug = 0, port = 0;
|
||||
|
||||
*source_ip = 0;
|
||||
*dest_ip = 0;
|
||||
for (;;) {
|
||||
static struct option long_options[] = {
|
||||
{"debug", no_argument, 0, 1},
|
||||
{"source", required_argument, 0, 2},
|
||||
{"port", required_argument, 0, 3},
|
||||
{0, 0, 0, 0}
|
||||
};
|
||||
int option_index = 0, opt;
|
||||
|
||||
opt = getopt_long(argc, argv, "", long_options, &option_index);
|
||||
if (opt == -1)
|
||||
break;
|
||||
|
||||
switch (opt) {
|
||||
case 1:
|
||||
debug = 1;
|
||||
break;
|
||||
|
||||
case 2:
|
||||
strncpy(source_ip, optarg, IPLEN);
|
||||
source_ip[IPLEN] = 0;
|
||||
break;
|
||||
|
||||
case 3:
|
||||
port = atoi(optarg);
|
||||
break;
|
||||
|
||||
default:
|
||||
exit(1);
|
||||
}
|
||||
}
|
||||
|
||||
if (optind != argc - 1) {
|
||||
printf("No destination IP address specified\n");
|
||||
exit(1);
|
||||
}
|
||||
strncpy(dest_ip, argv[optind], IPLEN);
|
||||
dest_ip[IPLEN] = 0;
|
||||
|
||||
int ret = is_encrypted(dest_ip, port, source_ip, 2, debug);
|
||||
printf("%s\n", ret ? "True" : "False");
|
||||
return ret;
|
||||
}
|
||||
|
|
@ -0,0 +1,309 @@
|
|||
/*
|
||||
* Is connection encrypted? -utility.
|
||||
*
|
||||
* Copyright (C) 2018 Kim B. Heino <b@bbbs.net>
|
||||
*
|
||||
* This program is free software; you can redistribute it and/or modify
|
||||
* it under the terms of the GNU General Public License as published by
|
||||
* the Free Software Foundation; either version 2 of the License, or
|
||||
* (at your option) any later version.
|
||||
*
|
||||
* This program is distributed in the hope that it will be useful,
|
||||
* but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
* GNU General Public License for more details.
|
||||
*
|
||||
* You should have received a copy of the GNU General Public License along
|
||||
* with this program; if not, write to the Free Software Foundation, Inc.,
|
||||
* 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
|
||||
*/
|
||||
|
||||
#include <stdio.h>
|
||||
#include <stdlib.h>
|
||||
#include <unistd.h>
|
||||
#include <sys/wait.h>
|
||||
#include <getopt.h>
|
||||
#include <string.h>
|
||||
#include <sys/socket.h>
|
||||
#include <sys/time.h>
|
||||
#include <sys/types.h>
|
||||
#include <arpa/inet.h>
|
||||
#include <fcntl.h>
|
||||
#include <netdb.h>
|
||||
#include "libreswan.h"
|
||||
#include "swan.h"
|
||||
|
||||
#define COMMAND_BUFFER 65536 /* Max length of "ip xfrm" output */
|
||||
|
||||
/* Dummy logger to require less lib dependencies. */
|
||||
int libreswan_log(const char *fmt, ...)
|
||||
{
|
||||
return 0;
|
||||
}
|
||||
|
||||
/* Run external command and return its output, NUL terminated. */
|
||||
static char *run_command(char **params)
|
||||
{
|
||||
int link[2];
|
||||
pid_t pid;
|
||||
char *buffer;
|
||||
|
||||
if (pipe(link) == -1)
|
||||
return NULL;
|
||||
if ((pid = fork()) == -1)
|
||||
return NULL;
|
||||
|
||||
if (pid == 0) {
|
||||
dup2(link[1], STDOUT_FILENO);
|
||||
close(link[0]);
|
||||
close(link[1]);
|
||||
execv(params[0], params);
|
||||
exit(0);
|
||||
}
|
||||
|
||||
buffer = malloc(COMMAND_BUFFER);
|
||||
if (buffer == NULL)
|
||||
return NULL;
|
||||
|
||||
close(link[1]);
|
||||
int nbytes = read(link[0], buffer, COMMAND_BUFFER - 1);
|
||||
wait(NULL);
|
||||
close(link[0]);
|
||||
if (nbytes < 0)
|
||||
nbytes = 0;
|
||||
buffer[nbytes] = 0;
|
||||
return buffer;
|
||||
}
|
||||
|
||||
/* Split command output to NUL terminated words. */
|
||||
static char *split_words(char *command_output)
|
||||
{
|
||||
char *buffer, *from, *to;
|
||||
|
||||
/* Worst case is "\n\n...", resulting 2 * input size */
|
||||
buffer = malloc(COMMAND_BUFFER * 2 + 2);
|
||||
if (buffer == NULL)
|
||||
return NULL;
|
||||
|
||||
/* Split to words */
|
||||
from = command_output;
|
||||
to = buffer;
|
||||
if (from != NULL)
|
||||
while (*from != 0) {
|
||||
/* Skip " " and "\" */
|
||||
while (*from == ' ' || *from == '\t' || *from == '\\')
|
||||
from++;
|
||||
|
||||
if (*from == '\n') {
|
||||
/* Copy "\n" as word */
|
||||
*(to++) = *(from++);
|
||||
|
||||
} else {
|
||||
/* Copy word */
|
||||
while (*from > ' ' && *from != '\\')
|
||||
*(to++) = *(from++);
|
||||
}
|
||||
|
||||
*(to++) = 0;
|
||||
}
|
||||
|
||||
/* Add end marker */
|
||||
*(to++) = 0;
|
||||
*(to++) = 0;
|
||||
|
||||
/* Free command output buffer */
|
||||
if (command_output != NULL)
|
||||
free(command_output);
|
||||
return buffer;
|
||||
}
|
||||
|
||||
/* Get my source IP address */
|
||||
static int get_source_ip(char *destination, char *source)
|
||||
{
|
||||
char *output, *p;
|
||||
char *params[8];
|
||||
|
||||
params[0] = "/sbin/ip";
|
||||
params[1] = "-oneline";
|
||||
params[2] = "route";
|
||||
params[3] = "get";
|
||||
params[4] = destination;
|
||||
params[5] = NULL;
|
||||
output = split_words(run_command(params));
|
||||
|
||||
for (p = output; *p != 0; p += strlen(p) + 1) {
|
||||
if (strcmp(p, "src") == 0) {
|
||||
strncpy(source, p + strlen(p) + 1, IPLEN);
|
||||
source[IPLEN] = 0;
|
||||
break;
|
||||
}
|
||||
}
|
||||
|
||||
free(output);
|
||||
if (*source == 0) {
|
||||
printf("Failed to detect source IP\n");
|
||||
return -1;
|
||||
}
|
||||
return 0;
|
||||
}
|
||||
|
||||
/* Is address inside subnet+mask? */
|
||||
static bool addr_in_mask(char *address_str, char *mask_str)
|
||||
{
|
||||
ip_address address;
|
||||
ip_subnet mask;
|
||||
err_t err;
|
||||
|
||||
err = ttoaddr(address_str, 0, AF_UNSPEC, &address);
|
||||
if (err)
|
||||
return false;
|
||||
err = ttosubnet(mask_str, 0, AF_UNSPEC, &mask);
|
||||
if (err)
|
||||
return false;
|
||||
return addrinsubnet(&address, &mask);
|
||||
}
|
||||
|
||||
/* Get "ip xfrm" output */
|
||||
static char *get_policy_list(void)
|
||||
{
|
||||
char *output;
|
||||
char *params[8];
|
||||
|
||||
params[0] = "/sbin/ip";
|
||||
params[1] = "-oneline";
|
||||
params[2] = "xfrm";
|
||||
params[3] = "policy";
|
||||
params[4] = "list";
|
||||
params[5] = NULL;
|
||||
|
||||
output = split_words(run_command(params));
|
||||
return output;
|
||||
}
|
||||
|
||||
/* Parse xfrm policy list */
|
||||
static bool parse_policy_list(char *source, char *destination, char *xfrm, int debug)
|
||||
{
|
||||
struct {
|
||||
char src[128];
|
||||
char dst[128];
|
||||
char dir[128];
|
||||
char priority[128];
|
||||
char proto[128];
|
||||
char reqid[128];
|
||||
} parsed;
|
||||
bool encrypted = false;
|
||||
int priority = 65536;
|
||||
char *keyword, *p;
|
||||
|
||||
memset(&parsed, 0, sizeof(parsed));
|
||||
keyword = NULL;
|
||||
for (p = xfrm; *p != 0; p += strlen(p) + 1) {
|
||||
if (*p == '\n') {
|
||||
/* End of line - check it */
|
||||
int prio = atoi(parsed.priority);
|
||||
|
||||
if (strcmp(parsed.dir, "out") == 0 &&
|
||||
strcmp(parsed.proto, "esp") == 0 &&
|
||||
prio > 0 &&
|
||||
prio < priority &&
|
||||
*parsed.src != 0 &&
|
||||
*parsed.dst != 0 &&
|
||||
addr_in_mask(source, parsed.src) &&
|
||||
addr_in_mask(destination, parsed.dst)) {
|
||||
/* Got match, update encrypted variable. */
|
||||
if (debug)
|
||||
printf("src %s dst %s dir %s priority %s proto %s reqid %s\n",
|
||||
parsed.src,
|
||||
parsed.dst,
|
||||
parsed.dir,
|
||||
parsed.priority,
|
||||
parsed.proto,
|
||||
parsed.reqid);
|
||||
priority = prio;
|
||||
encrypted = *parsed.reqid != 0 &&
|
||||
strcmp(parsed.reqid, "0") != 0;
|
||||
}
|
||||
|
||||
memset(&parsed, 0, sizeof(parsed));
|
||||
keyword = NULL;
|
||||
|
||||
} else if (keyword != NULL) {
|
||||
if (*keyword == 0) {
|
||||
strncpy(keyword, p, IPLEN);
|
||||
keyword[IPLEN] = 0;
|
||||
}
|
||||
keyword = NULL;
|
||||
|
||||
} else if (strcmp(p, "src") == 0)
|
||||
keyword = parsed.src;
|
||||
else if (strcmp(p, "dst") == 0)
|
||||
keyword = parsed.dst;
|
||||
else if (strcmp(p, "dir") == 0)
|
||||
keyword = parsed.dir;
|
||||
else if (strcmp(p, "priority") == 0)
|
||||
keyword = parsed.priority;
|
||||
else if (strcmp(p, "proto") == 0)
|
||||
keyword = parsed.proto;
|
||||
else if (strcmp(p, "reqid") == 0)
|
||||
keyword = parsed.reqid;
|
||||
}
|
||||
return encrypted;
|
||||
}
|
||||
|
||||
/* Connect to dest:port, ignore errors */
|
||||
static void connect_to(char *destination, int port, int timeout)
|
||||
{
|
||||
struct addrinfo hints;
|
||||
struct addrinfo *result, *rp;
|
||||
char port_str[16];
|
||||
int sock;
|
||||
fd_set fdset;
|
||||
struct timeval tv;
|
||||
|
||||
/* Parse destination:port */
|
||||
memset(&hints, 0, sizeof(struct addrinfo));
|
||||
hints.ai_family = AF_UNSPEC;
|
||||
hints.ai_socktype = SOCK_STREAM;
|
||||
hints.ai_flags = 0;
|
||||
hints.ai_protocol = 0;
|
||||
|
||||
sprintf(port_str, "%d", port);
|
||||
if (getaddrinfo(destination, port_str, &hints, &result) != 0)
|
||||
return;
|
||||
|
||||
for (rp = result; rp != NULL; rp = rp->ai_next) {
|
||||
/* Open non-blocking connection */
|
||||
sock = socket(rp->ai_family, rp->ai_socktype, rp->ai_protocol);
|
||||
if (sock == -1)
|
||||
continue;
|
||||
fcntl(sock, F_SETFL, O_NONBLOCK);
|
||||
connect(sock, rp->ai_addr, rp->ai_addrlen);
|
||||
|
||||
/* Wait until timeout or connected */
|
||||
FD_ZERO(&fdset);
|
||||
FD_SET(sock, &fdset);
|
||||
tv.tv_sec = timeout;
|
||||
tv.tv_usec = 0;
|
||||
select(sock + 1, NULL, &fdset, NULL, &tv);
|
||||
close(sock);
|
||||
}
|
||||
freeaddrinfo(result);
|
||||
}
|
||||
|
||||
/* Is connection encrypted? */
|
||||
bool is_encrypted(char *destination, int port, char *source, int timeout,
|
||||
int debug)
|
||||
{
|
||||
if (*source == 0 && get_source_ip(destination, source) == -1)
|
||||
return false;
|
||||
if (debug)
|
||||
printf("Checking %s to %s port %d\n", source, destination,
|
||||
port);
|
||||
if (port > 0)
|
||||
connect_to(destination, port, timeout);
|
||||
|
||||
char *xfrm = get_policy_list();
|
||||
bool ret = parse_policy_list(source, destination, xfrm, debug);
|
||||
free(xfrm);
|
||||
return ret;
|
||||
}
|
||||
|
|
@ -0,0 +1,24 @@
|
|||
/*
|
||||
* Is connection encrypted? -utility.
|
||||
*
|
||||
* Copyright (C) 2018 Kim B. Heino <b@bbbs.net>
|
||||
*
|
||||
* This program is free software; you can redistribute it and/or modify
|
||||
* it under the terms of the GNU General Public License as published by
|
||||
* the Free Software Foundation; either version 2 of the License, or
|
||||
* (at your option) any later version.
|
||||
*
|
||||
* This program is distributed in the hope that it will be useful,
|
||||
* but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
* GNU General Public License for more details.
|
||||
*
|
||||
* You should have received a copy of the GNU General Public License along
|
||||
* with this program; if not, write to the Free Software Foundation, Inc.,
|
||||
* 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
|
||||
*/
|
||||
|
||||
#define IPLEN 100 /* Max length for IP address/mask string */
|
||||
|
||||
bool is_encrypted(char *destination, int port, char *source, int timeout,
|
||||
int debug);
|
||||
|
|
@ -0,0 +1,12 @@
|
|||
all: cisco-decrypt
|
||||
|
||||
clean:
|
||||
rm cisco-decrypt
|
||||
|
||||
install:
|
||||
echo "cisco-decrypt is also installed as part of the vpnc packae"
|
||||
install -D cisco-decrypt /usr/local/bin/
|
||||
install -D cisco-decrypt.1 /usr/local/man/man1/
|
||||
|
||||
cisco-decrypt:
|
||||
cc -lgcrypt -o cisco-decrypt cisco-decrypt.c
|
||||
|
|
@ -0,0 +1,5 @@
|
|||
See source code for copyrights and information. Taken from the vpnc
|
||||
package.
|
||||
|
||||
It is not installed per default, because vpnc already installs it. It
|
||||
is here for reference only.
|
||||
|
|
@ -0,0 +1,29 @@
|
|||
.TH "CISCO-DECRYPT" "1" "August 2007" "cisco-decrypt" "vpnc"
|
||||
.SH "NAME"
|
||||
cisco-decrypt \- decrypts an obfuscated Cisco vpn client pre-shared key
|
||||
.\"
|
||||
.\" $Id: cisco-decrypt.1 204 2007-08-14 18:01:28Z Joerg Mayer $
|
||||
.\"
|
||||
.SH "SYNOPSIS"
|
||||
.B cisco-decrypt
|
||||
\fI<obfuscated pre-shared key>
|
||||
.SH "DESCRIPTION"
|
||||
This command accompanies \fBvpnc\fR. It decrypts the obfuscated
|
||||
pre-shared key from *.pcf\-configuration files, which must be
|
||||
specified on the command line.
|
||||
|
||||
The result will be printed to STDOUT.
|
||||
.SH "AUTHOR"
|
||||
cisco-decrypt was originally written by Maurice Massar. This man\-page was
|
||||
written by Jörg Mayer, based on the pcf2vpnc manpage written by Wolfram Sang
|
||||
(ninja(at)the\-dreams.de).
|
||||
|
||||
Permission is granted to copy, distribute and/or modify this document under
|
||||
the terms of the GNU General Public License, Version 2 any
|
||||
later version published by the Free Software Foundation.
|
||||
.PP
|
||||
On Debian systems, the complete text of the GNU General Public
|
||||
License can be found in /usr/share/common\-licenses/GPL.
|
||||
.SH "SEE ALSO"
|
||||
.BR vpnc(8)
|
||||
.BR pcf2vpnc(1)
|
||||
|
|
@ -0,0 +1,195 @@
|
|||
|
||||
/* IPsec VPN client compatible with Cisco equipment.
|
||||
Copyright (C) 2004-2005 Maurice Massar
|
||||
|
||||
This program is free software; you can redistribute it and/or modify
|
||||
it under the terms of the GNU General Public License as published by
|
||||
the Free Software Foundation; either version 2 of the License, or
|
||||
(at your option) any later version.
|
||||
|
||||
This program is distributed in the hope that it will be useful,
|
||||
but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
GNU General Public License for more details.
|
||||
|
||||
You should have received a copy of the GNU General Public License
|
||||
along with this program; if not, write to the Free Software
|
||||
Foundation, Inc., 59 Temple Place, Suite 330, Boston, MA 02111-1307 USA
|
||||
|
||||
$Id: config.c 242 2007-09-09 07:55:21Z Joerg Mayer $
|
||||
*/
|
||||
|
||||
#define _GNU_SOURCE
|
||||
|
||||
#include <inttypes.h>
|
||||
#include <stdio.h>
|
||||
#include <stdlib.h>
|
||||
#include <unistd.h>
|
||||
#include <string.h>
|
||||
#include <errno.h>
|
||||
#include <sys/utsname.h>
|
||||
|
||||
#include <gcrypt.h>
|
||||
|
||||
static int hex2bin_c(unsigned int c)
|
||||
{
|
||||
if ((c >= '0') && (c <= '9'))
|
||||
return c - '0';
|
||||
|
||||
if ((c >= 'A') && (c <= 'F'))
|
||||
return c - 'A' + 10;
|
||||
|
||||
if ((c >= 'a') && (c <= 'f'))
|
||||
return c - 'a' + 10;
|
||||
|
||||
return -1;
|
||||
}
|
||||
|
||||
int hex2bin(const char *str, char **bin, int *len)
|
||||
{
|
||||
char *p;
|
||||
int i, l;
|
||||
|
||||
if (!bin)
|
||||
return EINVAL;
|
||||
|
||||
for (i = 0; str[i] != '\0'; i++)
|
||||
if (hex2bin_c(str[i]) == -1)
|
||||
return EINVAL;
|
||||
|
||||
l = i;
|
||||
if ((l & 1) != 0)
|
||||
return EINVAL;
|
||||
|
||||
l /= 2;
|
||||
|
||||
p = malloc(l);
|
||||
if (p == NULL)
|
||||
return ENOMEM;
|
||||
|
||||
for (i = 0; i < l; i++)
|
||||
p[i] = hex2bin_c(str[i * 2]) << 4 | hex2bin_c(str[i * 2 + 1]);
|
||||
|
||||
*bin = p;
|
||||
if (len)
|
||||
*len = l;
|
||||
|
||||
return 0;
|
||||
}
|
||||
|
||||
int deobfuscate(char *ct, int len, const char **resp, char *reslenp)
|
||||
{
|
||||
const char *h1 = ct;
|
||||
const char *h4 = ct + 20;
|
||||
const char *enc = ct + 40;
|
||||
|
||||
char ht[20], h2[20], h3[20], key[24];
|
||||
const char *iv = h1;
|
||||
char *res;
|
||||
gcry_cipher_hd_t ctx;
|
||||
int reslen;
|
||||
|
||||
if (len < 48)
|
||||
return -1;
|
||||
|
||||
len -= 40;
|
||||
|
||||
memcpy(ht, h1, 20);
|
||||
|
||||
ht[19]++;
|
||||
gcry_md_hash_buffer(GCRY_MD_SHA1, h2, ht, 20);
|
||||
|
||||
ht[19] += 2;
|
||||
gcry_md_hash_buffer(GCRY_MD_SHA1, h3, ht, 20);
|
||||
|
||||
memcpy(key, h2, 20);
|
||||
memcpy(key + 20, h3, 4);
|
||||
/* who cares about parity anyway? */
|
||||
|
||||
gcry_md_hash_buffer(GCRY_MD_SHA1, ht, enc, len);
|
||||
|
||||
if (!memeq(h4, ht, 20))
|
||||
return -1;
|
||||
|
||||
res = malloc(len);
|
||||
if (res == NULL)
|
||||
return -1;
|
||||
|
||||
gcry_cipher_open(&ctx, GCRY_CIPHER_3DES, GCRY_CIPHER_MODE_CBC, 0);
|
||||
gcry_cipher_setkey(ctx, key, 24);
|
||||
gcry_cipher_setiv(ctx, iv, 8);
|
||||
gcry_cipher_decrypt(ctx, (unsigned char *)res, len,
|
||||
(unsigned char *)enc, len);
|
||||
gcry_cipher_close(ctx);
|
||||
|
||||
reslen = len - res[len - 1];
|
||||
res[reslen] = '\0';
|
||||
|
||||
if (resp)
|
||||
*resp = res;
|
||||
if (reslenp)
|
||||
*reslenp = reslen;
|
||||
return 0;
|
||||
}
|
||||
|
||||
/* Decoder for password encoding of Cisco VPN client.
|
||||
Copyright (C) 2005 Maurice Massar
|
||||
|
||||
Thanks to HAL-9000@evilscientists.de for decoding and posting the algorithm!
|
||||
|
||||
This program is free software; you can redistribute it and/or modify
|
||||
it under the terms of the GNU General Public License as published by
|
||||
the Free Software Foundation; either version 2 of the License, or
|
||||
(at your option) any later version.
|
||||
|
||||
This program is distributed in the hope that it will be useful,
|
||||
but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
GNU General Public License for more details.
|
||||
|
||||
You should have received a copy of the GNU General Public License
|
||||
along with this program; if not, write to the Free Software
|
||||
Foundation, Inc., 59 Temple Place, Suite 330, Boston, MA 02111-1307 USA
|
||||
*/
|
||||
|
||||
#include <stdio.h>
|
||||
#include <stdlib.h>
|
||||
#include <gcrypt.h>
|
||||
#include <errno.h>
|
||||
|
||||
int main(int argc, char *argv[])
|
||||
{
|
||||
int i, len, ret = 0;
|
||||
char *bin, *pw = NULL;
|
||||
|
||||
gcry_check_version(NULL);
|
||||
|
||||
if (argc == 1 || *argv[1] == '-') {
|
||||
fprintf(stderr,
|
||||
"\nUsage: %s DEADBEEF...012345678 424242...7261\n"
|
||||
" Print decoded result to stdout\n\n",
|
||||
argv[0]);
|
||||
exit(1);
|
||||
}
|
||||
/* Hack for use in pcf2vpnc */
|
||||
if (*argv[1] == 'q')
|
||||
exit(1);
|
||||
|
||||
for (i = 1; i < argc; i++) {
|
||||
ret = hex2bin(argv[i], &bin, &len);
|
||||
if (ret != 0) {
|
||||
perror("decoding input");
|
||||
continue;
|
||||
}
|
||||
ret = deobfuscate(bin, len, (const char **)&pw, NULL);
|
||||
free(bin);
|
||||
if (ret != 0) {
|
||||
perror("decrypting input");
|
||||
continue;
|
||||
}
|
||||
printf("%s\n", pw);
|
||||
free(pw);
|
||||
}
|
||||
|
||||
exit(ret != 0);
|
||||
}
|
||||
|
|
@ -0,0 +1,9 @@
|
|||
This little tool will convert a Cisco PCF file to an Libreswan style
|
||||
ipsec.conf connection.
|
||||
|
||||
If your PCF file contains an "encrypted" (obfuscated) password, then you
|
||||
can find the plaintext version by running the Linux Cisco VPN client within
|
||||
strace. See http://femto.cs.uiuc.edu/~sbond/vpnc/ for more information.
|
||||
|
||||
ExecSum: "ltrace -i ./vpnclient connect ... 2>&1 | fgrep 805ac57" to decode
|
||||
the passwords. (client: vpnclient-linux-4.0.3.B-k9).
|
||||
|
|
@ -0,0 +1,58 @@
|
|||
#!/usr/bin/perl
|
||||
#
|
||||
# (C) 2004 Ken Bantoft <ken@xelerance.com>
|
||||
#
|
||||
# This script converts most Cisco VPN client .pcf files to Libreswan's
|
||||
# ipsec.conf and ipsec.secrets format
|
||||
#
|
||||
|
||||
die "Usage: ./pcf2os.pl cisco-config.pcf\n\n" if ! $ARGV[0];
|
||||
|
||||
open(PCF,$ARGV[0]);
|
||||
while(<PCF>) {
|
||||
chop;
|
||||
# print "[$_]";
|
||||
if (m/^description/i) {
|
||||
s/.*=//;
|
||||
s/\ /\_/g;
|
||||
$desc=$_;
|
||||
}
|
||||
if (m/^host/i) {
|
||||
s/.*=//;
|
||||
$right=$_;
|
||||
}
|
||||
|
||||
if (m/^groupname/i) {
|
||||
s/.*=//;
|
||||
$groupname=$_;
|
||||
}
|
||||
|
||||
if (m/^grouppwd/i) {
|
||||
s/.*=//;
|
||||
$grouppassword=$_;
|
||||
}
|
||||
|
||||
|
||||
|
||||
}
|
||||
close(PCF);
|
||||
|
||||
print "ipsec.conf\n\n";
|
||||
print "conn $desc\n";
|
||||
print " ike=aes-sha1-modp1536\n";
|
||||
print " aggressive=yes\n";
|
||||
print " authby=secret\n";
|
||||
print " left=%defaultroute\n";
|
||||
print " leftid=\@$groupname\n";
|
||||
print " leftxauthclient=yes\n";
|
||||
print " leftmodecfgclient=yes\n";
|
||||
print " right=$right\n";
|
||||
print " rightxauthserver=yes\n";
|
||||
print " rightmodecfgserver=yes\n";
|
||||
print " pfs=no\n";
|
||||
print " auto=add\n";
|
||||
|
||||
print "\n\n";
|
||||
print "ipsec.secrets:\n\n";
|
||||
print "\@$groupname $right : PSK \"$grouppassword\"\n";
|
||||
|
||||
|
|
@ -0,0 +1,32 @@
|
|||
[main]
|
||||
Description=Example Cisco Config Profile
|
||||
Host=127.0.0.1
|
||||
AuthType=1
|
||||
GroupName=remote_users
|
||||
GroupPwd=password
|
||||
enc_GroupPwd=
|
||||
EnableISPConnect=0
|
||||
ISPConnectType=0
|
||||
ISPConnect=
|
||||
ISPCommand=
|
||||
Username=Remote_User
|
||||
UserPassword=user_password
|
||||
enc_UserPassword=
|
||||
SaveUserPassword=0
|
||||
EnableBackup=0
|
||||
BackupServer=
|
||||
CertStore=0
|
||||
CertName=
|
||||
CertPath=
|
||||
CertSubjectName=
|
||||
CertSerialHash=00000000000000000000000000000000
|
||||
DHGroup=2
|
||||
ForceKeepAlives=1
|
||||
NTDomain=
|
||||
EnableMSLogon=1
|
||||
MSLogonType=0
|
||||
EnableNat=1
|
||||
TunnelingMode=0
|
||||
TcpTunnelingPort=10000
|
||||
SendCertChain=0
|
||||
PeerTimeout=90
|
||||
|
|
@ -0,0 +1,8 @@
|
|||
|
||||
This is an example script that can be called via _updown to allows
|
||||
a new cloud/instance/host to send its raw RSA key to a DNS server.
|
||||
|
||||
This IPSECKEY record can then be used for Opportunistic IPsec
|
||||
|
||||
The authentication for the DNS update happens using TSIG
|
||||
|
||||
|
|
@ -0,0 +1,5 @@
|
|||
key "dyn.nohats.ca" {
|
||||
algorithm hmac-sha256;
|
||||
secret "NotTheRealSecretKeyObviously";
|
||||
};
|
||||
|
||||
|
|
@ -0,0 +1,69 @@
|
|||
#!/bin/bash -e
|
||||
|
||||
# Copyright (C) 2017 Paul Wouters <paul@libreswan.org>
|
||||
#
|
||||
# This program is free software; you can redistribute it and/or modify it
|
||||
# under the terms of the GNU General Public License as published by the
|
||||
# Free Software Foundation; either version 2 of the License, or (at your
|
||||
# option) any later version. See <https://www.gnu.org/licenses/gpl2.txt>.
|
||||
#
|
||||
# This program is distributed in the hope that it will be useful, but
|
||||
# WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY
|
||||
# or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License
|
||||
# for more details.
|
||||
|
||||
# TSIG keys can be generated using bind's ddns-confgen command
|
||||
#
|
||||
#KEY=/etc/bind/keys/yourddns.key
|
||||
|
||||
KEY="$(dirname $0)/dyn.nohats.ca.key"
|
||||
|
||||
echo "Using keyfile: $KEY"
|
||||
|
||||
# The zone in which the update happens
|
||||
#ZONE=yourdomain
|
||||
ZONE=dyn.nohats.ca
|
||||
|
||||
# TTL to use for new DNS entries
|
||||
TTL=300
|
||||
|
||||
# Name of Dyn DNS update utility (eg nsupdate, kupdate, etc)
|
||||
DNSUPDATER=nsupdate
|
||||
|
||||
# The name/IP of the server to send the Dynamic DNS update to
|
||||
#DNSSERVER=ns0.yourdomain.com
|
||||
# Demo server that accepts DYN DNS updates for the zone dyn.nohats.ca
|
||||
DNSSERVER=hiddenmaster.nohats.ca
|
||||
|
||||
# Your IP address to update the A and/or PTR records for
|
||||
# 8.8.8.8 is a random IP to get the default route
|
||||
MYIP=$(ip route get 8.8.8.8 | head -1 | awk '{print $7}')
|
||||
|
||||
# Your hostname, default is to use hostname.ZONE
|
||||
MYNAME="$(hostname -s).$ZONE"
|
||||
# If you don't have a raw RSA key, generate one using:
|
||||
# ipsec newhostkey --output /etc/ipsec.d/hostkey.secrets
|
||||
#
|
||||
# Get our raw RSA key and generate the IPSECKEY syntax
|
||||
CKAID="$(ipsec showhostkey --list | head -1 | sed 's/^.*://')"
|
||||
IPSECKEY="$(ipsec showhostkey --ipseckey --ckaid $CKAID)"
|
||||
|
||||
#echo $MYNAME
|
||||
#echo $IPSECKEY
|
||||
KEYDATA=$(echo $IPSECKEY | sed "s/^.*IPSECKEY//")
|
||||
echo $KEYDATA
|
||||
|
||||
echo "Updating $MYNAME A record to $MYIP and sending IPSECKEY using server $DNSSERVER"
|
||||
|
||||
echo "->update add IPSECKEY $IPSECKEY"
|
||||
|
||||
cat <<EOF | $DNSUPDATER -k "$KEY"
|
||||
server $DNSSERVER
|
||||
zone $ZONE
|
||||
update delete $MYNAME A
|
||||
update add $MYNAME $TTL A $MYIP
|
||||
update delete $MYNAME IPSECKEY
|
||||
update add $MYNAME $TTL IPSECKEY $KEYDATA
|
||||
send
|
||||
EOF
|
||||
|
||||
|
|
@ -0,0 +1,339 @@
|
|||
GNU GENERAL PUBLIC LICENSE
|
||||
Version 2, June 1991
|
||||
|
||||
Copyright (C) 1989, 1991 Free Software Foundation, Inc.,
|
||||
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA
|
||||
Everyone is permitted to copy and distribute verbatim copies
|
||||
of this license document, but changing it is not allowed.
|
||||
|
||||
Preamble
|
||||
|
||||
The licenses for most software are designed to take away your
|
||||
freedom to share and change it. By contrast, the GNU General Public
|
||||
License is intended to guarantee your freedom to share and change free
|
||||
software--to make sure the software is free for all its users. This
|
||||
General Public License applies to most of the Free Software
|
||||
Foundation's software and to any other program whose authors commit to
|
||||
using it. (Some other Free Software Foundation software is covered by
|
||||
the GNU Lesser General Public License instead.) You can apply it to
|
||||
your programs, too.
|
||||
|
||||
When we speak of free software, we are referring to freedom, not
|
||||
price. Our General Public Licenses are designed to make sure that you
|
||||
have the freedom to distribute copies of free software (and charge for
|
||||
this service if you wish), that you receive source code or can get it
|
||||
if you want it, that you can change the software or use pieces of it
|
||||
in new free programs; and that you know you can do these things.
|
||||
|
||||
To protect your rights, we need to make restrictions that forbid
|
||||
anyone to deny you these rights or to ask you to surrender the rights.
|
||||
These restrictions translate to certain responsibilities for you if you
|
||||
distribute copies of the software, or if you modify it.
|
||||
|
||||
For example, if you distribute copies of such a program, whether
|
||||
gratis or for a fee, you must give the recipients all the rights that
|
||||
you have. You must make sure that they, too, receive or can get the
|
||||
source code. And you must show them these terms so they know their
|
||||
rights.
|
||||
|
||||
We protect your rights with two steps: (1) copyright the software, and
|
||||
(2) offer you this license which gives you legal permission to copy,
|
||||
distribute and/or modify the software.
|
||||
|
||||
Also, for each author's protection and ours, we want to make certain
|
||||
that everyone understands that there is no warranty for this free
|
||||
software. If the software is modified by someone else and passed on, we
|
||||
want its recipients to know that what they have is not the original, so
|
||||
that any problems introduced by others will not reflect on the original
|
||||
authors' reputations.
|
||||
|
||||
Finally, any free program is threatened constantly by software
|
||||
patents. We wish to avoid the danger that redistributors of a free
|
||||
program will individually obtain patent licenses, in effect making the
|
||||
program proprietary. To prevent this, we have made it clear that any
|
||||
patent must be licensed for everyone's free use or not licensed at all.
|
||||
|
||||
The precise terms and conditions for copying, distribution and
|
||||
modification follow.
|
||||
|
||||
GNU GENERAL PUBLIC LICENSE
|
||||
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
|
||||
|
||||
0. This License applies to any program or other work which contains
|
||||
a notice placed by the copyright holder saying it may be distributed
|
||||
under the terms of this General Public License. The "Program", below,
|
||||
refers to any such program or work, and a "work based on the Program"
|
||||
means either the Program or any derivative work under copyright law:
|
||||
that is to say, a work containing the Program or a portion of it,
|
||||
either verbatim or with modifications and/or translated into another
|
||||
language. (Hereinafter, translation is included without limitation in
|
||||
the term "modification".) Each licensee is addressed as "you".
|
||||
|
||||
Activities other than copying, distribution and modification are not
|
||||
covered by this License; they are outside its scope. The act of
|
||||
running the Program is not restricted, and the output from the Program
|
||||
is covered only if its contents constitute a work based on the
|
||||
Program (independent of having been made by running the Program).
|
||||
Whether that is true depends on what the Program does.
|
||||
|
||||
1. You may copy and distribute verbatim copies of the Program's
|
||||
source code as you receive it, in any medium, provided that you
|
||||
conspicuously and appropriately publish on each copy an appropriate
|
||||
copyright notice and disclaimer of warranty; keep intact all the
|
||||
notices that refer to this License and to the absence of any warranty;
|
||||
and give any other recipients of the Program a copy of this License
|
||||
along with the Program.
|
||||
|
||||
You may charge a fee for the physical act of transferring a copy, and
|
||||
you may at your option offer warranty protection in exchange for a fee.
|
||||
|
||||
2. You may modify your copy or copies of the Program or any portion
|
||||
of it, thus forming a work based on the Program, and copy and
|
||||
distribute such modifications or work under the terms of Section 1
|
||||
above, provided that you also meet all of these conditions:
|
||||
|
||||
a) You must cause the modified files to carry prominent notices
|
||||
stating that you changed the files and the date of any change.
|
||||
|
||||
b) You must cause any work that you distribute or publish, that in
|
||||
whole or in part contains or is derived from the Program or any
|
||||
part thereof, to be licensed as a whole at no charge to all third
|
||||
parties under the terms of this License.
|
||||
|
||||
c) If the modified program normally reads commands interactively
|
||||
when run, you must cause it, when started running for such
|
||||
interactive use in the most ordinary way, to print or display an
|
||||
announcement including an appropriate copyright notice and a
|
||||
notice that there is no warranty (or else, saying that you provide
|
||||
a warranty) and that users may redistribute the program under
|
||||
these conditions, and telling the user how to view a copy of this
|
||||
License. (Exception: if the Program itself is interactive but
|
||||
does not normally print such an announcement, your work based on
|
||||
the Program is not required to print an announcement.)
|
||||
|
||||
These requirements apply to the modified work as a whole. If
|
||||
identifiable sections of that work are not derived from the Program,
|
||||
and can be reasonably considered independent and separate works in
|
||||
themselves, then this License, and its terms, do not apply to those
|
||||
sections when you distribute them as separate works. But when you
|
||||
distribute the same sections as part of a whole which is a work based
|
||||
on the Program, the distribution of the whole must be on the terms of
|
||||
this License, whose permissions for other licensees extend to the
|
||||
entire whole, and thus to each and every part regardless of who wrote it.
|
||||
|
||||
Thus, it is not the intent of this section to claim rights or contest
|
||||
your rights to work written entirely by you; rather, the intent is to
|
||||
exercise the right to control the distribution of derivative or
|
||||
collective works based on the Program.
|
||||
|
||||
In addition, mere aggregation of another work not based on the Program
|
||||
with the Program (or with a work based on the Program) on a volume of
|
||||
a storage or distribution medium does not bring the other work under
|
||||
the scope of this License.
|
||||
|
||||
3. You may copy and distribute the Program (or a work based on it,
|
||||
under Section 2) in object code or executable form under the terms of
|
||||
Sections 1 and 2 above provided that you also do one of the following:
|
||||
|
||||
a) Accompany it with the complete corresponding machine-readable
|
||||
source code, which must be distributed under the terms of Sections
|
||||
1 and 2 above on a medium customarily used for software interchange; or,
|
||||
|
||||
b) Accompany it with a written offer, valid for at least three
|
||||
years, to give any third party, for a charge no more than your
|
||||
cost of physically performing source distribution, a complete
|
||||
machine-readable copy of the corresponding source code, to be
|
||||
distributed under the terms of Sections 1 and 2 above on a medium
|
||||
customarily used for software interchange; or,
|
||||
|
||||
c) Accompany it with the information you received as to the offer
|
||||
to distribute corresponding source code. (This alternative is
|
||||
allowed only for noncommercial distribution and only if you
|
||||
received the program in object code or executable form with such
|
||||
an offer, in accord with Subsection b above.)
|
||||
|
||||
The source code for a work means the preferred form of the work for
|
||||
making modifications to it. For an executable work, complete source
|
||||
code means all the source code for all modules it contains, plus any
|
||||
associated interface definition files, plus the scripts used to
|
||||
control compilation and installation of the executable. However, as a
|
||||
special exception, the source code distributed need not include
|
||||
anything that is normally distributed (in either source or binary
|
||||
form) with the major components (compiler, kernel, and so on) of the
|
||||
operating system on which the executable runs, unless that component
|
||||
itself accompanies the executable.
|
||||
|
||||
If distribution of executable or object code is made by offering
|
||||
access to copy from a designated place, then offering equivalent
|
||||
access to copy the source code from the same place counts as
|
||||
distribution of the source code, even though third parties are not
|
||||
compelled to copy the source along with the object code.
|
||||
|
||||
4. You may not copy, modify, sublicense, or distribute the Program
|
||||
except as expressly provided under this License. Any attempt
|
||||
otherwise to copy, modify, sublicense or distribute the Program is
|
||||
void, and will automatically terminate your rights under this License.
|
||||
However, parties who have received copies, or rights, from you under
|
||||
this License will not have their licenses terminated so long as such
|
||||
parties remain in full compliance.
|
||||
|
||||
5. You are not required to accept this License, since you have not
|
||||
signed it. However, nothing else grants you permission to modify or
|
||||
distribute the Program or its derivative works. These actions are
|
||||
prohibited by law if you do not accept this License. Therefore, by
|
||||
modifying or distributing the Program (or any work based on the
|
||||
Program), you indicate your acceptance of this License to do so, and
|
||||
all its terms and conditions for copying, distributing or modifying
|
||||
the Program or works based on it.
|
||||
|
||||
6. Each time you redistribute the Program (or any work based on the
|
||||
Program), the recipient automatically receives a license from the
|
||||
original licensor to copy, distribute or modify the Program subject to
|
||||
these terms and conditions. You may not impose any further
|
||||
restrictions on the recipients' exercise of the rights granted herein.
|
||||
You are not responsible for enforcing compliance by third parties to
|
||||
this License.
|
||||
|
||||
7. If, as a consequence of a court judgment or allegation of patent
|
||||
infringement or for any other reason (not limited to patent issues),
|
||||
conditions are imposed on you (whether by court order, agreement or
|
||||
otherwise) that contradict the conditions of this License, they do not
|
||||
excuse you from the conditions of this License. If you cannot
|
||||
distribute so as to satisfy simultaneously your obligations under this
|
||||
License and any other pertinent obligations, then as a consequence you
|
||||
may not distribute the Program at all. For example, if a patent
|
||||
license would not permit royalty-free redistribution of the Program by
|
||||
all those who receive copies directly or indirectly through you, then
|
||||
the only way you could satisfy both it and this License would be to
|
||||
refrain entirely from distribution of the Program.
|
||||
|
||||
If any portion of this section is held invalid or unenforceable under
|
||||
any particular circumstance, the balance of the section is intended to
|
||||
apply and the section as a whole is intended to apply in other
|
||||
circumstances.
|
||||
|
||||
It is not the purpose of this section to induce you to infringe any
|
||||
patents or other property right claims or to contest validity of any
|
||||
such claims; this section has the sole purpose of protecting the
|
||||
integrity of the free software distribution system, which is
|
||||
implemented by public license practices. Many people have made
|
||||
generous contributions to the wide range of software distributed
|
||||
through that system in reliance on consistent application of that
|
||||
system; it is up to the author/donor to decide if he or she is willing
|
||||
to distribute software through any other system and a licensee cannot
|
||||
impose that choice.
|
||||
|
||||
This section is intended to make thoroughly clear what is believed to
|
||||
be a consequence of the rest of this License.
|
||||
|
||||
8. If the distribution and/or use of the Program is restricted in
|
||||
certain countries either by patents or by copyrighted interfaces, the
|
||||
original copyright holder who places the Program under this License
|
||||
may add an explicit geographical distribution limitation excluding
|
||||
those countries, so that distribution is permitted only in or among
|
||||
countries not thus excluded. In such case, this License incorporates
|
||||
the limitation as if written in the body of this License.
|
||||
|
||||
9. The Free Software Foundation may publish revised and/or new versions
|
||||
of the General Public License from time to time. Such new versions will
|
||||
be similar in spirit to the present version, but may differ in detail to
|
||||
address new problems or concerns.
|
||||
|
||||
Each version is given a distinguishing version number. If the Program
|
||||
specifies a version number of this License which applies to it and "any
|
||||
later version", you have the option of following the terms and conditions
|
||||
either of that version or of any later version published by the Free
|
||||
Software Foundation. If the Program does not specify a version number of
|
||||
this License, you may choose any version ever published by the Free Software
|
||||
Foundation.
|
||||
|
||||
10. If you wish to incorporate parts of the Program into other free
|
||||
programs whose distribution conditions are different, write to the author
|
||||
to ask for permission. For software which is copyrighted by the Free
|
||||
Software Foundation, write to the Free Software Foundation; we sometimes
|
||||
make exceptions for this. Our decision will be guided by the two goals
|
||||
of preserving the free status of all derivatives of our free software and
|
||||
of promoting the sharing and reuse of software generally.
|
||||
|
||||
NO WARRANTY
|
||||
|
||||
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY
|
||||
FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN
|
||||
OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES
|
||||
PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED
|
||||
OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF
|
||||
MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS
|
||||
TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE
|
||||
PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING,
|
||||
REPAIR OR CORRECTION.
|
||||
|
||||
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING
|
||||
WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR
|
||||
REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES,
|
||||
INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING
|
||||
OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED
|
||||
TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY
|
||||
YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER
|
||||
PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE
|
||||
POSSIBILITY OF SUCH DAMAGES.
|
||||
|
||||
END OF TERMS AND CONDITIONS
|
||||
|
||||
How to Apply These Terms to Your New Programs
|
||||
|
||||
If you develop a new program, and you want it to be of the greatest
|
||||
possible use to the public, the best way to achieve this is to make it
|
||||
free software which everyone can redistribute and change under these terms.
|
||||
|
||||
To do so, attach the following notices to the program. It is safest
|
||||
to attach them to the start of each source file to most effectively
|
||||
convey the exclusion of warranty; and each file should have at least
|
||||
the "copyright" line and a pointer to where the full notice is found.
|
||||
|
||||
<one line to give the program's name and a brief idea of what it does.>
|
||||
Copyright (C) <year> <name of author>
|
||||
|
||||
This program is free software; you can redistribute it and/or modify
|
||||
it under the terms of the GNU General Public License as published by
|
||||
the Free Software Foundation; either version 2 of the License, or
|
||||
(at your option) any later version.
|
||||
|
||||
This program is distributed in the hope that it will be useful,
|
||||
but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
GNU General Public License for more details.
|
||||
|
||||
You should have received a copy of the GNU General Public License along
|
||||
with this program; if not, write to the Free Software Foundation, Inc.,
|
||||
51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
|
||||
|
||||
Also add information on how to contact you by electronic and paper mail.
|
||||
|
||||
If the program is interactive, make it output a short notice like this
|
||||
when it starts in an interactive mode:
|
||||
|
||||
Gnomovision version 69, Copyright (C) year name of author
|
||||
Gnomovision comes with ABSOLUTELY NO WARRANTY; for details type `show w'.
|
||||
This is free software, and you are welcome to redistribute it
|
||||
under certain conditions; type `show c' for details.
|
||||
|
||||
The hypothetical commands `show w' and `show c' should show the appropriate
|
||||
parts of the General Public License. Of course, the commands you use may
|
||||
be called something other than `show w' and `show c'; they could even be
|
||||
mouse-clicks or menu items--whatever suits your program.
|
||||
|
||||
You should also get your employer (if you work as a programmer) or your
|
||||
school, if any, to sign a "copyright disclaimer" for the program, if
|
||||
necessary. Here is a sample; alter the names:
|
||||
|
||||
Yoyodyne, Inc., hereby disclaims all copyright interest in the program
|
||||
`Gnomovision' (which makes passes at compilers) written by James Hacker.
|
||||
|
||||
<signature of Ty Coon>, 1 April 1989
|
||||
Ty Coon, President of Vice
|
||||
|
||||
This General Public License does not permit incorporating your program into
|
||||
proprietary programs. If your program is a subroutine library, you may
|
||||
consider it more useful to permit linking proprietary applications with the
|
||||
library. If this is what you want to do, use the GNU Lesser General
|
||||
Public License instead of this License.
|
||||
|
|
@ -0,0 +1,8 @@
|
|||
|
||||
getpeercon_server.c written by Paul Moore, licensed as GPLv2
|
||||
|
||||
getpeercon_server displays the SElinux networking context (netlabel)
|
||||
of an incoming connection. This is used for testing labeled-ipsec.
|
||||
|
||||
See testing/pluto/labeled-ipsec-*
|
||||
|
||||
|
|
@ -0,0 +1,208 @@
|
|||
/*
|
||||
* getpeercon_server: simple INET/INET6/UNIX socket getpeercon(3) test server
|
||||
*
|
||||
* compile: gcc -Wall -o getpeercon_server -lselinux getpeercon_server.c
|
||||
*
|
||||
* Copyright Paul Moore <paul@paul-moore.com>
|
||||
*
|
||||
* Paul Wouters <pwouters@redhat.com> added simplistic quit option. If
|
||||
* the server receives the text "quit" it will quit.
|
||||
*/
|
||||
|
||||
/*
|
||||
* (c) Copyright Hewlett-Packard Development Company, L.P., 2008, 2010
|
||||
* (c) Copyright Red Hat, 2012
|
||||
*
|
||||
* This program is free software: you can redistribute it and/or modify
|
||||
* it under the terms of version 2 of the GNU General Public License as
|
||||
* published by the Free Software Foundation.
|
||||
*
|
||||
* This program is distributed in the hope that it will be useful,
|
||||
* but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
* GNU General Public License for more details.
|
||||
*
|
||||
* You should have received a copy of the GNU General Public License
|
||||
* along with this program. If not, see <http://www.gnu.org/licenses/>.
|
||||
*/
|
||||
|
||||
#include <stdlib.h>
|
||||
#include <stdio.h>
|
||||
#include <string.h>
|
||||
#include <errno.h>
|
||||
#include <unistd.h>
|
||||
#include <sys/types.h>
|
||||
#include <sys/socket.h>
|
||||
#include <netinet/in.h>
|
||||
#include <arpa/inet.h>
|
||||
#include <sys/un.h>
|
||||
#include <selinux/selinux.h>
|
||||
#include <selinux/context.h>
|
||||
|
||||
#define UNIX_PATH_MAX 108
|
||||
#define LISTEN_QUEUE 1
|
||||
#define RECV_BUF_LEN 1024
|
||||
|
||||
/**
|
||||
* main
|
||||
*/
|
||||
int main(int argc, char *argv[])
|
||||
{
|
||||
int rc;
|
||||
short srv_sock_port;
|
||||
int srv_sock;
|
||||
const int true_const = 1;
|
||||
char *srv_sock_path = NULL;
|
||||
|
||||
if (argc != 2) {
|
||||
fprintf(stderr, "usage: %s <port|path>\n", argv[0]);
|
||||
return 1;
|
||||
}
|
||||
|
||||
srv_sock_port = atoi(argv[1]);
|
||||
if (srv_sock_port == 0)
|
||||
srv_sock_path = argv[1];
|
||||
|
||||
{
|
||||
security_context_t ctx;
|
||||
int rc = getcon(&ctx);
|
||||
|
||||
fprintf(stderr, "-> running as %s\n",
|
||||
rc < 0 ? "NO_CONTEXT" : ctx);
|
||||
if (rc >= 0)
|
||||
freecon(ctx);
|
||||
}
|
||||
|
||||
fprintf(stderr, "-> creating socket ... ");
|
||||
if (srv_sock_path == NULL)
|
||||
srv_sock = socket(AF_INET6, SOCK_STREAM, IPPROTO_TCP);
|
||||
else
|
||||
srv_sock = socket(AF_UNIX, SOCK_STREAM, 0);
|
||||
if (srv_sock < 0) {
|
||||
fprintf(stderr, "socket(2) error: %s\n", strerror(errno));
|
||||
return 1;
|
||||
}
|
||||
rc = setsockopt(srv_sock,
|
||||
SOL_SOCKET, SO_REUSEADDR, &true_const, sizeof(true_const));
|
||||
if (rc < 0) {
|
||||
fprintf(stderr, "setsockopt(2) error: %s\n", strerror(errno));
|
||||
return 1;
|
||||
}
|
||||
fprintf(stderr, "ok\n");
|
||||
|
||||
if (srv_sock_path == NULL) {
|
||||
struct sockaddr_in6 srv_sock_addr;
|
||||
|
||||
fprintf(stderr, "-> listening on TCP port %d ... ",
|
||||
srv_sock_port);
|
||||
memset(&srv_sock_addr, 0, sizeof(srv_sock_addr));
|
||||
srv_sock_addr.sin6_family = AF_INET6;
|
||||
#ifdef NEED_SIN_LEN
|
||||
srv_sock_addr.sin6_len = sizeof(struct sockaddr_in6);
|
||||
#endif
|
||||
memcpy(&srv_sock_addr.sin6_addr, &in6addr_any,
|
||||
sizeof(in6addr_any));
|
||||
srv_sock_addr.sin6_port = htons(srv_sock_port);
|
||||
rc = bind(srv_sock, (struct sockaddr *)&srv_sock_addr,
|
||||
sizeof(srv_sock_addr));
|
||||
} else {
|
||||
struct sockaddr_un srv_sock_addr;
|
||||
|
||||
fprintf(stderr, "-> listening on UNIX socket %s ... ",
|
||||
srv_sock_path);
|
||||
srv_sock_addr.sun_family = AF_UNIX;
|
||||
#ifdef NEED_SIN_LEN
|
||||
#error how do we set srv_sock_addr.sun_len?
|
||||
#endif
|
||||
/* make .sun_path both NUL-padded and NUL-terminated */
|
||||
strncpy(srv_sock_addr.sun_path, srv_sock_path, UNIX_PATH_MAX-1);
|
||||
srv_sock_addr.sun_path[UNIX_PATH_MAX - 1] = '\0';
|
||||
rc = bind(srv_sock, (struct sockaddr *)&srv_sock_addr,
|
||||
sizeof(srv_sock_addr));
|
||||
}
|
||||
if (rc < 0) {
|
||||
fprintf(stderr, "bind(2) error: %s\n", strerror(errno));
|
||||
return 1;
|
||||
}
|
||||
|
||||
rc = listen(srv_sock, LISTEN_QUEUE);
|
||||
if (rc < 0) {
|
||||
fprintf(stderr, "listen(2) error: %s\n", strerror(errno));
|
||||
return 1;
|
||||
} else
|
||||
fprintf(stderr, "ok\n");
|
||||
|
||||
fprintf(stderr, "-> waiting ... ");
|
||||
fflush(stdout);
|
||||
/* loop forever */
|
||||
for (;;) {
|
||||
int cli_sock;
|
||||
struct sockaddr_storage cli_sock_saddr;
|
||||
struct sockaddr *const cli_sock_addr = (struct sockaddr *)&cli_sock_saddr;
|
||||
struct sockaddr_in6 *const cli_sock_6addr = (struct sockaddr_in6 *)&cli_sock_saddr;
|
||||
socklen_t cli_sock_addr_len;
|
||||
char cli_sock_addr_str[INET6_ADDRSTRLEN + 1];
|
||||
security_context_t ctx;
|
||||
char *ctx_str;
|
||||
|
||||
//fflush(stdout);
|
||||
memset(&cli_sock_saddr, 0, sizeof(cli_sock_saddr));
|
||||
cli_sock_addr_len = sizeof(cli_sock_saddr);
|
||||
cli_sock = accept(srv_sock, cli_sock_addr, &cli_sock_addr_len);
|
||||
if (cli_sock < 0) {
|
||||
fprintf(stderr, "accept(2) error: %s\n", strerror(errno));
|
||||
continue;
|
||||
}
|
||||
rc = getpeercon(cli_sock, &ctx);
|
||||
ctx_str = rc < 0 ? "NO_CONTEXT" : ctx;
|
||||
|
||||
switch (cli_sock_saddr.ss_family) {
|
||||
case AF_INET6:
|
||||
if (IN6_IS_ADDR_V4MAPPED(&cli_sock_6addr->sin6_addr)) {
|
||||
inet_ntop(AF_INET,
|
||||
&cli_sock_6addr->sin6_addr.s6_addr32[3],
|
||||
cli_sock_addr_str, sizeof(cli_sock_addr_str));
|
||||
} else {
|
||||
inet_ntop(cli_sock_6addr->sin6_family,
|
||||
&cli_sock_6addr->sin6_addr,
|
||||
cli_sock_addr_str, sizeof(cli_sock_addr_str));
|
||||
}
|
||||
fprintf(stderr, "<- connect(%s,%s)\n",
|
||||
cli_sock_addr_str, ctx_str);
|
||||
break;
|
||||
|
||||
case AF_UNIX:
|
||||
fprintf(stderr, "connect(UNIX,%s)\n", ctx_str);
|
||||
break;
|
||||
|
||||
default:
|
||||
fprintf(stderr, "connect(%d,%s)\n",
|
||||
cli_sock_saddr.ss_family, ctx_str);
|
||||
}
|
||||
|
||||
if (rc >= 0)
|
||||
freecon(ctx);
|
||||
|
||||
for (;;) {
|
||||
char buffer[RECV_BUF_LEN + 1];
|
||||
|
||||
rc = recv(cli_sock, buffer, sizeof(buffer) - 1, 0);
|
||||
if (rc < 0) {
|
||||
fprintf(stderr, "recv(2) error: %s\n", strerror(errno));
|
||||
break;
|
||||
} else if (rc == 0) {
|
||||
break;
|
||||
} else {
|
||||
buffer[rc] = '\0';
|
||||
/* ??? should this format include a \n? */
|
||||
printf(" %s", buffer);
|
||||
if (strcmp(buffer, "quit") == 0)
|
||||
break;
|
||||
}
|
||||
}
|
||||
close(cli_sock);
|
||||
fprintf(stderr, "-> connection closed\n");
|
||||
}
|
||||
|
||||
return 0;
|
||||
}
|
||||
|
|
@ -0,0 +1,13 @@
|
|||
LIBRESWANSRCDIR=../..
|
||||
-include ${LIBRESWANSRCDIR}/Makefile.inc
|
||||
CFLAGS += -I${LIBRESWANSRCDIR}/include
|
||||
|
||||
SOURCE=saref.c
|
||||
TARGET=libsaref.so
|
||||
|
||||
${TARGET}: ${SOURCE}
|
||||
$(CC) ${CFLAGS} -fPIC -o $@ -shared -ldl ${SOURCE}
|
||||
|
||||
.PHONY: clean
|
||||
clean:
|
||||
rm -f *~ ${TARGET}
|
||||
|
|
@ -0,0 +1,8 @@
|
|||
This tool is used for testing the setsockopt IP_IPSEC_BINDREF option
|
||||
which allows a socket to be "bound" to a SAref. Each packet sent on
|
||||
that socket, as long as it's routed through mast0, will use the SA
|
||||
associated with the SAref. Example use case:
|
||||
|
||||
saref 123 nc 192.168.0.1 80
|
||||
|
||||
given that 123 is a valid refhim value seen in ipsec auto --status.
|
||||
|
|
@ -0,0 +1,33 @@
|
|||
#!/bin/sh
|
||||
set -e
|
||||
|
||||
do_help() {
|
||||
cat <<END
|
||||
saref - bind process to given SAref
|
||||
|
||||
saref <saref> <command> <options...>
|
||||
|
||||
END
|
||||
exit 0
|
||||
}
|
||||
|
||||
[ -z "$1" ] && do_help
|
||||
|
||||
case "$1" in
|
||||
-h|--help)
|
||||
do_help
|
||||
;;
|
||||
esac
|
||||
|
||||
export IPSEC_SAREF="$1"
|
||||
shift
|
||||
|
||||
if [ "$IPSEC_SAREF" -lt 0 ] || [ "$IPSEC_SAREF" -gt 65536 ] ; then
|
||||
echo >&2 "Error: invalid SAref value of $IPSEC_SAREF"
|
||||
exit 1
|
||||
fi
|
||||
|
||||
dir=$(dirname $0)
|
||||
|
||||
export LD_PRELOAD="$dir/libsaref.so $LD_PRELOAD"
|
||||
exec ${@}
|
||||
|
|
@ -0,0 +1,46 @@
|
|||
#define _GNU_SOURCE
|
||||
#include <stdio.h>
|
||||
#include <stdlib.h>
|
||||
#include <unistd.h>
|
||||
#include <dlfcn.h>
|
||||
#include <sys/types.h>
|
||||
#include <sys/socket.h>
|
||||
#include <netinet/in.h>
|
||||
#include <netinet/ip.h>
|
||||
#include <ipsec_saref.h>
|
||||
|
||||
typedef int (*socket_fn)(int, int, int);
|
||||
static socket_fn real_socket = NULL;
|
||||
static int saref = 0;
|
||||
#define UNASSIGNED_SAREF 0
|
||||
#define INVALID_SAREF (-1)
|
||||
|
||||
int socket(int domain, int type, int protocol)
|
||||
{
|
||||
int sk, rc;
|
||||
|
||||
if (real_socket == NULL)
|
||||
real_socket = (socket_fn)dlsym(RTLD_NEXT, "socket");
|
||||
|
||||
sk = real_socket(domain, type, protocol);
|
||||
|
||||
if (saref == UNASSIGNED_SAREF) {
|
||||
const char *str;
|
||||
|
||||
saref = INVALID_SAREF;
|
||||
str = getenv("IPSEC_SAREF");
|
||||
if (str != NULL) {
|
||||
char tmp = 0;
|
||||
|
||||
rc = sscanf(str, "%u%c", &saref, &tmp);
|
||||
if (rc != 1)
|
||||
saref = INVALID_SAREF;
|
||||
}
|
||||
}
|
||||
|
||||
if (saref != UNASSIGNED_SAREF && saref != INVALID_SAREF)
|
||||
(void) setsockopt(sk, IPPROTO_IP, IP_IPSEC_BINDREF, &saref,
|
||||
sizeof(saref));
|
||||
|
||||
return sk;
|
||||
}
|
||||
|
|
@ -0,0 +1,157 @@
|
|||
|
||||
helper program to interop with non-rfc IPsec implementation of Lucent.
|
||||
|
||||
From Rolando:
|
||||
|
||||
Lucent's way to work around NATing is to change this:
|
||||
|
||||
| IP | whatever L4 proto | Payload |
|
||||
|
||||
where IP has the (IP source; IP dest) within it into this:
|
||||
|
||||
| IP | UDP:XXX | IP | whatever L4 proto | Payload |
|
||||
|
||||
where IP have the same (IP source; IP dest) within them and XXX is the
|
||||
configurable UDP port (default=501)
|
||||
|
||||
In a nutshell, they "tunnelize" all the traffic to/from the client and
|
||||
the gateway into a IP/UDP:XXX header
|
||||
|
||||
May be there are better ways to do it but using iptables QUEUE is the
|
||||
one we used to encapsulate/decapsulate. I thougth about adding it to
|
||||
LSW code as well as some code to make it manipulate iptables QUEUE stuff
|
||||
but got lost on it. :-(
|
||||
|
||||
|
||||
---------- Forwarded message ----------
|
||||
Date: Sun, 5 Apr 2009 10:36:54 -0700 (PDT)
|
||||
From: Rolando Zappacosta
|
||||
Cc: users@libreswan.org
|
||||
To: Paul Wouters <paul@xelerance.com>
|
||||
Subject: Re: [Libreswan Users] Connection against a Lucent FW success!!!! but may
|
||||
be there's still room for improvement
|
||||
|
||||
|
||||
Hi all,
|
||||
|
||||
I could finally manage to get LSW to work against a Lucen VPN Gateway
|
||||
even through NAT. So, in case someone else needs such connection,
|
||||
compile below code and then run this:
|
||||
|
||||
modprobe ip_queue
|
||||
UDP501encap &
|
||||
iptables -A OUTPUT -d IPofLucentGW -j QUEUE
|
||||
iptables -A INPUT -s IPofLucentGW -j QUEUE
|
||||
|
||||
before launching LSW as usual.
|
||||
|
||||
|
||||
> I discussed this subject here:
|
||||
>
|
||||
> http://lists.libreswan.org/pipermail/users/2008-February/014030.html
|
||||
> based on
|
||||
>> what I could capture under Windows, the relevant part
|
||||
> of it is:
|
||||
>> "I'm trying to connect OpenSwan to a Lucent
|
||||
> VPN Gateway, which according to
|
||||
>> its ASCII interpretation of its Vendor ID payload is:
|
||||
>>
|
||||
> 4C5647392E312E3235353A425249434B3A392E312E323535="LVG9.1.255:BRICK:9.1.255".
|
||||
> I
|
||||
>> can connect to it by means of the Lucent VPN Client
|
||||
> V7.1.2 on a Windows XP
|
||||
>> computer (Vendor ID=
|
||||
> 4C5643372E312E323A5850="LVC7.1.2:XP")."
|
||||
>
|
||||
> Thanks. Normally vendorids are md5sum's of some text,
|
||||
> though in this case
|
||||
> that does not seem to be the case. I added them as-is to
|
||||
> vendor.c for now.
|
||||
>
|
||||
>> Seems one can know the running version of the client
|
||||
> and server just looking
|
||||
>> on the vendor id part of an ASCII capture dump.
|
||||
>> Interesting thing is, as explained to you privatelly,
|
||||
> the way the PSK gets
|
||||
>> handled here. Under the LVC (windows) I had to
|
||||
> configure a PSK like:
|
||||
>> <MyCompanysPSK> where the real PSK is 9 ASCII
|
||||
> characters long. However, I
|
||||
>> could find that in order to have LSW establishing
|
||||
> phase 1 successfully I had to
|
||||
>> add the string "01234567890" as a trailer,
|
||||
> i.e. my ipsec.secrets looks like:
|
||||
>> !@#$% <MyCompanysGWipAddress> : PSK
|
||||
> "<MyCompanysPSK>01234567890"
|
||||
>>
|
||||
>> what gives a PSK of length 20. Not sure on how they
|
||||
> handle it but my guess is
|
||||
>> they just take the PSK the user configures, add the
|
||||
> string
|
||||
>> "01234567890123456789" and take the first 20
|
||||
> bytes of it. Easy way to hook you
|
||||
>> on their client while still keeping it simply to
|
||||
> develop.
|
||||
>>
|
||||
>> And I'm not sure if the user !@#$% is the one the
|
||||
> GW admin configured on it or
|
||||
>> if it's the way they handle it but whatever else I
|
||||
> configure, the GW just
|
||||
>> don't respond anything back to me.
|
||||
>
|
||||
> Thanks! I put a note of this in docs/lucent-client.txt, and
|
||||
> it will end up
|
||||
> in the new wiki once we have it online.
|
||||
>
|
||||
>>> Looks like a resend, you can ignore it.
|
||||
>> Strangely, I *always* do receive the duplicate packet
|
||||
> warning. Another
|
||||
>> interesting thing is Lucent's VPN client
|
||||
> doesn't exchange any CFG at all...
|
||||
>> I'm wondering now if I need it indeed. The server
|
||||
> sends it to me but seems
|
||||
>> like LSW only configures the local IP address based on
|
||||
> it. I supossed it was
|
||||
>> going to be able to configure something else, such as
|
||||
> DNS or things like that.
|
||||
>
|
||||
> Libreswan does support DNS/WINS via XAUTH/ModeConfig. Though
|
||||
> as a client, we
|
||||
> might be ignoring it, since we have no structured way of
|
||||
> modifying resolv.conf
|
||||
> in any modern way (eg dbus/networkmanager). I believe we
|
||||
> might only pass it
|
||||
> as env variables to the updown script.
|
||||
>
|
||||
>> The LVC do more things with no CFG at all, configures
|
||||
> the DNS and WINS servers
|
||||
>> for instance, something I'll need to do manually
|
||||
> via a script (or can it be
|
||||
>> made automatically somehow by LSW?)
|
||||
>
|
||||
> You can copy the stock _updown script and add resolv.conf
|
||||
> rewriting to it,
|
||||
> and configure the new script using leftupdown=
|
||||
>
|
||||
>>>> and this one from pluto's debug:
|
||||
>>>> 3) "Intranet" #1: XAUTH:
|
||||
> Unsupported attribute: INTERNAL_ADDRESS_EXPIRY
|
||||
>>> You can also ignore this. Libreswan does not
|
||||
> support INTERNAL_ADDRESS_EXPIRY,
|
||||
>>> so it won't drop the IP address or ask for a new
|
||||
> one.
|
||||
>> Same for "ignoring informational payload, type
|
||||
> IPSEC_RESPONDER_LIFETIME"
|
||||
>> above?
|
||||
>
|
||||
> Yes. the remote is telling us how long they will keep the
|
||||
> SA around. Libreswan
|
||||
> does not really care what the remote does. If the remote
|
||||
> wants to rekey, it
|
||||
> will and can do it anytime. We do enforce our own SA life
|
||||
> similarly.
|
||||
>
|
||||
> Paul
|
||||
|
||||
|
||||
|
||||
|
|
@ -0,0 +1,283 @@
|
|||
|
||||
|
||||
before launching LSW as usual.
|
||||
|
||||
RJZ - LNX UDP501 # cat UDP501encap.c
|
||||
/*
|
||||
* This code is GPL.
|
||||
* To compile: gcc UDP501encap.c -o UDP501encap -lipq
|
||||
*
|
||||
* Use as follows:
|
||||
*
|
||||
* modprobe ip_queue
|
||||
* UDP501encap &
|
||||
* iptables -A OUTPUT -d IPofLucentGW -j QUEUE
|
||||
* iptables -A INPUT -s IPofLucentGW -j QUEUE
|
||||
*/
|
||||
|
||||
#include <netinet/in.h>
|
||||
#include <arpa/inet.h>
|
||||
#include <linux/netfilter.h>
|
||||
#include <libipq.h>
|
||||
#include <stdio.h>
|
||||
#include <stdlib.h>
|
||||
#include <string.h>
|
||||
|
||||
#define BUFSIZE 2048
|
||||
#define BOOL int
|
||||
|
||||
#define DstPort 501
|
||||
#define DstPortHi (DstPort >> 8)
|
||||
#define DstPortLo (DstPort & 0x00FF)
|
||||
#define SrcPort 501
|
||||
#define SrcPortHi (SrcPort >> 8)
|
||||
#define SrcPortLo (SrcPort & 0x00FF)
|
||||
|
||||
typedef unsigned short u16;
|
||||
typedef unsigned long u32;
|
||||
|
||||
u16 ip_sum_calc(u16 len_ip_header, unsigned char buff[])
|
||||
{
|
||||
u16 word16;
|
||||
u32 sum = 0;
|
||||
u16 i;
|
||||
|
||||
// make 16 bit words out of every two adjacent 8 bit words in the packet
|
||||
// and add them up
|
||||
for (i = 0; i < len_ip_header; i = i + 2) {
|
||||
word16 = ((buff[i] << 8) & 0xFF00) + (buff[i + 1] & 0xFF);
|
||||
sum = sum + (u32) word16;
|
||||
}
|
||||
|
||||
// take only 16 bits out of the 32 bit sum and add up the carries
|
||||
while (sum >> 16)
|
||||
sum = (sum & 0xFFFF) + (sum >> 16);
|
||||
|
||||
// one's complement the result
|
||||
sum = ~sum;
|
||||
|
||||
return (u16) sum;
|
||||
}
|
||||
|
||||
static void die(struct ipq_handle *h)
|
||||
{
|
||||
ipq_perror("passer");
|
||||
ipq_destroy_handle(h);
|
||||
exit(1);
|
||||
}
|
||||
|
||||
int main(int argc, char **argv)
|
||||
{
|
||||
int status;
|
||||
unsigned char buf[BUFSIZE];
|
||||
struct ipq_handle *h;
|
||||
unsigned char *newPayload;
|
||||
u16 srcaddr[4], dstaddr[4];
|
||||
u16 newCS;
|
||||
int ip_header_len;
|
||||
u16 udp_len;
|
||||
int i;
|
||||
|
||||
h = ipq_create_handle(0, PF_INET);
|
||||
if (!h)
|
||||
die(h);
|
||||
|
||||
status = ipq_set_mode(h, IPQ_COPY_PACKET, BUFSIZE);
|
||||
if (status < 0)
|
||||
die(h);
|
||||
|
||||
do {
|
||||
status = ipq_read(h, buf, BUFSIZE, 0);
|
||||
if (status < 0)
|
||||
die(h);
|
||||
|
||||
switch (ipq_message_type(buf)) {
|
||||
case NLMSG_ERROR:
|
||||
fprintf(stderr, "Received error message %d\n",
|
||||
ipq_get_msgerr(buf));
|
||||
break;
|
||||
|
||||
case IPQM_PACKET:
|
||||
{
|
||||
ipq_packet_msg_t *m = ipq_get_packet(buf);
|
||||
//Enable this to debug the incoming/outgoing packets:
|
||||
//printf("0x%02x %s -> %s (%d)\n", m->payload[9], m->indev_name, m->outdev_name, m->data_len);
|
||||
|
||||
if (m->outdev_name[0] == 0x0) {
|
||||
// INPUT
|
||||
ip_header_len = (m->payload[0] & 0xF) * 4;
|
||||
u16 new_ip_len = m->data_len - ip_header_len -
|
||||
8;
|
||||
newPayload = malloc(new_ip_len);
|
||||
memcpy(newPayload,
|
||||
m->payload + ip_header_len + 8,
|
||||
new_ip_len);
|
||||
status = ipq_set_verdict(h, m->packet_id,
|
||||
NF_ACCEPT, new_ip_len,
|
||||
newPayload);
|
||||
free(newPayload);
|
||||
} else {
|
||||
u16 ip_len =
|
||||
(m->payload[2] << 8 & 0xff00) +
|
||||
(m->payload[3] & 0xff);
|
||||
ip_header_len = (m->payload[0] & 0xF) * 4;
|
||||
u16 new_ip_len = ip_len + ip_header_len + 8;
|
||||
newPayload = malloc(new_ip_len);
|
||||
// Copy prev packet
|
||||
char *dst = newPayload;
|
||||
char *org = m->payload;
|
||||
// Copy IP header
|
||||
memcpy(dst, org, ip_header_len);
|
||||
dst += ip_header_len;
|
||||
// Update IP length field
|
||||
newPayload[2] = new_ip_len >> 8;
|
||||
newPayload[3] = new_ip_len & 0x00ff;
|
||||
// Set IP protocol field to UDP
|
||||
newPayload[9] = 0x11;
|
||||
// Calculate and update IP cksum
|
||||
newPayload[10] = newPayload[11] = 0x00;
|
||||
newCS = ip_sum_calc(ip_header_len, newPayload);
|
||||
newPayload[10] = newCS >> 8;
|
||||
newPayload[11] = newCS & 0x00FF;
|
||||
// Create UDP header
|
||||
dst[0] = SrcPortHi; // src port
|
||||
dst[1] = SrcPortLo; // src port
|
||||
dst[2] = DstPortHi; // dst port
|
||||
dst[3] = DstPortLo; // dst port
|
||||
u16 new_udp_len = new_ip_len - ip_header_len;
|
||||
dst[4] = new_udp_len >> 8; // total len
|
||||
dst[5] = new_udp_len & 0x00ff; // total len
|
||||
dst[6] = 0x00; // Cksum
|
||||
dst[7] = 0x00; // Cksum
|
||||
dst += 8;
|
||||
// Clone the rest of the packet
|
||||
memcpy(dst, org, ip_len);
|
||||
status = ipq_set_verdict(h, m->packet_id,
|
||||
NF_ACCEPT, new_ip_len,
|
||||
newPayload);
|
||||
free(newPayload);
|
||||
}
|
||||
if (status < 0)
|
||||
die(h);
|
||||
break;
|
||||
}
|
||||
|
||||
default:
|
||||
fprintf(stderr, "Unknown message type!\n");
|
||||
break;
|
||||
}
|
||||
} while (1);
|
||||
|
||||
ipq_destroy_handle(h);
|
||||
return 0;
|
||||
}
|
||||
|
||||
/*
|
||||
>> I discussed this subject here:
|
||||
>>
|
||||
> http://lists.openswan.org/pipermail/users/2008-February/014030.html
|
||||
> based on
|
||||
>> what I could capture under Windows, the relevant part
|
||||
> of it is:
|
||||
>> "I'm trying to connect OpenSwan to a Lucent
|
||||
> VPN Gateway, which according to
|
||||
>> its ASCII interpretation of its Vendor ID payload is:
|
||||
>>
|
||||
> 4C5647392E312E3235353A425249434B3A392E312E323535="LVG9.1.255:BRICK:9.1.255".
|
||||
> I
|
||||
>> can connect to it by means of the Lucent VPN Client
|
||||
> V7.1.2 on a Windows XP
|
||||
>> computer (Vendor ID=
|
||||
> 4C5643372E312E323A5850="LVC7.1.2:XP")."
|
||||
>
|
||||
> Thanks. Normally vendorids are md5sum's of some text,
|
||||
> though in this case
|
||||
> that does not seem to be the case. I added them as-is to
|
||||
> vendor.c for now.
|
||||
>
|
||||
>> Seems one can know the running version of the client
|
||||
> and server just looking
|
||||
>> on the vendor id part of an ASCII capture dump.
|
||||
>> Interesting thing is, as explained to you privatelly,
|
||||
> the way the PSK gets
|
||||
>> handled here. Under the LVC (windows) I had to
|
||||
> configure a PSK like:
|
||||
>> <MyCompanysPSK> where the real PSK is 9 ASCII
|
||||
> characters long. However, I
|
||||
>> could find that in order to have LSW establishing
|
||||
> phase 1 successfully I had to
|
||||
>> add the string "01234567890" as a trailer,
|
||||
> i.e. my ipsec.secrets looks like:
|
||||
>> !@#$% <MyCompanysGWipAddress> : PSK
|
||||
> "<MyCompanysPSK>01234567890"
|
||||
>>
|
||||
>> what gives a PSK of length 20. Not sure on how they
|
||||
> handle it but my guess is
|
||||
>> they just take the PSK the user configures, add the
|
||||
> string
|
||||
>> "01234567890123456789" and take the first 20
|
||||
> bytes of it. Easy way to hook you
|
||||
>> on their client while still keeping it simply to
|
||||
> develop.
|
||||
>>
|
||||
>> And I'm not sure if the user !@#$% is the one the
|
||||
> GW admin configured on it or
|
||||
>> if it's the way they handle it but whatever else I
|
||||
> configure, the GW just
|
||||
>> don't respond anything back to me.
|
||||
>
|
||||
> Thanks! I put a note of this in docs/lucent-client.txt, and
|
||||
> it will end up
|
||||
> in the new wiki once we have it online.
|
||||
>
|
||||
>>> Looks like a resend, you can ignore it.
|
||||
>> Strangely, I *always* do receive the duplicate packet
|
||||
> warning. Another
|
||||
>> interesting thing is Lucent's VPN client
|
||||
> doesn't exchange any CFG at all...
|
||||
>> I'm wondering now if I need it indeed. The server
|
||||
> sends it to me but seems
|
||||
>> like LSW only configures the local IP address based on
|
||||
> it. I supossed it was
|
||||
>> going to be able to configure something else, such as
|
||||
> DNS or things like that.
|
||||
>
|
||||
> Libreswan does support DNS/WINS via XAUTH/ModeConfig. Though
|
||||
> as a client, we
|
||||
> might be ignoring it, since we have no structured way of
|
||||
> modifying resolv.conf
|
||||
> in any modern way (eg dbus/networkmanager). I believe we
|
||||
> might only pass it
|
||||
> as env variables to the updown script.
|
||||
>
|
||||
>> The LVC do more things with no CFG at all, configures
|
||||
> the DNS and WINS servers
|
||||
>> for instance, something I'll need to do manually
|
||||
> via a script (or can it be
|
||||
>> made automatically somehow by LSW?)
|
||||
>
|
||||
> You can copy the stock _updown script and add resolv.conf
|
||||
> rewriting to it,
|
||||
> and configure the new script using leftupdown=
|
||||
>
|
||||
>>>> and this one from pluto's debug:
|
||||
>>>> 3) "Intranet" #1: XAUTH:
|
||||
> Unsupported attribute: INTERNAL_ADDRESS_EXPIRY
|
||||
>>> You can also ignore this. Libreswan does not
|
||||
> support INTERNAL_ADDRESS_EXPIRY,
|
||||
>>> so it won't drop the IP address or ask for a new
|
||||
> one.
|
||||
>> Same for "ignoring informational payload, type
|
||||
> IPSEC_RESPONDER_LIFETIME"
|
||||
>> above?
|
||||
>
|
||||
> Yes. the remote is telling us how long they will keep the
|
||||
> SA around. Libreswan
|
||||
> does not really care what the remote does. If the remote
|
||||
> wants to rekey, it
|
||||
> will and can do it anytime. We do enforce our own SA life
|
||||
> similarly.
|
||||
>
|
||||
> Paul
|
||||
*/
|
||||
|
||||
|
|
@ -0,0 +1,6 @@
|
|||
|
||||
this is a libreswan plugin for munin.
|
||||
|
||||
See: http://munin-monitoring.org/
|
||||
|
||||
It requires libreswan 3.20 or later
|
||||
|
|
@ -0,0 +1,240 @@
|
|||
#!/usr/bin/python -tt
|
||||
|
||||
"""Munin plugin to monitor libreswan ipsec servers
|
||||
Copyright 2017, Kim B. Heino, b@bbbs.net, Foobar Oy
|
||||
Copyright 2017, Paul Wouters <paul@nohats.ca>
|
||||
License GPLv2+
|
||||
|
||||
This plugin requires Munin config /etc/munin/plugin-conf.d/libreswan:
|
||||
|
||||
[libreswan]
|
||||
user root
|
||||
|
||||
#%# capabilities=autoconf
|
||||
#%# family=auto
|
||||
"""
|
||||
|
||||
from __future__ import print_function, unicode_literals
|
||||
import subprocess
|
||||
import sys
|
||||
from collections import defaultdict
|
||||
|
||||
|
||||
def tree():
|
||||
"""Tree of defaultdicts"""
|
||||
return defaultdict(tree)
|
||||
|
||||
|
||||
def get_stats():
|
||||
"""Get statistics"""
|
||||
# Get status output
|
||||
try:
|
||||
pipe = subprocess.Popen(
|
||||
['/usr/sbin/ipsec', 'whack', '--globalstatus'],
|
||||
stdout=subprocess.PIPE,
|
||||
stderr=subprocess.STDOUT)
|
||||
output = pipe.communicate()[0]
|
||||
except OSError:
|
||||
return {}
|
||||
|
||||
# Parse output
|
||||
values = tree()
|
||||
for line in output.splitlines():
|
||||
prefix, val = line.split("=")
|
||||
prefix = prefix.split('.')
|
||||
pos = values
|
||||
for key in prefix[:-1]:
|
||||
pos = pos[key]
|
||||
pos[prefix[-1]] = val
|
||||
return values
|
||||
|
||||
|
||||
def derive_gauge(entry, value, config, graph_type):
|
||||
"""Print config or value"""
|
||||
if config:
|
||||
print('{}.label {}'.format(entry, entry))
|
||||
print('{}.type {}'.format(entry, graph_type))
|
||||
print('{}.min 0'.format(entry))
|
||||
else:
|
||||
print('{}.value {}'.format(entry, value))
|
||||
|
||||
|
||||
def derive(entry, value, config):
|
||||
"""Print config or value"""
|
||||
derive_gauge(entry, value, config, 'DERIVE')
|
||||
|
||||
|
||||
def gauge(entry, value, config):
|
||||
"""Print config or value"""
|
||||
derive_gauge(entry, value, config, 'GAUGE')
|
||||
|
||||
|
||||
def print_config(name, title, vlabel, config):
|
||||
"""Print config header"""
|
||||
print('multigraph {}'.format(name))
|
||||
if config:
|
||||
print('graph_title {}'.format(title))
|
||||
print('graph_vlabel {}'.format(vlabel))
|
||||
print('graph_category vpn')
|
||||
print('graph_args --base 1000 --lower-limit 0')
|
||||
|
||||
|
||||
def updown(name, title, values, config):
|
||||
"""Print up/down header"""
|
||||
print('multigraph {}'.format(name))
|
||||
if config:
|
||||
print('graph_title {}'.format(title))
|
||||
print('graph_category vpn')
|
||||
print('graph_order down up')
|
||||
print('graph_args --base 1000')
|
||||
print('graph_vlabel bytes in (-) / out (+) per ${graph_period}')
|
||||
print('down.label received')
|
||||
print('down.type DERIVE')
|
||||
print('down.graph no')
|
||||
print('down.cdef down,8,*')
|
||||
print('down.min 0')
|
||||
print('up.label bps')
|
||||
print('up.type DERIVE')
|
||||
print('up.negative down')
|
||||
print('up.cdef up,8,*')
|
||||
print('up.min 0')
|
||||
for entry, value in values.items():
|
||||
orig = 'down' if entry == 'in' else 'up'
|
||||
if config:
|
||||
print('{}.label {}'.format(orig, entry))
|
||||
print('{}.type DERIVE'.format(orig))
|
||||
print('{}.min 0'.format(orig))
|
||||
else:
|
||||
print('{}.value {}'.format(orig, value))
|
||||
|
||||
|
||||
def derive_all(name, title, vlabel, values, config):
|
||||
"""Print config of value for all items"""
|
||||
print_config(name, title, vlabel, config)
|
||||
for entry, value in values.items():
|
||||
derive(entry, value, config)
|
||||
|
||||
|
||||
def gauge_all(name, title, vlabel, values, config):
|
||||
"""Print config of value for all items"""
|
||||
print_config(name, title, vlabel, config)
|
||||
for entry, value in values.items():
|
||||
gauge(entry, value, config)
|
||||
|
||||
|
||||
def print_values(values, config):
|
||||
"""Print values or config"""
|
||||
if not values:
|
||||
return
|
||||
|
||||
derive_all(
|
||||
'vpn_ipsec_types', 'IPsec SA Types', 'total',
|
||||
values['total']['ipsec']['type'], config)
|
||||
derive_all(
|
||||
'vpn_ipsec_encr', 'IPsec SA ENCR', 'total',
|
||||
values['total']['ipsec']['encr'], config)
|
||||
derive_all(
|
||||
'vpn_ipsec_integ', 'IPsec SA INTEG', 'total',
|
||||
values['total']['ipsec']['integ'], config)
|
||||
|
||||
print_config('vpn_current', 'Current States', 'current', config)
|
||||
for entry, value in values['current']['states']. items():
|
||||
if entry not in ('enumerate', 'iketype'):
|
||||
gauge(entry, value, config)
|
||||
|
||||
gauge_all(
|
||||
'vpn_iketype', 'Current IKE types', 'iketypes',
|
||||
values['current']['states']['iketype'], config)
|
||||
gauge_all(
|
||||
'vpn_state_kind', 'Current pluto states', 'pluto_states',
|
||||
values['current']['states']['enumerate'], config)
|
||||
derive_all(
|
||||
'vpn_state_transition_func', 'Pluto STFs', 'total',
|
||||
values['total']['pluto']['stf'], config)
|
||||
updown(
|
||||
'vpn_traffic_ipsec', 'Total IPsec Traffic',
|
||||
values['total']['ipsec']['traffic'], config)
|
||||
updown(
|
||||
'vpn_traffic_ike', 'Total IKE Traffic',
|
||||
values['total']['ike']['traffic'], config)
|
||||
derive_all(
|
||||
'vpn_dpd', 'Total DPD Traffic', 'dpd_traffic',
|
||||
values['total']['ike']['dpd'], config)
|
||||
|
||||
print_config('vpn_ike', 'Total IKE Sessions', 'ike_traffic', config)
|
||||
for entry in ('ikev2_ok', 'ikev2_fail', 'ikev1_ok', 'ikev1_fail'):
|
||||
if config:
|
||||
print('{}.label {}'.format(entry, entry))
|
||||
print('{}.type DERIVE'.format(entry))
|
||||
print('{}.min 0'.format(entry))
|
||||
else:
|
||||
ike = entry[:5]
|
||||
if 'fail' in entry:
|
||||
status = 'failed'
|
||||
else:
|
||||
status = 'established'
|
||||
print('{}.value {}'.format(
|
||||
entry, values['total']['ike'][ike][status]))
|
||||
|
||||
derive_all(
|
||||
'vpn_ikev1_sent_notifies', 'IKEv1 sent NOTIFIES', 'total',
|
||||
values['total']['ikev1']['sent']['notifies']['error'], config)
|
||||
derive_all(
|
||||
'vpn_ikev2_sent_notifies', 'IKEv2 sent NOTIFIES', 'total',
|
||||
values['total']['ikev2']['sent']['notifies']['error'], config)
|
||||
derive_all(
|
||||
'vpn_ikev1_recv_notifies', 'IKEv1 recv NOTIFIES', 'total',
|
||||
values['total']['ikev1']['recv']['notifies']['error'], config)
|
||||
derive_all(
|
||||
'vpn_ikev2_recv_notifies', 'IKEv2 recv NOTIFIES', 'total',
|
||||
values['total']['ikev2']['recv']['notifies']['error'], config)
|
||||
|
||||
# Down from here it is all crypto params
|
||||
|
||||
derive_all(
|
||||
'vpn_ikev1_encr', 'IKEv1 ENCR', 'total',
|
||||
values['total']['ikev1']['encr'], config)
|
||||
derive_all(
|
||||
'vpn_ikev2_encr', 'IKEv2 ENCR', 'total',
|
||||
values['total']['ikev2']['encr'], config)
|
||||
derive_all(
|
||||
'vpn_ikev1_integ', 'IKEv1 INTEG', 'total',
|
||||
values['total']['ikev1']['integ'], config)
|
||||
derive_all(
|
||||
'vpn_ikev2_integ', 'IKEv2 INTEG', 'total',
|
||||
values['total']['ikev2']['integ'], config)
|
||||
derive_all(
|
||||
'vpn_ikev1_group', 'IKEv1 GROUP', 'total',
|
||||
values['total']['ikev1']['group'], config)
|
||||
derive_all(
|
||||
'vpn_ikev2_group', 'IKEv2 GROUP', 'total',
|
||||
values['total']['ikev2']['group'], config)
|
||||
derive_all(
|
||||
'vpn_ikev2_recv_badgroup_in', 'IKEv2 recv INVALID GROUP', 'total',
|
||||
values['total']['ikev2']['recv']['invalidke']['using'], config)
|
||||
derive_all(
|
||||
'vpn_ikev2_recv_badgroup_out', 'IKEv2 recv-sent INVALID GROUP',
|
||||
'total',
|
||||
values['total']['ikev2']['recv']['invalidke']['suggesting'], config)
|
||||
derive_all(
|
||||
'vpn_ikev2_sent_badgroup_in', 'IKEv2 sent-recv INVALID GROUP', 'total',
|
||||
values['total']['ikev2']['sent']['invalidke']['using'], config)
|
||||
derive_all(
|
||||
'vpn_ikev2_sent_badgroup_out', 'IKEv2 sent-sent INVALID GROUP',
|
||||
'total',
|
||||
values['total']['ikev2']['sent']['invalidke']['suggesting'], config)
|
||||
|
||||
|
||||
def main(args):
|
||||
"""Main program"""
|
||||
values = get_stats()
|
||||
if len(args) > 1 and args[1] == 'autoconf':
|
||||
print('yes' if values else 'no')
|
||||
elif len(args) > 1 and args[1] == 'config':
|
||||
print_values(values, True)
|
||||
else:
|
||||
print_values(values, False)
|
||||
|
||||
|
||||
if __name__ == '__main__':
|
||||
main(sys.argv)
|
||||
|
|
@ -0,0 +1,263 @@
|
|||
#!/bin/bash
|
||||
#
|
||||
# Copyright (C) 2010 Bart Trojanowski <bart@jukie.net>
|
||||
#
|
||||
# This script imports patches generated from a linux/klips git tree into
|
||||
# an libreswan git tree.
|
||||
|
||||
set -e
|
||||
|
||||
prog=$(basename $0)
|
||||
|
||||
say() {
|
||||
echo >&2 "$@"
|
||||
}
|
||||
warn() {
|
||||
say "$prog: $@"
|
||||
}
|
||||
die() {
|
||||
warn "$@"
|
||||
exit 1
|
||||
}
|
||||
|
||||
do_help() {
|
||||
local err=$1
|
||||
local out=1
|
||||
[[ -n "$err" && "$err" -eq 0 ]] || out=2
|
||||
cat >&$out <<END
|
||||
This is a tool that helps in importing patches from klips to libreswan.
|
||||
|
||||
You can import a single patch that changes klips code:
|
||||
|
||||
$prog -p1 < some.patch
|
||||
|
||||
-p[<num>] --patch[=<num>] - import from stdin, -p<num> is passed to patch
|
||||
(default is 1)
|
||||
|
||||
Or import from an existing linux-2.6.git tree with klips applied:
|
||||
|
||||
$prog -k <dir> [ -n <num> ] [ -h <ref> ]
|
||||
|
||||
-k --kernel <dir> - path to kernel git tree
|
||||
-n --number <num> - number of patches to import (default is 1)
|
||||
-r --head <ref> - git ref/head to start from (default is HEAD)
|
||||
|
||||
Generic options:
|
||||
|
||||
-h --help - this help
|
||||
--dry-run - don't apply anything
|
||||
-q --quiet - pass quiet flag to git-am
|
||||
-t --tmp-dir <dir> - use this temporary directory
|
||||
|
||||
END
|
||||
exit $err
|
||||
}
|
||||
|
||||
# set defaults
|
||||
kernel_mode=false
|
||||
patch_mode=false
|
||||
dryrun_mode=false
|
||||
arg_head=
|
||||
arg_kernel=
|
||||
arg_count=
|
||||
arg_pnum=
|
||||
arg_quiet=
|
||||
arg_tmpdir=/tmp
|
||||
|
||||
# this will queue a patch if it looks like it would apply
|
||||
queue_patch() {
|
||||
local queue="$1"
|
||||
local patch="$2"
|
||||
|
||||
# make sure this patch contains only changes to files we care about
|
||||
diffstat -l -p1 "$patch" \
|
||||
| while read fn ; do
|
||||
local dir=$(dirname "$fn")
|
||||
if ! [[ -d "linux/$dir" ]] ; then
|
||||
fn=$(basename "$fn")
|
||||
warn "Patch modifies $fn in $dir, but linux/$dir is not an libreswan"
|
||||
warn "directory. You could 'mkdir $dir' to skip this warning."
|
||||
exit 1
|
||||
fi
|
||||
done
|
||||
|
||||
# convert paths to contain linux/ prefix
|
||||
sed -ie 's,^\(\(---\|+++\) \([a-z]\+/\)\{'"$arg_pnum"'\}\)\(.*\)$,\1linux/\4,' "$patch"
|
||||
|
||||
# add it to the queue
|
||||
cat "$patch" >> "$queue"
|
||||
|
||||
# check if the patch applies (including all the ones that came before it
|
||||
git apply --check -p"$arg_pnum" "$queue" || die "patch doesn't apply"
|
||||
}
|
||||
|
||||
apply_queue() {
|
||||
local queue="$1"
|
||||
|
||||
$dryrun_mode && return 0
|
||||
|
||||
# import the patch
|
||||
git am < "$queue"
|
||||
}
|
||||
|
||||
is_git_dir() {
|
||||
local dir="$1"
|
||||
[[ -d "$dir" \
|
||||
&& -f "$dir/HEAD" \
|
||||
&& -d "$dir/objects" \
|
||||
&& -d "$dir/refs" ]]
|
||||
}
|
||||
|
||||
find_kernel_git_dir() {
|
||||
for dir in "$arg_kernel" "$arg_kernel/.git" ; do
|
||||
if is_git_dir "$dir" ; then
|
||||
echo "$dir"
|
||||
return 0
|
||||
fi
|
||||
done
|
||||
|
||||
die "cannot find git dir at $arg_kernel"
|
||||
}
|
||||
|
||||
# imports $arg_count patches from $arg_kernel
|
||||
do_kernel_import() {
|
||||
local workdir="$arg_tmpdir/$prog-$$"
|
||||
local series="$workdir/series"
|
||||
local queue="$workdir/queue"
|
||||
|
||||
[[ -d $workdir ]] && die "$workdir already exists, remove it"
|
||||
mkdir -p "$workdir" || die "failed to create: $workdir"
|
||||
trap "rm -rf $workdir" EXIT HUP INT QUIT ABRT
|
||||
|
||||
# find the kernel dir
|
||||
local kernel_git=$(find_kernel_git_dir)
|
||||
|
||||
# generate those patches
|
||||
git --git-dir "$kernel_git" \
|
||||
format-patch \
|
||||
-"$arg_count" \
|
||||
--suffix=.patch \
|
||||
--output-directory "$workdir" \
|
||||
"$arg_head" \
|
||||
> "$series" \
|
||||
|| die "failed to generate $arg_count patch(es) in from $kernel_git"
|
||||
|
||||
for patch in $(cat "$series") ; do
|
||||
local name=$(basename "$patch")
|
||||
|
||||
say "Testing $name..."
|
||||
queue_patch "$queue" "$patch"
|
||||
done
|
||||
|
||||
say "Looks good, now applying..."
|
||||
apply_queue "$queue"
|
||||
|
||||
say "DONE"
|
||||
}
|
||||
|
||||
# import patch read from /dev/stdin
|
||||
do_patch_from_stdin() {
|
||||
local patch="$arg_tmpdir/$prog-$$.patch"
|
||||
local queue="$arg_tmpdir/$prog-$$.queue"
|
||||
trap "rm -f $patch $queue" EXIT HUP INT QUIT ABRT
|
||||
|
||||
# read in the patch
|
||||
cat > "$patch"
|
||||
|
||||
# reset the queue
|
||||
cat </dev/null >"$queue"
|
||||
|
||||
say "Testing patch from stdin..."
|
||||
queue_patch "$queue" "$patch"
|
||||
|
||||
say "Looks good, now applying..."
|
||||
apply_queue "$queue"
|
||||
|
||||
say "DONE"
|
||||
}
|
||||
|
||||
# parse parameters
|
||||
while [[ -n "$1" ]] ; do
|
||||
cmd="$1"
|
||||
shift
|
||||
case "$cmd" in
|
||||
-h|--help)
|
||||
do_help 0
|
||||
;;
|
||||
--dry-run)
|
||||
dryrun_mode=true
|
||||
;;
|
||||
--debug)
|
||||
set -x
|
||||
;;
|
||||
-r|--head)
|
||||
arg_head="$1"
|
||||
shift || die "--head requires an argument"
|
||||
;;
|
||||
-k|--kernel)
|
||||
kernel_mode=true
|
||||
arg_kernel="$1"
|
||||
[[ -d "$arg_kernel" ]] || die "no such directory: $arg_kernel"
|
||||
shift
|
||||
;;
|
||||
-p|--patch)
|
||||
patch_mode=true
|
||||
;;
|
||||
-p[0-9]*)
|
||||
patch_mode=true
|
||||
arg_pnum="${cmd#-p}"
|
||||
;;
|
||||
--patch=[0-9]*)
|
||||
patch_mode=true
|
||||
arg_pnum="${cmd#*=}"
|
||||
;;
|
||||
-n|--number)
|
||||
arg_count="$1"
|
||||
shift || die "--number requires an argument"
|
||||
;;
|
||||
-[0-9]*)
|
||||
arg_count="${cmd#-}"
|
||||
;;
|
||||
-q|--quiet)
|
||||
arg_quiet="--quiet"
|
||||
;;
|
||||
-t|--tmp-dir)
|
||||
arg_tmpdir="$1"
|
||||
[[ -d "$arg_tmpdir" ]] || die "no such directory: $arg_tmpdir"
|
||||
shift
|
||||
;;
|
||||
*)
|
||||
warn "invalid option: $cmd"
|
||||
do_help 1
|
||||
;;
|
||||
esac
|
||||
done
|
||||
|
||||
( $kernel_mode || $patch_mode ) || die "need to use --kernel or --patch mode"
|
||||
( $kernel_mode && $patch_mode ) && die "only use --kernel or --patch mode"
|
||||
|
||||
for n in diffstat filterdiff ; do
|
||||
$n --help </dev/null >/dev/null 2>&1 || die "cannot find '$n' (part of patchutils package)"
|
||||
done
|
||||
|
||||
if [[ -z "$arg_pnum" ]] ; then
|
||||
arg_pnum=1
|
||||
elif [[ "$arg_pnum" -gt 0 ]] ; then
|
||||
die "--patch/-p level must be a number"
|
||||
fi
|
||||
|
||||
if $kernel_mode; then
|
||||
[[ -z "$arg_count" ]] && arg_count=1
|
||||
[[ -z "$arg_head" ]] && arg_head=HEAD
|
||||
do_kernel_import
|
||||
ret=$?
|
||||
|
||||
elif $patch_mode; then
|
||||
do_patch_from_stdin
|
||||
ret=$?
|
||||
|
||||
else
|
||||
ret=1
|
||||
fi
|
||||
|
||||
exit $ret
|
||||
|
|
@ -0,0 +1,243 @@
|
|||
#!/bin/bash
|
||||
#
|
||||
# Copyright (C) 2010 Bart Trojanowski <bart@jukie.net>
|
||||
#
|
||||
# This script applies saref, natt, and klips patches to a
|
||||
# linux kernel git tree.
|
||||
|
||||
set -e
|
||||
|
||||
prog=$(basename $0)
|
||||
|
||||
say() {
|
||||
echo >&2 "$@"
|
||||
}
|
||||
warn() {
|
||||
say "$prog: $@"
|
||||
}
|
||||
die() {
|
||||
warn "$@"
|
||||
exit 1
|
||||
}
|
||||
|
||||
do_help() {
|
||||
local err=$1
|
||||
local out=1
|
||||
[[ -n "$err" && "$err" -eq 0 ]] || out=2
|
||||
cat >&$out <<END
|
||||
This is a tool that applies libreswan patches to a kernel git tree.
|
||||
|
||||
Syntax
|
||||
|
||||
$prog [ -s | --saref ] [ -n | --natt ] [ -k | --klips ] <path to kernel>
|
||||
|
||||
Options:
|
||||
|
||||
-s --saref - apply the saref patch(es), create commit(s)
|
||||
-n --natt - apply the natt patch(es), create commit(s)
|
||||
-k --klips - apply the klips patch(es), create commit(s)
|
||||
|
||||
Generic options:
|
||||
|
||||
-h --help - this help
|
||||
--dry-run - don't apply anything
|
||||
-q --quiet - pass quiet flag to git-am
|
||||
-t --tmp-dir <dir> - use this temporary directory
|
||||
|
||||
END
|
||||
exit $err
|
||||
}
|
||||
|
||||
# set defaults
|
||||
do_saref=false
|
||||
do_natt=false
|
||||
do_klips=false
|
||||
dryrun_mode=false
|
||||
cleen_up=true
|
||||
arg_kernel=
|
||||
arg_quiet=
|
||||
arg_tmpdir=/tmp
|
||||
libreswan_rev=
|
||||
kernel_ver=
|
||||
|
||||
# this will queue a patch if it looks like it would apply
|
||||
queue_patch() {
|
||||
local queue="$1"
|
||||
local pnum="$2"
|
||||
local patch="$3"
|
||||
|
||||
# add it to the queue
|
||||
cat "$patch" >> "$queue"
|
||||
|
||||
# check if the patch applies (including all the ones that came before it)
|
||||
(
|
||||
cd "$arg_kernel"
|
||||
git apply --ignore-space-change --ignore-whitespace --check -p"$pnum" "$queue" || die "patch doesn't apply"
|
||||
)
|
||||
}
|
||||
|
||||
# apply the patch in the kernel tree
|
||||
apply_a_patch() {
|
||||
local pnum="$1"
|
||||
local patch="$2"
|
||||
local desc="$3"
|
||||
|
||||
$dryrun_mode && return 0
|
||||
|
||||
# import the patch
|
||||
(
|
||||
cd "$arg_kernel"
|
||||
git apply --ignore-space-change --ignore-whitespace --index < "$patch"
|
||||
diffstat -l -p"$pnum" < "$patch" | xargs git add
|
||||
git commit -m"$desc"
|
||||
)
|
||||
}
|
||||
|
||||
is_git_dir() {
|
||||
local dir="$1"
|
||||
[[ -d "$dir" \
|
||||
&& -f "$dir/HEAD" \
|
||||
&& -d "$dir/objects" \
|
||||
&& -d "$dir/refs" ]]
|
||||
}
|
||||
|
||||
generate_saref_patch() {
|
||||
local workdir="$1"
|
||||
local series="$2"
|
||||
local count=0
|
||||
|
||||
for src in patches/kernel/$kernel_ver/0*.patch ; do
|
||||
count=$(($count + 1))
|
||||
local patch="$workdir/saref$count.patch"
|
||||
local desc="Applied saref patch #$count from Libreswan $libreswan_rev"
|
||||
local pnum=1
|
||||
|
||||
say "Reading ${src##*/}..."
|
||||
say "Generating ${patch##*/}..."
|
||||
|
||||
cat "$src" > "$patch"
|
||||
|
||||
echo "$pnum" "$patch" "$desc" >> $series
|
||||
done
|
||||
}
|
||||
|
||||
generate_natt_patch() {
|
||||
local workdir="$1"
|
||||
local series="$2"
|
||||
local patch="$workdir/natt.patch"
|
||||
local desc="Applied NATT patch from Libreswan $libreswan_rev"
|
||||
local pnum=1
|
||||
|
||||
say "Generating ${patch##*/}..."
|
||||
|
||||
cat "patches/kernel/$kernel_ver/natt.patch" > "$patch"
|
||||
|
||||
echo "$pnum" "$patch" "$desc" >> $series
|
||||
}
|
||||
|
||||
generate_klips_patch() {
|
||||
local workdir="$1"
|
||||
local series="$2"
|
||||
local patch="$workdir/klips.patch"
|
||||
local desc="Applied klips patch from Libreswan $libreswan_rev"
|
||||
local pnum=1
|
||||
|
||||
say "Generating ${patch##*/}..."
|
||||
|
||||
make kernelpatch2.6 > "$patch"
|
||||
|
||||
echo "$pnum" "$patch" "$desc" >> $series
|
||||
}
|
||||
|
||||
apply_patches() {
|
||||
local workdir="$arg_tmpdir/$prog-$$"
|
||||
local series="$workdir/series"
|
||||
local queue="$workdir/queue"
|
||||
|
||||
[[ -d $workdir ]] && die "$workdir already exists, remove it"
|
||||
mkdir -p "$workdir" || die "failed to create: $workdir"
|
||||
if $cleen_up ; then
|
||||
trap "rm -rf $workdir" EXIT HUP INT QUIT ABRT
|
||||
else
|
||||
trap "echo 'not cleaning: $workdir'" EXIT HUP INT QUIT ABRT
|
||||
fi
|
||||
|
||||
$do_saref && generate_saref_patch "$workdir" "$series"
|
||||
$do_natt && generate_natt_patch "$workdir" "$series"
|
||||
$do_klips && generate_klips_patch "$workdir" "$series"
|
||||
|
||||
while read pnum patch desc ; do
|
||||
local name=$(basename "$patch")
|
||||
|
||||
say "Testing $name..."
|
||||
queue_patch "$queue" "$pnum" "$patch"
|
||||
done < "$series"
|
||||
|
||||
while read pnum patch desc ; do
|
||||
local name=$(basename "$patch")
|
||||
|
||||
say "Applying $name..."
|
||||
apply_a_patch "$pnum" "$patch" "$desc"
|
||||
done < "$series"
|
||||
|
||||
say "DONE"
|
||||
}
|
||||
|
||||
# parse parameters
|
||||
while [[ -n "$1" ]] ; do
|
||||
[[ -n "$arg_kernel" ]] && die "garbage at end of line; see $prog --help"
|
||||
cmd="$1"
|
||||
shift
|
||||
case "$cmd" in
|
||||
-h|--help)
|
||||
do_help 0
|
||||
;;
|
||||
--dry-run)
|
||||
dryrun_mode=true
|
||||
;;
|
||||
--debug)
|
||||
set -x
|
||||
;;
|
||||
--keep)
|
||||
cleen_up=false
|
||||
;;
|
||||
-q|--quiet)
|
||||
arg_quiet="--quiet"
|
||||
;;
|
||||
-t|--tmp-dir)
|
||||
arg_tmpdir="$1"
|
||||
[[ -d "$arg_tmpdir" ]] || die "no such directory: $arg_tmpdir"
|
||||
shift
|
||||
;;
|
||||
-s|--saref)
|
||||
do_saref=true
|
||||
;;
|
||||
-n|--natt)
|
||||
do_natt=true
|
||||
;;
|
||||
-k|--klips)
|
||||
do_klips=true
|
||||
;;
|
||||
-*)
|
||||
warn "invalid option: $cmd"
|
||||
do_help 1
|
||||
;;
|
||||
*)
|
||||
arg_kernel="$cmd"
|
||||
;;
|
||||
esac
|
||||
done
|
||||
|
||||
( $do_saref || $do_natt || $do_klips ) || die "need to specify at least one of --saref, --natt, or --klips"
|
||||
|
||||
is_git_dir ".git" && libreswan_rev=$(git describe)
|
||||
[[ "${libreswan_rev:0:1}" = "v" ]] || die "run this script from the top of the libreswan git tree"
|
||||
echo "Libreswan revision $libreswan_rev"
|
||||
|
||||
[[ -n "$arg_kernel" ]] || die "missing kernel directory; see $prog --help"
|
||||
is_git_dir "$arg_kernel/.git" && kernel_ver=$(git --git-dir="$arg_kernel/.git" describe | sed -ne's/v\(2\.6\.[0-9]\+\).*/\1/p')
|
||||
[[ "${kernel_ver:0:2}" = "2." ]] || die "$arg_kernel: this dones't look like a kernel git tree"
|
||||
|
||||
apply_patches
|
||||
|
||||
exit $ret
|
||||
|
|
@ -0,0 +1,52 @@
|
|||
#!/usr/bin/python2 -tt
|
||||
# -*- coding: utf-8 -*-
|
||||
|
||||
"""Is connection encrypted?
|
||||
|
||||
./is_encrypted.py --debug --port 443 10.6.6.1
|
||||
./is_encrypted.py --debug --source 2001:998:2e:f00::42 2a00:1190:c00a:f00::1
|
||||
./is_encrypted.py --debug --source 193.65.3.113 172.27.129.42
|
||||
|
||||
/*
|
||||
* Is connection encrypted? -utility.
|
||||
*
|
||||
* Copyright (C) 2018 Kim B. Heino <b@bbbs.net>
|
||||
*
|
||||
* This program is free software; you can redistribute it and/or modify
|
||||
* it under the terms of the GNU General Public License as published by
|
||||
* the Free Software Foundation; either version 2 of the License, or
|
||||
* (at your option) any later version.
|
||||
*
|
||||
* This program is distributed in the hope that it will be useful,
|
||||
* but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
* GNU General Public License for more details.
|
||||
*
|
||||
* You should have received a copy of the GNU General Public License along
|
||||
* with this program; if not, write to the Free Software Foundation, Inc.,
|
||||
* 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
|
||||
*/
|
||||
"""
|
||||
|
||||
from __future__ import print_function
|
||||
from __future__ import unicode_literals
|
||||
import argparse
|
||||
import swan
|
||||
|
||||
|
||||
def main():
|
||||
"""Main program"""
|
||||
parser = argparse.ArgumentParser(
|
||||
description='check if traffic would get encrypted by IPsec')
|
||||
parser.add_argument('--debug', action='store_true', help='show debugging')
|
||||
parser.add_argument('--source', help='source address of the packet')
|
||||
parser.add_argument('--port', help='connect to TCP port on destination')
|
||||
parser.add_argument('destination', help='destination IP address to check')
|
||||
args = parser.parse_args()
|
||||
|
||||
print(swan.is_encrypted(
|
||||
args.destination, args.port, args.source, debug=args.debug))
|
||||
|
||||
|
||||
if __name__ == '__main__':
|
||||
main()
|
||||
|
|
@ -0,0 +1,116 @@
|
|||
# -*- coding: utf-8 -*-
|
||||
|
||||
"""Random functions for Libreswan.
|
||||
|
||||
/*
|
||||
* Is connection encrypted? -utility.
|
||||
*
|
||||
* Copyright (C) 2018 Kim B. Heino <b@bbbs.net>
|
||||
*
|
||||
* This program is free software; you can redistribute it and/or modify
|
||||
* it under the terms of the GNU General Public License as published by
|
||||
* the Free Software Foundation; either version 2 of the License, or
|
||||
* (at your option) any later version.
|
||||
*
|
||||
* This program is distributed in the hope that it will be useful,
|
||||
* but WITHOUT ANY WARRANTY; without even the implied warranty of
|
||||
* MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
|
||||
* GNU General Public License for more details.
|
||||
*
|
||||
* You should have received a copy of the GNU General Public License along
|
||||
* with this program; if not, write to the Free Software Foundation, Inc.,
|
||||
* 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
|
||||
*/
|
||||
"""
|
||||
|
||||
from __future__ import print_function
|
||||
from __future__ import unicode_literals
|
||||
import socket
|
||||
import subprocess
|
||||
import sys
|
||||
try:
|
||||
import ipaddress
|
||||
except ImportError:
|
||||
sys.exit('Please install https://pypi.python.org/pypi/ipaddress')
|
||||
|
||||
|
||||
def run_command(params):
|
||||
"""Run command and return it's output"""
|
||||
try:
|
||||
output = subprocess.check_output(params, stderr=subprocess.STDOUT)
|
||||
except subprocess.CalledProcessError:
|
||||
return ''
|
||||
return output.decode('utf-8', 'ignore')
|
||||
|
||||
|
||||
def is_encrypted(destination, port=None, source=None, timeout=1.0,
|
||||
debug=False):
|
||||
"""Is connection encrypted?
|
||||
Returns True/False or raises ValueError
|
||||
"""
|
||||
# Parse destination, autodetect source if not specified
|
||||
destination = ipaddress.ip_address(unicode(destination))
|
||||
if not source:
|
||||
output = run_command([
|
||||
'/sbin/ip', '-oneline', 'route', 'get', unicode(destination)])
|
||||
try:
|
||||
source = output.split(' src ')[1].split()[0]
|
||||
except IndexError:
|
||||
raise ValueError('failed to detect source IP')
|
||||
source = ipaddress.ip_address(unicode(source))
|
||||
if debug:
|
||||
print('Checking {} to {} port {}'.format(source, destination, port))
|
||||
|
||||
# Connect to port if specified, ignore errors
|
||||
if port:
|
||||
try:
|
||||
sock = socket.create_connection(
|
||||
(unicode(destination), port),
|
||||
timeout,
|
||||
(unicode(source), 0))
|
||||
sock.close()
|
||||
except socket.error as error:
|
||||
if debug:
|
||||
print('Connection error: {}'.format(error))
|
||||
|
||||
# Get "ip xfrm" output
|
||||
output = run_command(['/sbin/ip', '-oneline', 'xfrm', 'policy', 'list'])
|
||||
|
||||
# Parse output
|
||||
encrypted = False
|
||||
priority = 65536
|
||||
for line in output.splitlines():
|
||||
# Parse single line
|
||||
parsed = {
|
||||
'src': None,
|
||||
'dst': None,
|
||||
'dir': None,
|
||||
'priority': None,
|
||||
'proto': None,
|
||||
'reqid': None,
|
||||
}
|
||||
keyword = None
|
||||
for item in line.replace('\\', ' ').split():
|
||||
if item in parsed and not parsed[item]:
|
||||
keyword = item
|
||||
elif keyword:
|
||||
parsed[keyword] = item
|
||||
keyword = None
|
||||
|
||||
# Is it our line?
|
||||
if not (
|
||||
parsed['dir'] == 'out' and
|
||||
parsed['proto'] == 'esp' and
|
||||
priority > int(parsed['priority']) and
|
||||
source in ipaddress.ip_network(parsed['src']) and
|
||||
destination in ipaddress.ip_network(parsed['dst'])
|
||||
):
|
||||
continue
|
||||
|
||||
# It is, update priority/encrypted
|
||||
if debug:
|
||||
print(line)
|
||||
priority = int(parsed['priority'])
|
||||
encrypted = parsed['reqid'] not in (None, '0')
|
||||
|
||||
return encrypted
|
||||
|
|
@ -0,0 +1,10 @@
|
|||
This directory contains scripts that mimic certain KLIPS-only commands
|
||||
when using NETKEY. These may fold back into the distribution later on,
|
||||
or get replaced by new code. Output is not guaranteed to be identical
|
||||
to the KLIPS versions.
|
||||
|
||||
eroute: replacement for KLIPS' "ipsec eroute"
|
||||
look: replacement for KLIPS' "ipsec look"
|
||||
|
||||
Install: replace the KLIPS script in /usr/local/libexec/ipsec/ with a
|
||||
version from this directory.
|
||||
|
|
@ -0,0 +1,66 @@
|
|||
#!/usr/bin/perl
|
||||
#
|
||||
# (c) Xelerance <ken@xelerance.com>
|
||||
#
|
||||
# I whipped this up in 15 minutes after switching my laptop to 2.6
|
||||
# so it's ugly, and could use some major improvement. setkey output is
|
||||
# ugly to parse
|
||||
|
||||
open(SETKEY,"setkey -PD|");
|
||||
|
||||
while(<SETKEY>) {
|
||||
|
||||
if ( m/any/) {
|
||||
($dst,$src, $any) = split(" ",$_);
|
||||
$src =~ s/\[any\]//g;
|
||||
$dst =~ s/\[any\]//g;
|
||||
}
|
||||
if ( m/ipsec/ ) {
|
||||
($dir,$dummy) = split(" ",$_);
|
||||
}
|
||||
|
||||
if ( m/unique/ ) {
|
||||
($proto,$type,$tunnel,$dummy) = split("/",$_);
|
||||
($net1,$net2) = split("-",$tunnel);
|
||||
if($dir eq "out" ) {
|
||||
$remotegw=$net2;
|
||||
$local=$net1;
|
||||
$temp = $src;
|
||||
$src=$dst;
|
||||
$dst=$temp;
|
||||
|
||||
}
|
||||
if ($dir eq "in") {
|
||||
$remotegw=$net1;
|
||||
$local=$net2;
|
||||
|
||||
}
|
||||
if ($dir eq "fwd") {
|
||||
$remotegw=$net1;
|
||||
$local=$net2;
|
||||
}
|
||||
}
|
||||
if ( m/spid/ ) {
|
||||
($spidstr,$seqstr, $pidstr) = split(" ",$_);
|
||||
($tmp,$spi) = split("\=",$spidstr);
|
||||
if ($spi != "" && $tunnel != "" ) {
|
||||
for ($src) {
|
||||
if (! m/\// ) {
|
||||
$src .= "/32";
|
||||
}
|
||||
}
|
||||
for ($dst) {
|
||||
if (! m/\// ) {
|
||||
$dst .= "/32";
|
||||
}
|
||||
}
|
||||
printf("%3s %-18s -> %-18s => tun0x%s@%s\n",$dir,$src,$dst,$spi,$remotegw);
|
||||
# Reset
|
||||
$tunnel = "";
|
||||
$spi = "";
|
||||
$dir = "";
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
close(SETKEY);
|
||||
|
|
@ -0,0 +1,48 @@
|
|||
#!/usr/bin/perl
|
||||
#
|
||||
# (c) Feb 2008 - Matteo Vitturi <matteo_vitturi@virgilio.it>
|
||||
#
|
||||
# A script to parse ip xfrm output - NETKEY version of "ipsec look"
|
||||
|
||||
open(IPSXP,"ip -s x p|");
|
||||
|
||||
$dir = '';
|
||||
$remotegw = '';
|
||||
$spi = '';
|
||||
while(<IPSXP>) {
|
||||
|
||||
if ( m/src (.+) dst (.+) uid/ ) { ($src,$dst) = ($2,$1) };
|
||||
if ( m/dir (.+) action/ ) { $dir = $1 }
|
||||
if ( m/index (.+) prio/ ) { $spi = $1 }
|
||||
if ( m/tmpl src (.+) dst (.+)/ and $remotegw eq '' ) {
|
||||
($net1,$net2) = ($1,$2) ;
|
||||
if ( $dir eq "out" ) {
|
||||
$remotegw=$net2;
|
||||
$local=$net1;
|
||||
$temp = $src;
|
||||
$src=$dst;
|
||||
$dst=$temp;
|
||||
}
|
||||
if ($dir eq "in") {
|
||||
$remotegw=$net1;
|
||||
$local=$net2;
|
||||
|
||||
}
|
||||
if ($dir eq "fwd") {
|
||||
$remotegw=$net1;
|
||||
$local=$net2;
|
||||
}
|
||||
}
|
||||
|
||||
if ( m/proto/ && $dir ne '') {
|
||||
$src .= "/32" if $src !~ m/\//;
|
||||
$dst .= "/32" if $dst !~ m/\//;
|
||||
printf("%3s %-18s -> %-18s => tun0x%s@%s\n",
|
||||
$dir,$src,$dst,$spi,$remotegw) unless $remotegw eq '0.0.0.0';
|
||||
$dir = '';
|
||||
$remotegw = '';
|
||||
$spi = '';
|
||||
}
|
||||
}
|
||||
|
||||
close(IPSXP);
|
||||
|
|
@ -0,0 +1,75 @@
|
|||
#!/usr/bin/python
|
||||
#
|
||||
# example-terminate.py
|
||||
#
|
||||
# This is a script that can be ADDED to the updown scripts. Normally this would
|
||||
# be addd to /usr/libexec/ipsec/_updown.netkey (for protostack=netkey)
|
||||
# This is an example that logs XAUTH users to /tmp/terminate.log when the
|
||||
# tunnel goes down:
|
||||
#
|
||||
# Inside _updown.netkey add a call to this script, like:
|
||||
#
|
||||
#
|
||||
# down-client)
|
||||
# # connection to my client subnet going down
|
||||
# downrule
|
||||
# # If you are doing a custom version, firewall commands go here.
|
||||
# restoreresolvconf
|
||||
# /usr/local/sbin/example-terminate.py $PLUTO_XAUTH_USERNAME
|
||||
#
|
||||
|
||||
import os, sys, pipes
|
||||
import commands
|
||||
import requests
|
||||
import signal
|
||||
|
||||
def child(username):
|
||||
# Send a GET request to our logserver to log disconnecting client
|
||||
# this might block if unavailable, so we must be detached from
|
||||
# pluto.
|
||||
url = 'https://logserver.example.com/delete/'
|
||||
payload = {'username': username}
|
||||
r = requests.get(url, data=payload)
|
||||
|
||||
fp = open("/tmp/terminate.log","a")
|
||||
fp.write("Termination notification sent for %s\n"%username)
|
||||
fp.write("HTTP status code:%s\n"%r.status_code)
|
||||
fp.write(r.text)
|
||||
fp.write("\n")
|
||||
fp.close()
|
||||
os._exit(0)
|
||||
|
||||
if __name__ == '__main__':
|
||||
if len(sys.argv) < 2:
|
||||
# nothing to log
|
||||
sys.exit(0)
|
||||
|
||||
username = sys.argv[1]
|
||||
if username != pipes.quote(username):
|
||||
sys.exit("bogus characters in username '%s', ignored termination request"%username)
|
||||
|
||||
# Redirect standard file descriptors to ensure pluto does not block on us
|
||||
os.close(0)
|
||||
os.close(1)
|
||||
os.close(2)
|
||||
os.close(3) # pluto.log - workaround for bug #202
|
||||
|
||||
# Do a double fork to decouple from the parent environment
|
||||
pid = os.fork()
|
||||
if pid > 0:
|
||||
# exit first parent
|
||||
sys.exit(0)
|
||||
|
||||
os.chdir("/")
|
||||
os.setsid()
|
||||
os.umask(0)
|
||||
|
||||
# do second fork
|
||||
pid = os.fork()
|
||||
if pid > 0:
|
||||
# exit from second parent
|
||||
sys.exit(0)
|
||||
|
||||
# we're fully detached now - take as long as needed to do the work
|
||||
child(username)
|
||||
|
||||
|
|
@ -0,0 +1,946 @@
|
|||
Changes to Pluto
|
||||
================
|
||||
|
||||
- [MCR] changes to support co-terminal connections of the near kind.
|
||||
|
||||
- --dontrekey is now a misnomer: the IPsec SA will be rekeyed if we
|
||||
are the Initiator and there is outbound traffic in the period
|
||||
leading up to the rekeying decision point. This is a heuristic: a
|
||||
mistake doesn't matter much since the connection, once deleted, will
|
||||
be rekeyed on demand.
|
||||
|
||||
- accept a proposal with compression even if the connection does not
|
||||
have the POLICY_COMPRESSION flag. This is a reversal of a policy
|
||||
introduced in 1.6.
|
||||
|
||||
- fixed load-triggered deadlock between asynch DNS process and pluto
|
||||
|
||||
- add %myid to indirectly refer to current id. Set from $IPSECmyid on
|
||||
startup and via whack --myid
|
||||
|
||||
- make whack/pluto version matching less stringent for --status and
|
||||
--shutdown.
|
||||
|
||||
- remove all code for DODGE_DH_MISSING_ZERO_BUG
|
||||
|
||||
- when attempting outbound Opportunism, check our side's DNS
|
||||
entries, not just the other side's. If we don't have them,
|
||||
fail: not worth attempting.
|
||||
|
||||
|
||||
Change since 2.00 release by MCR and DHR
|
||||
|
||||
- "KEY Restrict": in each place where Pluto used the DNS KEY Resource
|
||||
Record, it now uses one of our special TXT Resource Records. For
|
||||
now, we continue to accept KEY records if the TXT record is not
|
||||
found.
|
||||
|
||||
Changes since 1.99 release by D. Hugh Redelmeier <hugh@mimosa.com
|
||||
|
||||
- when Responding with an Opportunistic connection, check our side's
|
||||
DNS for proper delegation. This avoids the promiscuous
|
||||
"packetdefault" conn from licensing unexpected access to our clients.
|
||||
|
||||
- many changes for "Policy Groups":
|
||||
+ host=%group and host=%opportunisticgroup signals that
|
||||
contents of group files should be substituted
|
||||
+ an opportunistic connection can be constrained to only
|
||||
apply to peers and their clients within a specified subnet
|
||||
+ Pluto can manage pure shunt connections (involving no IKE).
|
||||
+ failure-case shunts can now be specified.
|
||||
|
||||
- add a listing of pending Phase 2 negotiations to status output
|
||||
|
||||
- reorganize impairment mechanism. Now controlled by unadvertised
|
||||
runtime flags.
|
||||
|
||||
- [MCR] tolerate Certificate Request Payloads any time
|
||||
|
||||
- [MCR] generate Vendor ID Payloads (sent if PLUTO_SENDS_VENDORID defined)
|
||||
|
||||
- [MCR] print some of content of Vendor ID Payloads received.
|
||||
|
||||
- Corrected design bug in --dontrekey. If IPsec SA lifetime chosen by
|
||||
us is smaller than what other side specified in negotiation, we will
|
||||
renegotiate when the shorter lifetime dictates. This is the only
|
||||
sane way to communicate the shorter lifetime. For ISAKMP SA lifetime,
|
||||
we accept the other side's choice.
|
||||
|
||||
|
||||
Changes since 1.98 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- Fixed assertion failure in quick_inI1_outR1_continue. Can happen
|
||||
when the result of a DNS TXT query is not needed by the time it
|
||||
arrives (due to another negotiation providing the information).
|
||||
Can be demonstrated by the test "ipsec-oppo-race-iinr-net".
|
||||
|
||||
|
||||
Changes since 1.97 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- added --dnskeyondemand option for connection ends.
|
||||
|
||||
- Fixed a bug that provoked PF_KEY errors. If an updown script fails
|
||||
and it was invoked as part of a step that involved installing an
|
||||
eroute, any previous eroute should be restored as part of undoing
|
||||
that step. The bug was that any old eroute was lost.
|
||||
|
||||
- When representing a long string in a DNS TXT resource record,
|
||||
it must be broken up into chunks less than 256. When reconstitute
|
||||
the original string, Pluto now just concatenates them. It used to
|
||||
add a space after a chunk if it was shorter than 255 characters.
|
||||
This should make it easier (not easy!) to edit the TXT record
|
||||
source by hand.
|
||||
|
||||
- [mlafon@arkoon.net] fixed protocol numbers used in delete payload.
|
||||
|
||||
- took -DDODGE_DH_MISSING_ZERO_BUG out of Makefile. Anyone planning
|
||||
on talking to FreeS/WAN 1.0 systems should put it back. And
|
||||
check into the Smithsonian Institution.
|
||||
|
||||
- in --status and logging output, references to connection instances
|
||||
now contain a sequence number for the instance and details of the
|
||||
instantiation (i.e. more IP addresses). Perhaps too bulky.
|
||||
|
||||
- reworked initiate_opportunistic to avoid race conditions
|
||||
introduced with Asynch DNS.
|
||||
|
||||
- added impairment to aid testing: IMPAIR_DELAY_ADNS_ANSWER
|
||||
|
||||
- whack --status now displays the bare shunt table.
|
||||
|
||||
- Changed Main Mode hash calculation to use the ID Payload as sent
|
||||
by peer, rather than reconstituting it from our tables. This matters
|
||||
if we use different case than peer did (eg @example.com vs @Example.Com).
|
||||
|
||||
- renamed source files:
|
||||
+ kernel_comm.[hc] => rcv_whack.[hc]
|
||||
+ preshared.[hc] => keys.[hc]
|
||||
+ main.c => plutomain.c
|
||||
|
||||
- added POLICY_UP to track whether our admin has requested that this
|
||||
connection be up.
|
||||
|
||||
|
||||
Changes since 1.96 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- fixed a bug that would make the following (pointless) sequence to
|
||||
trigger a failure of Pluto assertion "c->routing == RT_ROUTED_TUNNEL":
|
||||
ipsec auto --add conn
|
||||
ipsec auto --up conn
|
||||
ipsec auto --route conn
|
||||
ipsec auto --down conn
|
||||
|
||||
- send Delete Notifications when deleting IPSEC SAs. We don't yet
|
||||
understand ones we receive.
|
||||
|
||||
- added "keyid" (see ipsec_keyblobtoid(3)) to appropriate messages so
|
||||
that RSA key being used is manifest.
|
||||
|
||||
- track whether information (security gateway, public key) came from
|
||||
DNSsec or unauthenticated DNS. Untested since normal resolver calls
|
||||
can no longer return DNSsec results. The information isn't used.
|
||||
|
||||
- use asynchronous DNS mechanism for all lookups during keying.
|
||||
|
||||
- added --interface flag to Pluto to constrain interfaces considered.
|
||||
One use of this option is to specify which interface should be used
|
||||
when two or more share the same IP address. Another is to assist
|
||||
with test setups.
|
||||
|
||||
- small cleanups:
|
||||
+ fix compile without no -DKLIPS
|
||||
+ use ttodatav in place of atobytes and ttodata
|
||||
+ use hosttosubnet
|
||||
+ define and use close_any
|
||||
+ define and use USED_BY_KLIPS and USED_BY_DEBUG
|
||||
+ define and use happy, a kind of assertion macro
|
||||
+ define and use impossible, a kind of assertion macro
|
||||
+ when an unknown attribute value is seen in an ISAKMP transform,
|
||||
reject only that transform, not the whole proposal.
|
||||
+ add Hybrid auth methods to table to improve diagnostics
|
||||
|
||||
Changes since 1.95 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- fixed bug in ipsec_doi.c:main_inR3 with unknown consequences.
|
||||
When the Initiator finds out the peer's Phase 1 ID, it might
|
||||
change which connection it thinks is being used. If so,
|
||||
this routine used to perform an operation on the old connection
|
||||
data structure -- a mistake now corrected. There are few cases
|
||||
where the Responder surprises the Initiator about Phase 1 IDs.
|
||||
|
||||
- fixed an error in network error handling that caused a segfault if
|
||||
there was a MSG_ERRQUEUE report on the last message of a Quick Mode
|
||||
exchange.
|
||||
|
||||
- fix leak (detected by assertion failure) triggered by missing
|
||||
private key.
|
||||
|
||||
|
||||
Changes since 1.94 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- added "whack --deletestate <state_object_number>" as a crude
|
||||
tool for deleting instances of connections.
|
||||
|
||||
- fix assertion in quick_inI1_outR1 introduced with key rollover
|
||||
support in 1.92. Assertion failed in Responder when Source
|
||||
was not the same as Initiator.
|
||||
|
||||
- reduce level of routine logging. Add --debug-lifecycle,
|
||||
a temporary hack: it controls some logging, not debugging.
|
||||
|
||||
- Reorganize code to prepare for asynchronous DNS.
|
||||
|
||||
- Arrange for our file descriptors to be close-on-exec so that
|
||||
the updown script won't inherit them. Some library facilities
|
||||
(syslog?) may not be as careful.
|
||||
|
||||
- Fix assertion failure in DNS record handling. Provoked by a
|
||||
malformed key in a TXT record. Introduced in 1.93.
|
||||
|
||||
- Change Responder cookie generation algorithm so that a particular
|
||||
peer no longer gets the same cookie each time.
|
||||
|
||||
- Tidy and correct setting and resetting cur_* variables. A per-connection
|
||||
debug setting could provoke a GLOBALS_ARE_RESET assertion failure.
|
||||
|
||||
- Fix handing of pending list in release_dead_interfaces:
|
||||
connection must be released before it is removed from host_pair list.
|
||||
|
||||
- Ignore IPv6 interface addresses that are of link-local scope.
|
||||
We think that they are never relevant. Trying to bind to these
|
||||
addresses without a scope-id causes bind to balk.
|
||||
|
||||
|
||||
Changes since 1.93 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- Only run the up-* updown script for tunnel eroutes, not shunt
|
||||
eroutes.
|
||||
|
||||
- Now only --routed connections may be initiated on demand
|
||||
(i.e. triggered by SADB_ACQUIRE triggered by trapped outbound packet).
|
||||
Among other things, this eliminates a bug whereby an ACQUIRE
|
||||
could be ascribed by Pluto to a Road Warrior template connection.
|
||||
Pluto will now refuse to --route a Road Warrior template.
|
||||
|
||||
- Correct bug that lost track of a bare shunt table entry.
|
||||
Add debugging logging for changes to that table.
|
||||
|
||||
|
||||
Changes since 1.92 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- [andreas.steffen@strongsec.com] Bug fix: carrying Phase 1 ID
|
||||
over when instantiating a different RW connection due to
|
||||
revelation of Phase 2 IDs. This bug should only have affected
|
||||
X509-authenticated negotiations.
|
||||
|
||||
- add more context to log and status lines. If the connection or
|
||||
state is an instance, show the peer involved; if Opportunistic, also
|
||||
show the client subnet.
|
||||
|
||||
- seed rand(3) with bytes from /dev/urandom.
|
||||
|
||||
- propose 1536 MODP Group before 1024 MODP Group. This generates
|
||||
more entropy, so should be a little safer. And slower.
|
||||
|
||||
- add --debug-dns flag
|
||||
|
||||
- During Phase 1, when an RSA Public Key is require, only query DNS
|
||||
for a KEY record for an Opportunistic connection. (This does not
|
||||
change the whack --keyid way of querying for a KEY record during
|
||||
preconfiguration.)
|
||||
|
||||
- Multiple RSA public keys, if available, will be tried when
|
||||
authenticating a signature. This facilitates key rollover.
|
||||
New whack flag --addkey.
|
||||
Multiple DNS TXT and KEY records are used if they are found
|
||||
(but only one Responder is tried).
|
||||
|
||||
- no longer try to figure out --rsasig or --psk if neither specified.
|
||||
This would require an extra DNS lookup for a KEY record.
|
||||
|
||||
Changes since 1.91 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- got rid of caching of DNS results. They might become stale.
|
||||
|
||||
- Added --dontrekey option for a connection. Crudely useful
|
||||
for Road Warrior and Opportunistic connections.
|
||||
|
||||
- Ignore the Commit Flag. This should let us interoperate with
|
||||
implementations that insist on it. The damage should be minor.
|
||||
|
||||
- Don't split the topology line of --status output. The output is now
|
||||
more consistent (if wider).
|
||||
|
||||
- Improve diagnosis when ipsec.secrets has a non-indented "}"
|
||||
at the end of an RSA private key.
|
||||
|
||||
- Savatier Sébastien <SebastienSavatier@lyon.msi-sa.fr>:
|
||||
fix bug in emitting explicit IP address ID payload.
|
||||
|
||||
- Support inbound policy check of source and destination inner
|
||||
addresses of tunneled packets. This will make it possible to
|
||||
prevent one peer from successfully spoofing packets from another.
|
||||
|
||||
- Use poll(2) to check for MSG_ERRQUEUE messages before recvfrom:
|
||||
even though select(2) says that there is a message, a plain
|
||||
recvfrom(2) can block if the only message is on MSG_ERRQUEUE. I
|
||||
think that this blocking is a kernel bug, or at least a
|
||||
documentation bug. Also check for MSG_ERRQUEUE messages before
|
||||
sendto(2): their presence can cause sendto to fail confusingly (i.e.
|
||||
the failure has nothing to do with the actual sendto).
|
||||
|
||||
|
||||
Changes since 1.9 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- SIGTERM now causes Pluto to exit cleanly.
|
||||
|
||||
- if --nofork is used, Pluto prints the line "Pluto initialized" to
|
||||
standard out after creating the lock file and the control socket.
|
||||
|
||||
- the startup script relies on the property that whack can be
|
||||
used immediately after the pluto command finishes (i.e.
|
||||
right after the parent process of the daemon exits).
|
||||
In the past, the control socket used by whack was created
|
||||
after the fork: not necessarily before the parent exits.
|
||||
This race condition has been eliminated.
|
||||
|
||||
- refined the code for DODGE_DH_MISSING_ZERO_BUG to ensure
|
||||
Responder never drops a negotiation.
|
||||
|
||||
- added and exploited builddiag(), a routine make it easier to add
|
||||
intermediate context to diagnostics.
|
||||
|
||||
- For purposes of IPv4, Pluto will now only consider interfaces that
|
||||
are "up". It has always ignored those configured with address
|
||||
0.0.0.0, thus ignoring "down" interfaces in most cases.
|
||||
|
||||
- add a list of interface pairs to --status output.
|
||||
|
||||
- replace signal(2) calls with sigaction(2) calls: glibc has further
|
||||
broken the semantics of signal(2). We want slow system calls
|
||||
to be interruptable and not be restarted.
|
||||
|
||||
- improved error message for lack of preshared key by showing
|
||||
IDs that were used in lookup. Collateral tidying.
|
||||
|
||||
- documented complex logic of routing and erouting in routing.txt
|
||||
|
||||
- When a connection is --routed, a route is installed to direct
|
||||
outbound packets destined for the peer's client to go to the ipsec
|
||||
interface implicit in the connection. This is not allowed for Road
|
||||
Warrior connections -- they are strictly inbound. For Opportunistic
|
||||
connections, a new default root is installed that points to the
|
||||
ipsec interface. Note that the route does not take into account the
|
||||
source address. In addition, a TRAP shunt eroute is installed to
|
||||
catch any traffic sent on the not-yet-initiated connection.
|
||||
|
||||
- When an outbound packet is trapped by the TRAP shunt eroute,
|
||||
Pluto attempts to initiate the corresponding connection.
|
||||
If the attempt fails because an Opportunistic connection was used
|
||||
and no gateway information was found, a PASS shunt eroute is
|
||||
installed (with no provision for automatic removal).
|
||||
|
||||
- if negotiation fails at a later point, a shunt eroute is installed.
|
||||
The kind of shunt is a policy decision. It is specified as part of
|
||||
the connection. (Untested; can not be specified in ipsec.conf.)
|
||||
|
||||
- When an inbound negotiation doesn't match a specific connection,
|
||||
and there is an Opportunistic connection, Pluto will try to respond
|
||||
using that connection.
|
||||
|
||||
- Every 2 minutes (SHUNT_SCAN_INTERVAL seconds), Pluto scans for
|
||||
|
||||
+ PASS eroutes that it installed that haven't been used recently.
|
||||
These will be deleted.
|
||||
|
||||
+ HOLD eroutes for which Pluto hasn't received a PFKEY_ACQUIRE message.
|
||||
For any it finds, it will attempt an opportunistic initiate.
|
||||
|
||||
- We no longer allow Phase 1 negotiations that we initiate to switch
|
||||
which connection is being used based on the Peer's Phase 1 ID.
|
||||
The fact that we used to do so was probably a bug.
|
||||
|
||||
- When Pluto as the Responder receives the Peer's Phase 1 ID, it is
|
||||
now willing to use a connection with a different ID and private
|
||||
RSA key for our end. Nothing has committed us to the current guess.
|
||||
|
||||
- Changes in internal data structures to aid in better tracking of
|
||||
history of attempted and successful communication. Needed for
|
||||
effective Opportunism.
|
||||
+ struct host_pair represents information about pairs of hosts.
|
||||
+ "Orientation" is done as soon as possible rather than as late
|
||||
as possible.
|
||||
+ an arbitrary number of Quick Mode negotiations may now queue
|
||||
for the completion of a Main Mode negotiation. Formerly,
|
||||
a negotiation could only use a previously completed Keying Channel.
|
||||
|
||||
|
||||
Changes since 1.8 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- [Svenning Soerensen] correct check requiring OAKLEY_LIFE_TYPE
|
||||
attribute before OAKLEY_LIFE_DURATION.
|
||||
|
||||
- Improved whack diagnostics for various cases of failure to connect
|
||||
with Pluto.
|
||||
|
||||
- Added function state_with_serialno to allow a serial number to be
|
||||
used as a safe reference to a state object. This avoids the risk
|
||||
of dangling pointers.
|
||||
|
||||
- Add crude support for PF_KEY SADB_ACQUIRE messages from the kernel.
|
||||
These cause the initiation of opportunistic negotiation.
|
||||
|
||||
- More processing of PF_KEY messages from the kernel. We check that
|
||||
each message we send to the kernel elicits a response. Other messages
|
||||
are queued to be processed at the head of the event loop.
|
||||
|
||||
- Fix bug in find_client_connection. The manifestation is a Pluto
|
||||
segfault when a negotiation successfully gets to Phase 2, but there
|
||||
is no connection with the appropriate clients AND there is no
|
||||
wildcarded connection using our same host interface (not even an
|
||||
inappropriate one).
|
||||
|
||||
- Purely internal change: simplify EVENT_SO_DISCARD logic.
|
||||
|
||||
- Accept GROUP_DESCRIPTION in IPCA (IPcomp SA) proposal. Although
|
||||
this SHOULD NOT appear according to
|
||||
draft-shacham-ippcp-rfc2393bis-05.txt 4.1, it should harmlessly help
|
||||
interoperation.
|
||||
|
||||
- Adjust to whether KLIPS supports IPCOMP. If it does not, ignore
|
||||
--compress policy flag in Connections. So Pluto would then neither
|
||||
propose nor accept IPCOMP transforms.
|
||||
|
||||
|
||||
Changes since 1.7 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- Allow IPcomp transformations to use "well known CPIs". This
|
||||
perversion allows better interoperation.
|
||||
|
||||
- Added rather experimental code to exploit IP_RECVERR. This facility
|
||||
allows us to report who refuses our packets when they are refused.
|
||||
I don't understand the documentation of the mechanism, hence the
|
||||
experimental nature of our use of it. Our code is pretty ugly too.
|
||||
|
||||
- [Svenning Soerensen] found a bug in the calculation of the verb for
|
||||
the updown script and proposed a fix. The -host suffix was being
|
||||
used when the client subnet contained only one IP address, even if
|
||||
that address was not of the host.
|
||||
|
||||
- [Svenning Soerensen] Allow Phase 1 ID Payloads of type FQDN and
|
||||
user@FQDN to specify UDP/500 explicitly as per RFC2407 (IPSEC DOI)
|
||||
4.6.2.
|
||||
|
||||
- When responding in Quick mode, after switching to an appropriate
|
||||
connection based on the ID payloads, copy the connection's IPSEC
|
||||
policy flags into the state object. Do this before consulting these
|
||||
flags.
|
||||
|
||||
- --status output now indicates when a connection is an instance
|
||||
of another. "POLICY_" has been removed from the display of each
|
||||
policy flag, reducing clutter. An extra space has been added to
|
||||
further indent lines in the --status report.
|
||||
|
||||
- Fixed a bug in displaying subnets in the error message
|
||||
"cannot respond to IPsec SA request..."
|
||||
|
||||
- In SA proposals, accept CPIs that are 4 bytes too, as long as
|
||||
the high order 2 bytes are 0.
|
||||
|
||||
- bug fix: no longer allocate tunnel SPIs below IPSEC_DOI_SPI_OUR_MIN.
|
||||
|
||||
- Added recognition (not support) for new Assigned Numbers for AES
|
||||
and friends.
|
||||
|
||||
|
||||
Changes since 1.6 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- only accept a proposal with compression if the connection has the
|
||||
POLICY_COMPRESSION flag. Normally, these flags don't affect what we
|
||||
propose. In this case, we need this control since our IPCOMP
|
||||
implementation has a history of crashing.
|
||||
|
||||
- Fixed nasty bug in connections.c:fc_try(). For a Quick Mode
|
||||
exchange, if Pluto picked a connection as a starting point
|
||||
that had no peer client, it would not accept any proposed
|
||||
peer client. On the other hand, if it picked a connection
|
||||
with a peer client, it would not accept any proposal without
|
||||
a peer client.
|
||||
|
||||
|
||||
Changes since 1.5 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- added a global pluto option --uniqueids. If this is enabled,
|
||||
whenever a new ISAKMP SA is established, any connections with
|
||||
the same Peer Id but different Peer IP address are unoriented,
|
||||
blowing away any of their SAs. This should help eliminate
|
||||
dangling Road Warrior connections when the same Road Warrior
|
||||
reconnects. It thus requires that IDs not be shared by hosts
|
||||
(a previously legal but probably useless capability).
|
||||
|
||||
- introduced clearer notation:
|
||||
+ --host %any signifying any IP address, for Road Warrior,
|
||||
replacing 0.0.0.0 or 0::0
|
||||
+ --nexthop %direct signifying "same IP as peer", replacing
|
||||
0.0.0.0 or 0::0
|
||||
+ %any and %any6 as indices in ipsec.secrets to match IP addresses of
|
||||
Road Warriors (replacing 0.0.0.0 or 0::0)
|
||||
+ --host %opportunistic signifying that the peer is actually
|
||||
to be discovered from the reverse DNS entry for the peer's client.
|
||||
This replaces --host 0.0.0.0 --client 0.0.0.0/32 (and IPv6 variants).
|
||||
|
||||
- be more strict about Phase 2 ID payloads (the ones that specify clients):
|
||||
reject if they specify protocol or port (which we do not support).
|
||||
|
||||
- Remove support for Diffie Hellman MODP 768 Group. Increase
|
||||
support for MODP 1536 Group.
|
||||
|
||||
- Remove NO_RSA option -- patent expired!!
|
||||
|
||||
- Improve support for newer resolvers.
|
||||
|
||||
- [initially from Svenning Soerensen <svenning@post5.tele.dk>]
|
||||
support IPcomp (compression)
|
||||
|
||||
- [mostly Gerhard Gessler <gessler@iabg.de>] initial support for IPv6.
|
||||
|
||||
- As part of the IPv6 support, changes were made to the Pluto/updown
|
||||
interface. See pluto(8) for the details. One oft-requested feature
|
||||
is the new PLUTO_*_CLIENT environment variables. The changes are
|
||||
"upward compatible", so the PLUTO_VERSION environment variable
|
||||
setting was changed from 1.0 to 1.1. Unfortunately, this will break
|
||||
many customized updown scripts.
|
||||
|
||||
- Prototype support for initiating and responding to opportunistic
|
||||
negotiation. A connection is considered for instantiation for
|
||||
opportunism if it has a peer of %opportunistic (the connection
|
||||
description must not specify a client for the peer). Currently, the
|
||||
only way to provoke an opportunistic initiation is to use whack to
|
||||
simulate the interception of an outbound flow (do a "whack --help"
|
||||
and look at opportunistic initiation). These features are not
|
||||
documented because they are experimental. Limitations: no actual
|
||||
interception of packets, DNS query synchronous.
|
||||
|
||||
- in ipsec.secrets, if multiple entries are the best match for the
|
||||
connection, they must all have the same secret. In the past
|
||||
there was no code to compare RSA keys, so separate RSA entries
|
||||
were assumed to be different. Now they are compared.
|
||||
|
||||
- Introduce now() to protect against clock being set backwards. The
|
||||
risk is that events might be delayed a lot. Still no protection
|
||||
against clock being moved forward.
|
||||
|
||||
- Don't "discover" interfaces that share IP addresses with others.
|
||||
This avoids an assertion failure. Eventually, Pluto will have to
|
||||
ask KLIPS about interfaces.
|
||||
|
||||
- prevent infinite loop decoding certain malformed DNS records
|
||||
|
||||
- explain "Phase 1", "Phase 2", "Main Mode", and "Quick Mode"
|
||||
|
||||
- fiddled with "max number of retransmissions" diagnostic to add a bit
|
||||
of explanation.
|
||||
|
||||
|
||||
Changes since 1.4 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- reorganized how messages are logged. More of the serious messages
|
||||
are distinguished with the code RC_LOG_SERIOUS and hence should
|
||||
make it through ipsec auto's filter.
|
||||
|
||||
- Reserve Message IDs only within their ISAKMP SA. This eliminates
|
||||
the unbounded memory requirement when reserving them per peer.
|
||||
|
||||
- Pluto's retransmission logic has been improved:
|
||||
+ the initial retransmission occurs after 10 seconds of silence,
|
||||
down from 30 seconds. The theory is that this will ungum a
|
||||
lost-packet situation more quickly
|
||||
+ the delay after each retransmission is twice the delay before
|
||||
it -- exponential backoff
|
||||
+ In the special case of the first message initiating Main Mode,
|
||||
when --keyingtries is 0 (meaning unlimited retries), Pluto
|
||||
will attempt more retransmissions at the same rate (no
|
||||
exponential backoff). This cuts down on the pointless
|
||||
busywork while a peer isn't responding.
|
||||
|
||||
- Pluto will no longer generate SPIs in the range 0x100-0xFFF.
|
||||
This has the effect of reserving this range for manual keying.
|
||||
Of course Pluto will still allow its peer to use this range.
|
||||
|
||||
- Fixed another bug in Road Warrior support. In responding to Phase 2
|
||||
/ Quick Mode, once the client subnets (if any) are known, Pluto must
|
||||
reselect which connection to use. If it didn't happen to be using
|
||||
the right one already, and no ID was explicitly specified for the
|
||||
peer, and the right one is a Road Warrior connection, the right one
|
||||
would not be found.
|
||||
|
||||
|
||||
Changes since 1.3 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- Pluto can now acquire a public key from DNS. It must be told
|
||||
to do so. Hint: --pubkeyrsa is optional when specifying keyid.
|
||||
|
||||
- On the Responder, if a connection is to be routed, and the peer has
|
||||
a client that is a fixed subnet, and that subnet is already routed
|
||||
for other connections, and that route conflicts, Pluto will unorient
|
||||
the old connections (deleting the SAs that depend on the old route)
|
||||
on the theory that they have been superseded. Too bad we can't
|
||||
otherwise tell when a connection is outdated.
|
||||
|
||||
- Support for netlink has been removed. We always use PFKEYV2.
|
||||
Pluto no longer #includes any kernel headers!
|
||||
|
||||
- Added a TODO file
|
||||
|
||||
- Road Warrior support is unconditionally included. No more need to
|
||||
define ROAD_WARRIOR_FUDGE.
|
||||
|
||||
- Fixed bug preventing Road Warrior connections being instantiated
|
||||
during the connection reselection prompted by receipt of Phase 1 ID
|
||||
Payload [Kai Martius <kai@secunet.de>]. Fixed bug that caused Phase
|
||||
1 ID to be ignored by connection reselection prompted by receipt of
|
||||
Phase 2 client IDs.
|
||||
|
||||
|
||||
Changes since 1.2 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- fixed deficiencies in id handling
|
||||
|
||||
- changed to use updown script for routing (and firewalling)
|
||||
|
||||
- In quick Mode, when Responder, avoid selecting same SPIs as
|
||||
initiator. This prevents KEYMAT being the same in both directions.
|
||||
See Ferguson and Schneier: "A Cryptographic Evaluation of IPsec",
|
||||
http://www.counterpane.com/ipsec.pdf, 5.6 #2.
|
||||
|
||||
- In Quick Mode, when Responder, install inbound IPsec SA one
|
||||
message earlier. This eliminates the chance of a message being
|
||||
sent before the SA is established.
|
||||
|
||||
- slight complication to RSA private key lookup rules to allow
|
||||
match to an entry with multiple identities for the host.
|
||||
|
||||
- support per-connection debugging flags
|
||||
|
||||
- more use of PFKEY (RGB+DHR)
|
||||
|
||||
- inbound SAs are now spigrped and an inbound IPIP SA is created
|
||||
if tunneling is used. This more symmetric with outbound processing
|
||||
and it allows KLIPS to check that the correct SAs are all applied.
|
||||
|
||||
- The way SA lifetime limits are proposed and accepted is better
|
||||
documented. whack now complains when a specified value exceeds the
|
||||
limit.
|
||||
|
||||
|
||||
Changes since 1.1 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- Updated constants to track newer IETF drafts
|
||||
|
||||
- added support for RSA Signature authentication
|
||||
+ augmented demux.c to support packet syntax differences
|
||||
due to authentication technique.
|
||||
+ preshared.c now can record RSA private keys
|
||||
+ whack --keyid --pubkeyrsa records RSA public keys
|
||||
+ whack --unlisten to allow a sequence of whack operations to be atomic
|
||||
with respect to IKE traffic (eg. loading public keys)
|
||||
+ ipsec_doi.c will now do RSA Signature authentication
|
||||
+ new policy bits are added to select authentication method (--rsasig, --psk)
|
||||
|
||||
- started towards more general ids (@FQDN and user@FQDN,
|
||||
in addition to IP addresses).
|
||||
+ Note: there is *no* meaning attached to the id used beyond
|
||||
being an identifier. Almost no syntax checking is done.
|
||||
+ these forms of id work in:
|
||||
o ipsec.secrets indices
|
||||
o whack's --keyid for defining public keys
|
||||
o id payloads (generated and accepted)
|
||||
o --id option for each side in a connection description
|
||||
+ the Id may be an IP address that isn't that of one end
|
||||
(but it must authenticate)
|
||||
+ once and ID payload is received, Pluto will reconsider which
|
||||
potential connection should be used. It makes sure that any
|
||||
authentication already done would apply to the new connection
|
||||
too. This should make RSASIG + Road Warrior useful.
|
||||
|
||||
- [RGB, Peter Onion, and DHR] start of PFKEY2 support
|
||||
|
||||
|
||||
Changes since 1.00 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- revamped rekeying:
|
||||
+ added --rekeyfuzz; defaults to 100% so lifetime must now be
|
||||
more than twice rekeymargin
|
||||
+ added rekeying for responders (but rigged to favour initiators)
|
||||
+ [BUGFIX] responder of an exchange will not reinitiate
|
||||
the exchange if it does not complete
|
||||
|
||||
- Renamed --rekeywindow to --rekeymargin to match ipsec.conf.
|
||||
The old name will be accepted for a while.
|
||||
|
||||
- improved error and debugging messages
|
||||
|
||||
- updated list of notification messages (but we still don't support
|
||||
them).
|
||||
|
||||
- In ID payload, support range representation, but only for a subnet.
|
||||
This may improve interoperability
|
||||
|
||||
- scatter asterisks in debugging code to support EMACS outline mode.
|
||||
|
||||
- many internal changes were made to improve to code. This should
|
||||
make it easier to add new states. There should be few behaviour
|
||||
changes.
|
||||
|
||||
- whack --status now shows the SPIs for established SAs.
|
||||
|
||||
- [BUGFIX] DH values are now represented with the length specified by
|
||||
the group description, not the length actually needed. About one
|
||||
time in 256, this will make a difference. In those cases, the new
|
||||
Pluto won't interoperate with old Plutos. It looks as if this
|
||||
change brings us in line with other IKE daemons. Added a fudge
|
||||
(select with DODGE_DH_MISSING_ZERO_BUG) so that when a problem
|
||||
arises, a new replacement exchange is initiated (idea from John
|
||||
Gilmore).
|
||||
|
||||
- [BUGFIX] whack no longer assumes that UNIX domain sockets preserve
|
||||
record boundaries (they don't). This faulty assumption caused
|
||||
whack's exit status to be unreliable
|
||||
|
||||
- [BUGFIX] pluto now correctly defaults the client subnet in a
|
||||
connection created for a Road Warrior exchange.
|
||||
|
||||
- [BUGFIX] Road Warrior code now supports multiple connections
|
||||
terminating in a particular Road Warrior node (allowing all
|
||||
appropriate combinations of host and subnets to be simultaneously
|
||||
connected).
|
||||
|
||||
- [BUGFIX] fix various peculiar Road Warrior crashes.
|
||||
|
||||
- [BUGFIX] fix spurious deletion of control socket when lock could
|
||||
not be acquired (Thomas Bellman <bellman@cendio.se>)
|
||||
|
||||
- [BUGFIX] interface discovery properly ignores nonAF_NET interfaces
|
||||
|
||||
|
||||
Changes since .92 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- Communication between whack and pluto is now done using UNIX domain
|
||||
sockets. This channel can be secured!
|
||||
|
||||
- liberalized ISAKMP SA acceptance. Now anything up to and including
|
||||
16 bytes long is accepted. How silly.
|
||||
|
||||
- All ISAKMP messages in UDP packets generated by pluto are now
|
||||
explicitly padded to be a multiple of 4 octets long. This was wrong
|
||||
if certain big numbers (eg. nonces) happened to have leading zero
|
||||
octets.
|
||||
|
||||
- set socket option SO_REUSEADDR on pluto's whack socket. This allows
|
||||
Pluto to quickly restart.
|
||||
|
||||
- Use new, consistent notation for topology:
|
||||
client===host---nexthop...nexthop---host===client
|
||||
|
||||
- prefix every line of status output with connection name. This
|
||||
allows selection of output using grep.
|
||||
|
||||
- Replaced system's assert with passert. This sends the diagnostic
|
||||
to syslog.
|
||||
|
||||
- Changed secrets file name processing to support sh-like "globbing"
|
||||
for file names.
|
||||
|
||||
- Where appropriate, log messages are prefixed by their connection
|
||||
name and state object serial numbers. Connection names are quoted
|
||||
with double quotes and serial numbers are prefixed with the number
|
||||
sign (#). Otherwise, where appropriate, log messages are prefixed
|
||||
by the IP address and port number from which the current message
|
||||
was sent.
|
||||
|
||||
- some attempt at making the messages more helpful
|
||||
+ warnings when authentication (preshared secrets) failure is
|
||||
likely cause of the observed symptom
|
||||
+ status message now highlights which SAs are the most recent
|
||||
(those are the ones that are subject to rekeying)and which are
|
||||
erouted.
|
||||
+ state names are slightly improved
|
||||
+ status message prints the "meaning" of a state after its name.
|
||||
|
||||
- the policy options of a connection (--pfs, --authenticate, --encrypt,
|
||||
(but not --tunnel)) now apply to negotiations being responded to.
|
||||
They continue to apply to negotiations initiated by Pluto.
|
||||
|
||||
- The Oakley group used for PFS in Phase 2 is dictated by the initiator.
|
||||
We used to dictate one of our choice. To increase the chances for
|
||||
success, we now dictate the same group as was used in Phase 1.
|
||||
|
||||
- First, some context. The "negotiated" lifetime of an SA is actually
|
||||
dictated by the initiator. If the responder doesn't like this
|
||||
lifetime, it can tell the initiator in a NOTIFY message. Pluto
|
||||
doesn't do this. Instead, it will just expire the lifetime sooner
|
||||
than negotiated. In the past, Pluto only initiated rekeying if it
|
||||
was the initiator. Now, a responder Pluto will initiate rekeying if
|
||||
it is going to expire the SA earlier than negotiated. To prevent an
|
||||
explosion of SAs, rekeying will only be done if the SA is the newest
|
||||
one for its connection. Rekeying of IPsec SA will respect the
|
||||
security properties of the old SA at the level of policy options
|
||||
(i.e. --pfs, --authenticate, --encrypt, --tunnel).
|
||||
|
||||
- Replaced --rekeytries with --keyingtries. This option now applies
|
||||
to initial keying as well as rekeying, hence the name change. Even
|
||||
though initial keying will now try more than once, whack logging
|
||||
will be stopped after the first attempt. The value 0 is taken to
|
||||
mean, effectively, infinity: don't give up.
|
||||
|
||||
|
||||
Changes since .91 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- A hack has been added to support mobile or anonymous initiators.
|
||||
|
||||
- The isakmp-secrets file has been renamed ipsec.secrets and the
|
||||
format spruced up to aid scalability. Entries now can be shared
|
||||
between relevant machines verbatim. An include facility was added.
|
||||
The file is now only read upon --listen commands.
|
||||
|
||||
- If --firewall appears on our end of a connection, Pluto will
|
||||
add a firewall rule to enable appropriate forwarding, without
|
||||
masquerading for any route it adds. It will delete the rule
|
||||
when it deletes the route.
|
||||
|
||||
- When Pluto thinks whack's message is malformed, it now says so
|
||||
to whack, not just syslog.
|
||||
|
||||
- In addition to the messages traditionally sent back to whack,
|
||||
non-debugging messages sent to the log that relate to whack's
|
||||
current activity are copied to whack. Whack's exit status now
|
||||
reflects the last message (if any) returned by Pluto. This should
|
||||
allow a script to tell, for example, if an SA was established.
|
||||
|
||||
- top-level payload parsing has been centralized. This should make
|
||||
it easier to add new features. Payload ordering constraints have
|
||||
are now just those required by RFC2409 (IKE). In most cases,
|
||||
Pluto will now ignore duplicated packets. It should recover better
|
||||
from the reception of a corrupt packet.
|
||||
|
||||
- Interface discovery is more clever. It notes each configured
|
||||
interface with a name ipsec[0-9] as a virtual public interface and
|
||||
considers any interface with a different kind of name and the same
|
||||
IP address to be the corresponding real public interface. This is
|
||||
only done when Pluto starts, so any interfaces of interest must be
|
||||
configured before then. This feature allows Pluto to support multiple
|
||||
public networks.
|
||||
|
||||
- Pluto now exploits the fact that eroutes only conflict if their
|
||||
local clients AND peer clients are the same. So we can now support
|
||||
multiple subnets behind our security gateway all talking to clients
|
||||
behind another security gateway.
|
||||
|
||||
- Switched to using ipsec_spi_t to represent SPIs. In the process
|
||||
fixed a related bug found by Peter Onion.
|
||||
|
||||
|
||||
Changes since .9 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
[incomplete]
|
||||
|
||||
- Message IDs are now random, rather than counting up from 1. This
|
||||
should help keep messages in different but simultaneous Phase 2
|
||||
exchanges being mixed up.
|
||||
- syslogged informative (i.e. debugging) messages are now prefixed
|
||||
with "| " to make the easier to ignore.
|
||||
- forbid zero cookies. Among other things, this prevents feedback
|
||||
confusing Pluto.
|
||||
- Use serial numbers to cause most recent of available ISAKMP SAs
|
||||
to be chosen. Also useful in debugging output.
|
||||
- Pluto will now only listen to Whack on the loopback interface
|
||||
(important security limitation).
|
||||
- implement rekeying, based on time, for ISAKMP and IPsec SAs
|
||||
- Whack now talks to Pluto using TCP. This allows status information
|
||||
to be returned to Whack. For now, not much interesting is sent back.
|
||||
The TCP port is the *same* as the IKE port -- no longer 1 greater.
|
||||
Pluto closes the socket once the "goal" is established or the
|
||||
state object is freed. All this will evolve.
|
||||
- For SAs that were initiated by Pluto, Pluto will try to replace
|
||||
the SA before it expires. There is a 10 minute window
|
||||
(SA_REPLACEMENT_WINDOW) in which this can occur.
|
||||
- Support --peer_nexthop for initiator of ISAKMP SA.
|
||||
- Support --optionsfrom <file>
|
||||
- be more specific about error conditions: for each STF_FAIL,
|
||||
designate which notification message most applies.
|
||||
- use these results in reporting to whack
|
||||
- make whack back-talk look like FTP messages
|
||||
- add and use notion of (potential) connection database. All scripts change!
|
||||
- fix handling of the variable form of attribute
|
||||
- don't allow --initiate before --listen
|
||||
- use new number for ESP_NULL
|
||||
- demand each transform include an ENCAPSULATION_MODE attribute
|
||||
- demand each AH transform include an appropriate AUTH_ALGORITHM attribute
|
||||
- add not-yet-standardized OAKLEY_GROUP 5 (MODP 1536)
|
||||
- since KLIPS only allows one IPsec SA to be routed to a particular
|
||||
subnet (for a peer's client), detect when a subnet is engaged.
|
||||
If we are replacing that SA, OK. Otherwise, balk.
|
||||
- [experimental] exploit the new UDP 500 hole to support host mode.
|
||||
- add --route and --unroute: hysteresis in routing should prevent
|
||||
packets flowing in the clear during IPsec SA transitions.
|
||||
- add --status to display the internal state of Pluto.
|
||||
- deleted misleading README; other resources fulfill its role
|
||||
- eliminated EVENT_CLEANUP: using EVENT_RETRANSMIT seemed more correct
|
||||
- gave special meaning to combination of delete and add
|
||||
- improved and documented combinations of whack command types
|
||||
- improved logging
|
||||
- added and used LEAK_DETECTIVE. Fixed some leaks.
|
||||
|
||||
|
||||
Changes between .85 and .9 release by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
[incomplete]
|
||||
|
||||
- change pluto and whack's argument processing to use getopt_long:
|
||||
the syntax and expressive power is quite different.
|
||||
- allow selection of debugging output. Change pluto to accept
|
||||
arguments for specifying this. Change whack and pluto allow
|
||||
settings to change during a run.
|
||||
- make most controls for debugging run-time rather than compile-time.
|
||||
This required the addition of many command line arguments (see README)
|
||||
- support 3DES encryption of Oakley messages (OAKLEY_3DES_CBC)
|
||||
- accept modestly long attribute values (32 bits) for
|
||||
OAKLEY_LIFE_DURATION and SA_LIFE_DURATION.
|
||||
|
||||
|
||||
Changes between .7alpha and .85 (highlights) by D. Hugh Redelmeier <hugh@mimosa.com>
|
||||
|
||||
- support RHL5.0 (glibc): avoid clash between
|
||||
<netinet/in.h> and <asm/byteorder.h>
|
||||
- Lessons from porting to Solaris: endianness, careful typing, alignment,
|
||||
correct fd_set bugs in call_server(), correct rnd.c to use sig_atomic_t
|
||||
- Makefile: add distlist target to put out names of files in distribution
|
||||
- Makefile: when installing binaries, move old ones to .OLD
|
||||
- add and exploit pb_stream mechanism for systematically decoding and
|
||||
encoding packets
|
||||
- More flexible security policy, but still hard-wired.
|
||||
- support new Oakley group (2 -- modp 1024)
|
||||
- make returned IPsec proposal for acceptance a copy of winning proposal
|
||||
(as per spec)
|
||||
- add and use generic interface to hash functions
|
||||
- add many comments referencing the draft standards
|
||||
- change all uses of stdout to use stderr instead (choice between stdout
|
||||
and stderr was haphazard)
|
||||
- fix SPI stuff: Oakley and IPSEC SPIs are different beasts
|
||||
- generate initial IPSEC SPI as a random number (avoid clashes)
|
||||
- fix layout bug for struct isakmp_transform
|
||||
- fix several dangerous memory allocation and buffer overflow errors;
|
||||
eliminate all inline uses of calloc (use a wrapper)
|
||||
- avoid memory leak due to uncleared mpz variables
|
||||
- general tidying and restructuring; get rid of many "magic" numbers
|
||||
- de-lint everywhere (add -Wall -Wmissing-prototypes to Makefile)
|
||||
- switch from BSD b* functions to ANSI mem* functions
|
||||
- get rid of bitfields
|
||||
- generate the correct amount of keying material (PRF feedback, if needed)
|
||||
- improve get_preshared_key (new format too)
|
||||
- improve handling of informational exchanges. Still poor.
|
||||
- improve tracing output
|
||||
- print version information (whack and pluto)
|
||||
- wherever an enum-like value is printed, print the name of the value
|
||||
- make duplicate_state() duplicate the st_myidentity_type field.
|
||||
- make kernel interface do required route commands
|
||||
- open and close /dev/ipsec more carefully
|
||||
- support separate keys for esp encryption and esp authentication
|
||||
File diff suppressed because it is too large
Load Diff
|
|
@ -0,0 +1,64 @@
|
|||
We haven't kept proper track of everybody who has helped us, alas, but
|
||||
here's a first attempt at acknowledgements...
|
||||
|
||||
Most of the FreeS/WAN software has been done by Richard Guy Briggs
|
||||
(KLIPS), D. Hugh Redelmeier (Pluto), Michael Richardson (technical lead,
|
||||
KLIPS, testing, etc.), Henry Spencer (past technical lead, scripts,
|
||||
libraries, packaging, etc.), Sandy Harris (documentation), Claudia
|
||||
Schmeing (support, documentation), and Sam Sgro (support, releases).
|
||||
Peter Onion has collaborated extensively with RGB on PFKEY2 stuff. The
|
||||
original version of our IPComp code came from Svenning Soerensen, who has
|
||||
also contributed various bug fixes and improvements.
|
||||
|
||||
Kai Martius (admin@imib.med.tu-dresden.de) contributed the initial
|
||||
version of the code supporting PFS.
|
||||
|
||||
The first versions of KLIPS were done by John Ioannidis <ji@hol.gr>. The
|
||||
first versions of Pluto (and further work on KLIPS) were done by Angelos
|
||||
D. Keromytis <angelos@dsl.cis.upenn.edu>.
|
||||
|
||||
Richard Guy Briggs (rgb@conscoop.ottawa.on.ca) and Peter Onion
|
||||
(ponion@srd.bt.co.uk) added the PFKEY2 support.
|
||||
|
||||
The MD5 implementation is from RSADSI, so this package must include the
|
||||
following phrase: "derived from the RSA Data Security, Inc. MD5
|
||||
Message-Digest Algorithm". It is not under the GPL; see details in
|
||||
linux/net/ipsec/ipsec_md5c.c.
|
||||
|
||||
The LIBDES library by Eric Young is used. It is not under the GPL -- see
|
||||
details in libdes/COPYRIGHT -- although he has graciously waived the
|
||||
advertising clause for FreeS/WAN use of LIBDES.
|
||||
|
||||
The SHA-1 code is derived from Steve Reid's; it is public domain.
|
||||
|
||||
Some bits of Linux code, notably drivers/net/new_tunnel.c and net/ipv4/ipip.c,
|
||||
are used in heavily modified forms.
|
||||
|
||||
The radix-tree code from 4.4BSD is used in a modified form. It is not
|
||||
under the GPL; see details in klips/net/ipsec/radij.c.
|
||||
|
||||
The lib/pfkeyv2.h header file contains public-domain material published in
|
||||
RFC 2367.
|
||||
|
||||
Delete SA code is based on Mathieu Lafon's Notification/Delete patch.
|
||||
|
||||
Peter Onion has been immensely helpful in finding portability bugs in
|
||||
general, and in making FreeS/WAN work on the Alpha in particular. Rob
|
||||
Hatfield likewise found and fixed some problems making it work on the
|
||||
Netwinder.
|
||||
|
||||
John S. Denker of AT&T Shannon Labs has found a number of bugs the hard
|
||||
way, has pointed out various problems (some of which we have fixed!) in
|
||||
using the software in production applications, and has suggested some
|
||||
substantial improvements to the documentation.
|
||||
|
||||
Marc Boucher <marc@mbsi.ca> did a quick-and-dirty port of KLIPS to the
|
||||
Linux 2.2.x kernels, at a time when we needed it badly, and has helped
|
||||
chase down 2.2.xx bugs and keep us current with 2.4.x development.
|
||||
|
||||
John Gilmore organized the FreeS/WAN project and continues to direct it.
|
||||
Hugh Daniel handles day-to-day management, customer interface, and both
|
||||
constructive and destructive testing. See the project's web page
|
||||
<http://www.freeswan.org> for other contributors to this project and
|
||||
related ones.
|
||||
|
||||
|
|
@ -0,0 +1,53 @@
|
|||
The following people have contributed major resources and/or significant patches
|
||||
to Openswan 2.x. There are many more unlisted contributors. If you feel you or
|
||||
your company are missing, please contact paul@nohats.ca.
|
||||
|
||||
Michael Richardson <mcr@xelerance.com> - KLIPS, OCF, IKEv2, testing
|
||||
Paul Wouters <paul@nohats.ca> - IKEv2, packaging, porting, support
|
||||
Antony Antony <antony@xelerance.com> - IKEv2, testing
|
||||
Ken Bantoft <ken@xelerance.com> - DPD, cross compiling, integration
|
||||
Bart Trojanowski <bart@xelerance.com> - OCF, KLIPS
|
||||
Herbert Xu <herbert@gondor.apana.org.au> - NETKEY / XFRM, IKEv2, NAT-T
|
||||
David McCullough <David_Mccullough@securecomputing.com> - KLIPS, OCF
|
||||
D. Hugh Redelmeier <hugh@mimosa.com> - Bug fixer extraordinaire
|
||||
Andreas Steffen <andreas.steffen@strongsec.com> - X.509 Certificates
|
||||
Dr{Who} on Freenode - Porting NAT-T + XAUTH to Openswan 2.x
|
||||
Jacco de Leeuw <jacco2@dds.nl> - Fixes for MS Interop
|
||||
Mathieu Lafon <mlafon@arkoon.net> - NAT-T Support
|
||||
Nate Carlson - Force NAT-T framework, KLIPS for 2.6, etc...
|
||||
Stephen Bevan <stephen@dino.dnsalias.com> - RFC2409 port selectors
|
||||
Tuomo Soini <tis@foobar.fi> - NETKEY, KLIPS, _updown scripts and more
|
||||
Matthew Galgoci <mgalgoci@redhat.com>
|
||||
Miloslav Trmac <mitr@redhat.com>
|
||||
Avesh Agarwal <avagarwa@redhat.com>, USE_LIBNSS, SElinux
|
||||
Hiren Joshi Cyberoam [www.cyberoam.com] - Various fixes
|
||||
Shingo Yamawaki <Shingo.Yamawaki@jp.sony.com> - Various KLIPS patches
|
||||
willy@w.ods.org
|
||||
|
||||
Openswan is a fork of the FreeS/WAN 2.04 codebase.
|
||||
Please see the doc/CREDITS.freeswan file from FreeS/WAN for details on
|
||||
original work.
|
||||
|
||||
Xelerance (http://www.xelerance.com) has sponsored the continued development
|
||||
of Openswan since version 1.0
|
||||
|
||||
RedHat (http://www.redhat.com/) sponsored the development of IKEv2, USE_LIBNSS
|
||||
and various fixes related to NETKEY.
|
||||
|
||||
Secure Computing / Snapgear contributed OCF integration, DYNDNS support and many
|
||||
other KLIPS and userland related fixes.
|
||||
|
||||
IXIA Communications (http://www.ixiacom.com/) sponsored the cryptographic
|
||||
refit in pluto, which permitted Aggressive mode to be incorporated safely.
|
||||
|
||||
Sony Japan contributed many fixes to KLIPS, and sponsored IPsec/L2TP development
|
||||
|
||||
Siemens Germany sponsored IPsec/L2TP development
|
||||
|
||||
Emagister sponsored IPsec/L2TP development
|
||||
|
||||
Astaro (http://www.astaro.de/) contributed patches and hardware
|
||||
|
||||
HP (http://www.hp.com/) donated hardware
|
||||
|
||||
Cyberoam (http://www.cyberoam.com/) contributed various patches
|
||||
Binary file not shown.
|
After 
(image error) Size: 35 KiB |
|
|
@ -0,0 +1,996 @@
|
|||
<?xml version="1.0" standalone="no"?>
|
||||
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN"
|
||||
"http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
|
||||
<!-- Creator: fig2dev Version 3.2 Patchlevel 5-alpha5 -->
|
||||
<!-- CreationDate: Sat Aug 20 10:49:05 2005 -->
|
||||
<!-- Magnification: 1.050 -->
|
||||
<svg xmlns="http://www.w3.org/2000/svg" width="12.5in" height="22.5in" viewBox="43 -1124 15040 26942">
|
||||
<g style="stroke-width:.025in; stroke:black; fill:none">
|
||||
<!-- Line -->
|
||||
<polyline points="4771,4110
|
||||
6519,4110
|
||||
6519,4771
|
||||
4771,4771
|
||||
4771,4110
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="5574" y="4393" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
examine isa_xchg</text>
|
||||
<!-- Line -->
|
||||
<polyline points="5763,5385
|
||||
7511,5385
|
||||
7511,6047
|
||||
5763,6047
|
||||
5763,5385
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="6566" y="5669" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
find/create state</text>
|
||||
<!-- Text -->
|
||||
<text x="6566" y="5905" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
object</text>
|
||||
<!-- Line -->
|
||||
<polyline points="4771,6661
|
||||
6519,6661
|
||||
6519,7322
|
||||
4771,7322
|
||||
4771,6661
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="5574" y="6944" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
determine valid</text>
|
||||
<!-- Text -->
|
||||
<text x="5622" y="7181" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
transitions</text>
|
||||
<!-- Line -->
|
||||
<polyline points="4771,7984
|
||||
6519,7984
|
||||
6519,8645
|
||||
4771,8645
|
||||
4771,7984
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="5574" y="8267" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
verify state</text>
|
||||
<!-- Text -->
|
||||
<text x="5622" y="8503" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
is not suspended</text>
|
||||
<!-- Line -->
|
||||
<polyline points="4771,9354
|
||||
6519,9354
|
||||
6519,10015
|
||||
4771,10015
|
||||
4771,9354
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="5574" y="9637" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
decrypt packet</text>
|
||||
<!-- Text -->
|
||||
<text x="5622" y="9874" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
if appropriate</text>
|
||||
<!-- Line -->
|
||||
<polyline points="4771,10724
|
||||
6519,10724
|
||||
6519,11385
|
||||
4771,11385
|
||||
4771,10724
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="5574" y="11007" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
calculate hash</text>
|
||||
<!-- Text -->
|
||||
<text x="5622" y="11244" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
if appropriate</text>
|
||||
<!-- Line -->
|
||||
<polyline points="5102,10015
|
||||
5102,10551
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5039 10279
|
||||
5102 10594
|
||||
5165 10279
|
||||
5102 10342
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="5102,11385
|
||||
5102,11921
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5039 11649
|
||||
5102 11964
|
||||
5165 11649
|
||||
5102 11712
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4771,12094
|
||||
6519,12094
|
||||
6519,12755
|
||||
4771,12755
|
||||
4771,12094
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="5574" y="12377" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
enforce ordering</text>
|
||||
<!-- Text -->
|
||||
<text x="5622" y="12614" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
of payloads</text>
|
||||
<!-- Line -->
|
||||
<polyline points="3732,13653
|
||||
5480,13653
|
||||
5480,14314
|
||||
3732,14314
|
||||
3732,13653
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="4535" y="13937" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
state specific func</text>
|
||||
<!-- Line -->
|
||||
<polyline points="4062,14314
|
||||
4062,14850
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="3999 14578
|
||||
4062 14893
|
||||
4125 14578
|
||||
4062 14641
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="3732,15023
|
||||
5480,15023
|
||||
5480,15685
|
||||
3732,15685
|
||||
3732,15023
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="4535" y="15307" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
complete_state_</text>
|
||||
<!-- Text -->
|
||||
<text x="4582" y="15543" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
transition()</text>
|
||||
<!-- Line -->
|
||||
<polyline points="5338,16488
|
||||
7086,16488
|
||||
7086,17149
|
||||
5338,17149
|
||||
5338,16488
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="6141" y="16771" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
STF_IGNORE</text>
|
||||
<!-- Line -->
|
||||
<polyline points="5338,17858
|
||||
7086,17858
|
||||
7086,18519
|
||||
5338,18519
|
||||
5338,17858
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="6141" y="18141" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
STF_SUSPEND</text>
|
||||
<!-- Line -->
|
||||
<polyline points="5338,19370
|
||||
7086,19370
|
||||
7086,20031
|
||||
5338,20031
|
||||
5338,19370
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="6141" y="19653" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
STF_OK</text>
|
||||
<!-- Line -->
|
||||
<polyline points="5338,20929
|
||||
7086,20929
|
||||
7086,21590
|
||||
5338,21590
|
||||
5338,20929
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="6141" y="21212" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
STF_FATAL</text>
|
||||
<!-- Line -->
|
||||
<polyline points="5338,22393
|
||||
7086,22393
|
||||
7086,23055
|
||||
5338,23055
|
||||
5338,22393
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="6141" y="22677" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="101" text-anchor="middle" >
|
||||
STF_INTERNAL_ERROR</text>
|
||||
<!-- Line -->
|
||||
<polyline points="5338,25133
|
||||
7086,25133
|
||||
7086,25795
|
||||
5338,25795
|
||||
5338,25133
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="6141" y="25417" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
STF_FAIL</text>
|
||||
<!-- Line -->
|
||||
<polyline points="5338,23669
|
||||
7086,23669
|
||||
7086,24330
|
||||
5338,24330
|
||||
5338,23669
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="6141" y="23952" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="89" text-anchor="middle" >
|
||||
STF_TOO_MUCH_CRYPTO</text>
|
||||
<!-- Line -->
|
||||
<polyline points="8314,20078
|
||||
10062,20078
|
||||
10062,20740
|
||||
8314,20740
|
||||
8314,20078
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="9118" y="20362" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
send_packet()</text>
|
||||
<!-- Line -->
|
||||
<polyline points="7086,13653
|
||||
8834,13653
|
||||
8834,14314
|
||||
7086,14314
|
||||
7086,13653
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="7889" y="13937" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
encrypt packet</text>
|
||||
<!-- Line -->
|
||||
<polyline points="992,13653
|
||||
2740,13653
|
||||
2740,14314
|
||||
992,14314
|
||||
992,13653
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="1795" y="13937" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
continuation</text>
|
||||
<!-- Line -->
|
||||
<polyline points="3732,-141
|
||||
5480,-141
|
||||
5480,519
|
||||
3732,519
|
||||
3732,-141
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="4535" y="141" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
read_packet()</text>
|
||||
<!-- Line -->
|
||||
<polyline points="3732,1275
|
||||
5480,1275
|
||||
5480,1937
|
||||
3732,1937
|
||||
3732,1275
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="4535" y="1559" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
process_packet()</text>
|
||||
<!-- Line -->
|
||||
<polyline points="4771,2692
|
||||
8078,2692
|
||||
8078,3354
|
||||
4771,3354
|
||||
4771,2692
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="6330" y="3118" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
de-marshal payloads (in_struct)</text>
|
||||
<!-- Line -->
|
||||
<polyline points="1984,1842
|
||||
1984,5401
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="1921 5129
|
||||
1984 5444
|
||||
2047 5129
|
||||
1984 5192
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="5102,1937
|
||||
5102,2566
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5039 2295
|
||||
5102 2609
|
||||
5165 2295
|
||||
5102 2358
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="5102,7322
|
||||
5102,7858
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5039 7586
|
||||
5102 7901
|
||||
5165 7586
|
||||
5102 7649
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="5102,8645
|
||||
5102,9181
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5039 8909
|
||||
5102 9224
|
||||
5165 8909
|
||||
5102 8972
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4062,1937
|
||||
4062,13480
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="3999 13208
|
||||
4062 13523
|
||||
4125 13208
|
||||
4062 13271
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4251,15685
|
||||
4251,16771
|
||||
5212,16771
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5179 16803
|
||||
5304 16771
|
||||
5179 16740
|
||||
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4251,15685
|
||||
4251,18188
|
||||
5212,18188
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5179 18220
|
||||
5304 18188
|
||||
5179 18157
|
||||
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4251,18755
|
||||
4251,21259
|
||||
5212,21259
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5179 21291
|
||||
5304 21259
|
||||
5179 21228
|
||||
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4251,20173
|
||||
4251,22677
|
||||
5212,22677
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5179 22708
|
||||
5304 22677
|
||||
5179 22645
|
||||
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4251,21496
|
||||
4251,23999
|
||||
5212,23999
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5179 24031
|
||||
5304 23999
|
||||
5179 23968
|
||||
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4251,22960
|
||||
4251,25464
|
||||
5212,25464
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5179 25496
|
||||
5304 25464
|
||||
5179 25433
|
||||
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4251,17149
|
||||
4251,19653
|
||||
5212,19653
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5179 19685
|
||||
5304 19653
|
||||
5179 19622
|
||||
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="6425,20031
|
||||
6425,20362
|
||||
8188,20362
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="8155 20393
|
||||
8281 20362
|
||||
8155 20330
|
||||
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="5480,13795
|
||||
6960,13795
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="6927 13826
|
||||
7053 13795
|
||||
6927 13763
|
||||
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="7039,14173
|
||||
5606,14173
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5639 14141
|
||||
5513 14173
|
||||
5639 14204
|
||||
|
||||
" style="stroke:#000000;stroke-width:16;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="2740,13889
|
||||
3606,13889
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="3334 13952
|
||||
3649 13889
|
||||
3334 13826
|
||||
3397 13889
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="5291,18425
|
||||
1559,18425
|
||||
1559,14566
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:10 10 10;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="1622 14635
|
||||
1559 14383
|
||||
1496 14635
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:#000000;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4535,-850
|
||||
4535,-313
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="4472 -585
|
||||
4535 -270
|
||||
4598 -585
|
||||
4535 -522
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4535,519
|
||||
4535,1149
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="4472 877
|
||||
4535 1192
|
||||
4598 877
|
||||
4535 940
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="5102,4771
|
||||
5102,6535
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5039 6263
|
||||
5102 6578
|
||||
5165 6263
|
||||
5102 6326
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="6141,4771
|
||||
6141,5259
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="6078 4987
|
||||
6141 5302
|
||||
6204 4987
|
||||
6141 5050
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Line -->
|
||||
<polyline points="5149,3354
|
||||
5109,3984
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polygon points="5063 3708
|
||||
5107 4027
|
||||
5189 3716
|
||||
5122 3775
|
||||
|
||||
" style="stroke:#000000;stroke-width:32;
|
||||
fill:white;"/>
|
||||
<!-- Text -->
|
||||
<text x="3307" y="1653" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="end" >
|
||||
msg_digest populated</text>
|
||||
<!-- Text -->
|
||||
<text x="2173" y="5622" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="start" >
|
||||
md->st connected</text>
|
||||
<!-- Text -->
|
||||
<text x="4440" y="14645" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="start" >
|
||||
returns STF_*</text>
|
||||
<!-- Text -->
|
||||
<text x="1464" y="15590" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="end" >
|
||||
DNS lookup</text>
|
||||
<!-- Text -->
|
||||
<text x="1464" y="15858" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="end" >
|
||||
DH calculation</text>
|
||||
<!-- Text -->
|
||||
<text x="1464" y="16125" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="end" >
|
||||
g^x calculation</text>
|
||||
<!-- Text -->
|
||||
<text x="1464" y="16393" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="end" >
|
||||
(LDAP lookup)</text>
|
||||
<!-- Text -->
|
||||
<text x="1464" y="16661" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="end" >
|
||||
(RSA sig check)</text>
|
||||
<!-- Text -->
|
||||
<text x="1464" y="16929" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="end" >
|
||||
(radius/pam)</text>
|
||||
<!-- Text -->
|
||||
<text x="7275" y="18188" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="start" >
|
||||
md -> st->st_suspended_md</text>
|
||||
<!-- Text -->
|
||||
<text x="8787" y="20929" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="start" >
|
||||
md freed</text>
|
||||
<!-- Text -->
|
||||
<text x="5196" y="-944" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
Time Sequence diagram of packet receive in Pluto</text>
|
||||
<!-- Text -->
|
||||
<text x="4724" y="-566" fill="#000000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="start" >
|
||||
select() indicates fd read</text>
|
||||
<!-- Line -->
|
||||
<polyline points="9448,3354
|
||||
12094,3354
|
||||
12094,4015
|
||||
9448,4015
|
||||
9448,3354
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="10913" y="3779" fill="#ff0000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
proc recvRawMessage</text>
|
||||
<!-- Line -->
|
||||
<polyline points="8314,9921
|
||||
10960,9921
|
||||
10960,10582
|
||||
8314,10582
|
||||
8314,9921
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="9779" y="10346" fill="#ff0000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
proc recvMessage</text>
|
||||
<!-- Line -->
|
||||
<polyline points="8314,12755
|
||||
10960,12755
|
||||
10960,13417
|
||||
8314,13417
|
||||
8314,12755
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="9779" y="13181" fill="#ff0000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
proc changeState</text>
|
||||
<!-- Line -->
|
||||
<polyline points="8267,14551
|
||||
10913,14551
|
||||
10913,15212
|
||||
8267,15212
|
||||
8267,14551
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="9732" y="14976" fill="#ff0000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
proc outgoingClearText</text>
|
||||
<!-- Line -->
|
||||
<polyline points="12425,20220
|
||||
15070,20220
|
||||
15070,20881
|
||||
12425,20881
|
||||
12425,20220
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="13889" y="20645" fill="#ff0000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
proc sixtySeconds</text>
|
||||
<!-- Line -->
|
||||
<polyline points="8314,19039
|
||||
10960,19039
|
||||
10960,19700
|
||||
8314,19700
|
||||
8314,19039
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="9779" y="19464" fill="#ff0000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
proc avoidEmitting</text>
|
||||
<!-- Line -->
|
||||
<polyline points="8314,15685
|
||||
10960,15685
|
||||
10960,16346
|
||||
8314,16346
|
||||
8314,15685
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Text -->
|
||||
<text x="9779" y="16110" fill="#ff0000" font-family="Times" font-style="normal" font-weight="normal" font-size="152" text-anchor="middle" >
|
||||
proc adjustFailure</text>
|
||||
<!-- Line -->
|
||||
<polyline points="8078,2881
|
||||
9921,2881
|
||||
9921,3322
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="9889 3193
|
||||
9921 3319
|
||||
9952 3193
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="9496,3732
|
||||
6236,3732
|
||||
6236,4078
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="6204 3949
|
||||
6236 4075
|
||||
6267 3949
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="6519,9637
|
||||
8787,9637
|
||||
8787,9889
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="8755 9760
|
||||
8787 9886
|
||||
8818 9760
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="8787,10582
|
||||
8787,11574
|
||||
5133,11574
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="5262 11543
|
||||
5137 11574
|
||||
5262 11606
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4062,12897
|
||||
8283,13038
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="8153 13064
|
||||
8280 13038
|
||||
8155 13002
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="8314,13181
|
||||
4488,13322
|
||||
4488,13622
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="4456 13492
|
||||
4488 13618
|
||||
4519 13492
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="7842,14362
|
||||
7842,14834
|
||||
8236,14834
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="8107 14866
|
||||
8233 14834
|
||||
8107 14803
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="8267,14976
|
||||
7511,14976
|
||||
7511,14393
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="7543 14522
|
||||
7511 14396
|
||||
7480 14522
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="10913,14881
|
||||
13889,14881
|
||||
13889,20188
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="13858 20059
|
||||
13889 20185
|
||||
13921 20059
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="11007,16015
|
||||
13228,16015
|
||||
13228,20188
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="13196 20059
|
||||
13228 20185
|
||||
13259 20059
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="11007,19370
|
||||
12944,19370
|
||||
12944,20188
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="12913 20059
|
||||
12944 20185
|
||||
12976 20059
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="12425,20456
|
||||
10094,20456
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="10223 20425
|
||||
10097 20456
|
||||
10223 20488
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="7606,20456
|
||||
7606,19370
|
||||
8283,19324
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="8156 19363
|
||||
8280 19324
|
||||
8152 19301
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="8314,19464
|
||||
7842,19464
|
||||
7888,20377
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="7849 20249
|
||||
7887 20374
|
||||
7911 20246
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="8314,16110
|
||||
4283,16298
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="4410 16259
|
||||
4286 16297
|
||||
4413 16322
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
<!-- Line -->
|
||||
<polyline points="4251,15968
|
||||
8283,15968
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
stroke-linejoin:miter; stroke-linecap:butt;
|
||||
stroke-dasharray:50 50;
|
||||
"/>
|
||||
<!-- Arrowhead on XXXpoint -->
|
||||
<polyline points="8154 15999
|
||||
8280 15968
|
||||
8154 15937
|
||||
" style="stroke:#ff0000;stroke-width:16;
|
||||
"/>
|
||||
</g>
|
||||
</svg>
|
||||
|
After (image error) Size: 26 KiB |
|
|
@ -0,0 +1,156 @@
|
|||
Notes on Pluto Conventions
|
||||
==========================
|
||||
|
||||
Pluto previously had it's own stylistic conventions but they were
|
||||
abandoned and starting from Libreswan 3.4 only Linux Kernel coding style
|
||||
is accepted.
|
||||
|
||||
Please read the Coding Style document thoroughly.
|
||||
|
||||
https://www.kernel.org/doc/Documentation/CodingStyle
|
||||
|
||||
- you can use checkpatch.pl utility from kernel to check your patches
|
||||
before committing.
|
||||
|
||||
git diff | checkpatch.pl --no-tree --no-signoff -
|
||||
|
||||
- sample formatting:
|
||||
|
||||
void fun(char *s) {
|
||||
if (s == NULL) {
|
||||
return "";
|
||||
} else {
|
||||
switch (*s) {
|
||||
default:
|
||||
s++;
|
||||
/* fall through */
|
||||
case '\0':
|
||||
return s;
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
- try to keep lines shorter than 80 columns
|
||||
|
||||
- space should be canonical:
|
||||
+ no line should have trailing whitespace
|
||||
+ leading whitespace should use tabs where possible
|
||||
+ indentation should be precise
|
||||
+ there should be no empty lines at the end of a file.
|
||||
+ a single space separates a control flow reserved word and its operand.
|
||||
+ no space follows a function name
|
||||
|
||||
- if a case falls through, say so explicitly. See example above.
|
||||
|
||||
- the operand of return need not be parenthesized
|
||||
|
||||
- be careful with types. For example, use size_t and ssize_t.
|
||||
Use const wherever possible. Avoid casts.
|
||||
|
||||
- we pretend that C has a strong boolean type.
|
||||
We define type bool with constants TRUE and FALSE.
|
||||
|
||||
Other types should not be used where a boolean is natural: as the
|
||||
complete expression in a test or as an operand of ||, &&, or !.
|
||||
Hence:
|
||||
if (s == NULL)
|
||||
One exception: lset_t values may be treated as booleans
|
||||
(technically they are, in the original sense of the word)
|
||||
|
||||
It rarely makes sense to compare a boolean value with TRUE or FALSE.
|
||||
|
||||
- don't use malloc/free -- use the wrappers (see defs.h)
|
||||
They guarantee allocation or death.
|
||||
|
||||
- streq(a,b) is clearer than strcmp(a,b) == 0.
|
||||
memeq is clearer than memcmp.
|
||||
zero is clearer than memset (but zero(&array) not zero(array)!).
|
||||
|
||||
- use passert, not assert.
|
||||
|
||||
- memset/calloc/alloc_thing can set memory to zero but a pointer set
|
||||
to zero is not guaranteed be NULL (surprising feature of the C
|
||||
language). What makes this insidious is that on most systems
|
||||
the result will be NULL.
|
||||
|
||||
- side-effects of expressions are to be avoided.
|
||||
BAD: if (i++ == 9)
|
||||
OK: i++;
|
||||
|
||||
- variables are to have as small a scope as is possible.
|
||||
Move definitions into inner blocks whenever possible.
|
||||
Often initializing definitions become possible and are clearer.
|
||||
User "static" to limit a variable or function scope to a file.
|
||||
|
||||
- within a block that has declarations, separate the declarations from
|
||||
the other statements with a blank line.
|
||||
|
||||
- Modern C allows declarations and statements to be mingled. We have
|
||||
avoided doing this but there are times where declaring in the middle
|
||||
of a block is clearer.
|
||||
|
||||
- all functions and variables that are exported from a .c file should
|
||||
be declared in that file's corresponding header file. Make sure
|
||||
that the .c file includes the header so that the declaration and the
|
||||
definition will be checked for consistency by the compiler.
|
||||
|
||||
There is almost no excuse for the "extern" keyword in a .c file.
|
||||
|
||||
There is almost no excuse for the declaration of an object within a
|
||||
.h file to NOT have the "extern" keyword. We are a bit lax about
|
||||
this for function declarations (because a definition is clearly
|
||||
marked by the presence of the function body).
|
||||
|
||||
Technical detail: C has declarations of variables and functions.
|
||||
Some of these are definitions. Some are even "tentative definitions".
|
||||
We don't want definitions or tentative definitions within .h files.
|
||||
We don't want declarations that are not definitions within .c files.
|
||||
"extern" usually signifies a variable declaration that isn't a definition.
|
||||
|
||||
- "magic numbers" are suspect. Most integers in code stand for
|
||||
something. They should be given a name (using enum or #define), and
|
||||
that name used consistently.
|
||||
|
||||
It is especially bad if the same number appears in two places in a way
|
||||
that requires both to be changed together (eg. an array bound and
|
||||
a loop bound). Often sizeof or ELEMSOF can help.
|
||||
|
||||
- Conditional compilation is to be avoided. It makes testing hard.
|
||||
|
||||
When conditionally compiling large chunks of text, it is good to put
|
||||
comments on #else and #endif to show what they match with. I use !
|
||||
to indicate the sense of the test:
|
||||
|
||||
#ifdef CRUD
|
||||
#else /* !CRUD */
|
||||
#endif /* !CRUD */
|
||||
|
||||
#ifndef CRUD
|
||||
#else /* CRUD */
|
||||
#endif /* CRUD */
|
||||
|
||||
- Never put two statements on one line. Especially empty statements.
|
||||
REALLY BAD: if (cat);
|
||||
Exception: some macro definitions.
|
||||
|
||||
- C preprocessor macros are implemented by a kind of textual substitution.
|
||||
Be sure to put parentheses around references to macro arguments and
|
||||
around the whole macro body.
|
||||
|
||||
If the body is meant to be a statement, put braces around it instead.
|
||||
|
||||
#define RETURN_STF_FAILURE(f) \
|
||||
{ int r = (f); if (r != NOTHING_WRONG) return STF_FAIL + r; }
|
||||
|
||||
Note: to make a macro body behave as a statement, some conventions
|
||||
wrap the whole body with do { } while (0) (eg. the Linux Kernel Style).
|
||||
This makes a difference only in this case, where a such a macro is used
|
||||
unbraced in the then part of an if with an else.
|
||||
if (test)
|
||||
MACRO();
|
||||
else
|
||||
whatever;
|
||||
|
||||
If the macro body were only wrapped in braces, the result would be a
|
||||
syntax error (automatically detected and easily fixed). This
|
||||
tradeoff favours simple braces.
|
||||
|
|
@ -0,0 +1,8 @@
|
|||
|
||||
|
||||
https://www.iana.org/assignments/enterprise-numbers
|
||||
|
||||
The Private Enterprise Number 41286 has been assigned to The Libreswan Project.
|
||||
|
||||
We might use this code in the future for DHCP,DHCP relay and/or SNMP add-ons.
|
||||
|
||||
|
|
@ -0,0 +1,2 @@
|
|||
|
||||
See http://ocf-linux.sourceforge.net/
|
||||
|
|
@ -0,0 +1,78 @@
|
|||
|
||||
XAUTH Server Support
|
||||
|
||||
Based on FlexS/WAN code from Colubris Networks (www.colubris.com)
|
||||
Ported to Openswan by Xelerance (www.xelerance.com)
|
||||
|
||||
Sponsored by Astaro AG (www.astaro.com)
|
||||
Ported to OpenSwan by Sean Mathews Nu Tech Software (www.nutech.com)
|
||||
Also added MD5/DES password file support and reworked the PAM code.
|
||||
|
||||
XAUTH server code rewritten for Openswan 2.1.0 to permit both client
|
||||
and server side code. Many changes, most visible to user.
|
||||
|
||||
Threading fixed by Philippe Vouters in Libreswan
|
||||
|
||||
Addresspool support added by Antony Antony in Libreswan
|
||||
|
||||
Installation:
|
||||
|
||||
1. If you want to be able to yse PAM to authenticate XAUTH users, you need
|
||||
to also set USE_XAUTHPAM=true in Makefile.inc.
|
||||
|
||||
2. Build & Install as normal.
|
||||
3. If you compiled with PAM then 'make install' will install the
|
||||
/etc/pam.d/pluto policy file for pam authentication.
|
||||
|
||||
5. If you choose the password file then create /etc/ipsec.d/passwd
|
||||
with the following format.
|
||||
|
||||
userid:password:conname
|
||||
|
||||
comments are allowed by putting a '#' as the first character of any
|
||||
line. You can allow a user access to any connection class in ipsec.conf
|
||||
by leaving the last field of the password file blank or '*', or set this
|
||||
field to the connection name in your ipsec.conf that you wish this person
|
||||
to have access.
|
||||
|
||||
Note:
|
||||
The crypt() call is used for passwords. This means you can have DES,
|
||||
MD5, SHA1 and SHA256 hashed passwords. In FIPS mode, DES and MD5 will
|
||||
not be available, so it is recommended not to use those.
|
||||
Some of these can be generated by any typical htpasswd utility.
|
||||
If you need to use DES, use htpasswd -d instead of htpasswd -m
|
||||
|
||||
Configuration:
|
||||
|
||||
One way to use XAUTH is to have a single shared secret (PSK) for
|
||||
all road warriors. This is not the best, but it does work.
|
||||
|
||||
Configure as normal in /etc/ipsec.secrets - eg:
|
||||
|
||||
0.0.0.0 1.2.3.4 : PSK "a secret for the xauth users"
|
||||
|
||||
On your conn block, simply add "{left|right}xauthserver=yes"
|
||||
to enable XAUTH, and "{right|left}xauthclient=yes" for the client side.
|
||||
|
||||
Client Configurations - these assume you already have a working
|
||||
non-XAUTH connection setup. These are tested and known to work.
|
||||
|
||||
SSH Sentinel 1.4.1
|
||||
|
||||
Note: 1.4.0 has a bug where it will only propose Single DES,
|
||||
even if Single DES is disabled. Please upgrade to 1.4.1
|
||||
|
||||
1. On the Rule Properties page, enabled Extended Authentication.
|
||||
2. Click [Settings], and check "Use authentication method types"
|
||||
3. Optionally set it to save your login information.
|
||||
|
||||
|
||||
SafeNet SoftRemote LT 10.0
|
||||
|
||||
1. In Security Policy Editor, open your connection.
|
||||
2. Expand Authentication (Phase 1)
|
||||
3. Click on Proposal, and set the Authentication Method to
|
||||
"Pre-Shared Key; Extended Authentication"
|
||||
|
||||
Note: SoftRemote does not let you save your Username and Password.
|
||||
|
||||
|
|
@ -0,0 +1,4 @@
|
|||
Be careful with deploying this. Please see:
|
||||
|
||||
http://marc.info/?l=selinux&m=119550363105309&w=2
|
||||
https://bugzilla.redhat.com/show_bug.cgi?id=235720
|
||||
|
|
@ -0,0 +1,146 @@
|
|||
|
||||
An IPsec roadmap is released as RFC 6071, which lists a lot of relevant RFCs
|
||||
|
||||
https://tools.ietf.org/html/rfc6071/
|
||||
|
||||
To search for IPsec related RFCs and drafts, see:
|
||||
|
||||
https://datatracker.ietf.org/doc/search/?name=ipsec&rfcs=on&activeDrafts=on&oldDrafts=on
|
||||
|
||||
IPsec related RFC's and drafts (list will likely be out of date):
|
||||
|
||||
|
||||
Overview RFCs
|
||||
|
||||
RFC 6071 IP Security (IPsec) and Internet Key Exchange (IKE) Document Roadmap
|
||||
RFC 2401 Security Architecture for the Internet Protocol
|
||||
RFC 2411 IP Security Document Roadmap
|
||||
RFC 4301 Security Architecture for the Internet Protocol
|
||||
|
||||
Basic protocols
|
||||
|
||||
RFC 2402 IP Authentication Header (AH)
|
||||
RFC 2406 IP Encapsulating Security Payload (ESP)
|
||||
RFC 4302 IP Authentication Header
|
||||
RFC 4303 IP Encapsulating Security Payload (ESP)
|
||||
|
||||
Key management
|
||||
|
||||
RFC 2367 PF_KEY Key Management API, Version 2
|
||||
RFC 2407 The Internet IP Security Domain of Interpretation for ISAKMP
|
||||
RFC 2408 Internet Security Association and Key Management Protocol (ISAKMP)
|
||||
RFC 2409 The Internet Key Exchange (IKE)
|
||||
RFC 2412 The OAKLEY Key Determination Protocol
|
||||
RFC 2528 Internet X.509 Public Key Infrastructure
|
||||
|
||||
RFC 3526 More Modular Exponential (MODP) Diffie-Hellman groups for Internet Key Exchange (IKE)
|
||||
RFC 3664 The AES-XCBC-PRF-128 Algorithm for the Internet Key Exchange Protocol (IKE)
|
||||
RFC 4109 Algorithms for Internet Key Exchange version 1 (IKEv1)
|
||||
RFC 4210 Internet X.509 Public Key Infrastructure Certificate Management Protocol (CMP)
|
||||
RFC 4304 Extended Sequence Number (ESN) Addendum to IPsec Domain of Interpretation (DOI) for Internet Security Association and Key Management Protocol (ISAKMP)
|
||||
RFC 4306 Internet Key Exchange (IKEv2) Protocol
|
||||
RFC 4718 IKEv2 Clarifications and Implementation Guidelines
|
||||
RFC 5996 Internet Key Exchange Protocol Version 2 (IKEv2)
|
||||
|
||||
Procedural and Operational RFC's
|
||||
|
||||
RFC 1750 Randomness Recommendations for Security
|
||||
RFC 1918 Address Allocation for Private Internets
|
||||
RFC 1984 IAB and IESG Statement on Cryptographic Technology and the Internet
|
||||
RFC 2144 The CAST-128 Encryption Algorithm
|
||||
RFC 3457 Requirements for IPsec Remote Access Scenarios
|
||||
RFC 3585 IPsec Configuration Policy Information Model
|
||||
|
||||
Detailed RFC's on specific cryptograhpic algorithms and ciphers
|
||||
|
||||
RFC 1321 The MD5 Message-Digest Algorithm
|
||||
RFC 1828 IP Authentication using Keyed MD5
|
||||
RFC 1829 The ESP DES-CBC Transform
|
||||
RFC 1851 The ESP Triple DES Transform
|
||||
RFC 1852 IP Authentication using Keyed SHA
|
||||
RFC 2085 HMAC-MD5 IP Authentication with Replay Prevention
|
||||
RFC 2104 HMAC: Keyed-Hashing for Message Authentication
|
||||
RFC 2202 Test Cases for HMAC-MD5 and HMAC-SHA-1
|
||||
RFC 2403 The Use of HMAC-MD5-96 within ESP and AH
|
||||
RFC 2404 The Use of HMAC-SHA-1-96 within ESP and AH
|
||||
RFC 2405 The ESP DES-CBC Cipher Algorithm With Explicit IV
|
||||
RFC 2410 The NULL Encryption Algorithm and Its Use With IPsec
|
||||
RFC 2451 The ESP CBC-Mode Cipher Algorithms
|
||||
RFC 2521 ICMP Security Failures Messages
|
||||
RFC 3566 The AES-XCBC-MAC-96 Algorithm and Its Use With IPsec
|
||||
RFC 3602 The AES-CBC Cipher Algorithm and Its Use with IPsec
|
||||
RFC 3686 Using Advanced Encryption Standard (AES) Counter Mode With IPsec Encapsulating Security Payload (ESP)
|
||||
RFC 4196 The SEED Cipher Algorithm and Its Use with IPsec
|
||||
RFC 4106 The Use of Galois/Counter Mode (GCM) in IPsec Encapsulating Security Payload (ESP)
|
||||
RFC 4305 Cryptographic Algorithm Implementation Requirements for Encapsulating Security Payload (ESP) and Authentication Header (AH)
|
||||
RFC 4307 Cryptographic Algorithms for Use in the Internet Key Exchange Version 2 (IKEv2)
|
||||
RFC 4308 Cryptographic Suites for IPsec
|
||||
RFC 4309 Using Advanced Encryption Standard (AES) CCM Mode with IPsec Encapsulating Security Payload (ESP)
|
||||
|
||||
Dead Peer Detection RFC's
|
||||
|
||||
RFC 3706 A Traffic-Based Method of Detecting Dead Internet Key Exchange (IKE) Peers
|
||||
|
||||
NAT-Traversal and UDP encapsulation RFC's
|
||||
|
||||
RFC 2709 Security Model with Tunnel-mode IPsec for NAT Domains
|
||||
RFC 3715 IPsec-Network Address Translation (NAT) Compatibility Requirements
|
||||
RFC 3947 Negotiation of NAT-Traversal in the IKE
|
||||
RFC 3948 UDP Encapsulation of IPsec ESP Packets
|
||||
|
||||
|
||||
RFCs for secure DNS service, which IPSEC may use
|
||||
|
||||
RFC 2137 Secure Domain Name System Dynamic Update
|
||||
RFC 2230 Key Exchange Delegation Record for the DNS
|
||||
RFC 2535 Domain Name System Security Extensions
|
||||
RFC 2536 DSA KEYs and SIGs in the Domain Name System (DNS)
|
||||
RFC 2537 RSA/MD5 KEYs and SIGs in the Domain Name System (DNS)
|
||||
RFC 2538 Storing Certificates in the Domain Name System (DNS)
|
||||
RFC 2539 Storage of Diffie-Hellman Keys in the Domain Name System (DNS)
|
||||
RFC 3007 Secure Domain Name System (DNS) Dynamic Update
|
||||
RFC 3008 Domain Name System Security (DNSSEC) Signing Authority [obsoleted]
|
||||
RFC 3130 Notes from the State-Of-The-Technology: DNSSEC
|
||||
RFC 3225 Indicating Resolver Support of DNSSEC
|
||||
RFC 3226 DNSSEC and IPv6 A6 aware server/resolver message size requirements
|
||||
RFC 3757 Domain Name System KEY (DNSKEY) Resource Record (RR) Secure Entry Point (SEP) Flag [obsoleted]
|
||||
RFC 3845 DNS Security (DNSSEC) NextSECure (NSEC) RDATA Format [obsoleted]
|
||||
RFC 4025 A Method for Storing IPsec Keying Material in DNS
|
||||
RFC 4033 DNS Security Introduction and Requirements
|
||||
RFC 4034 Resource Records for the DNS Security Extensions
|
||||
RFC 4035 Protocol Modifications for the DNS Security Extensions
|
||||
RFC 4322 Opportunistic Encryption using the Internet Key Exchange (IKE)
|
||||
|
||||
RFC's related to L2TP, often used in combination with IPsec
|
||||
|
||||
RFC 2341 Cisco Layer Two Forwarding (Protocol) "L2F". (A predecessor to L2TP)
|
||||
RFC 2637 Point-to-Point Tunneling Protocol (PPTP). (A predecessor to L2TP)
|
||||
RFC 2661 Layer Two Tunneling Protocol "L2TP"
|
||||
RFC 2809 Implementation of L2TP Compulsory Tunneling via RADIUS
|
||||
RFC 2888 Secure Remote Access with L2TP
|
||||
RFC 3070 Layer Two Tunneling Protocol (L2TP) over Frame Relay
|
||||
RFC 3145 L2TP Disconnect Cause Information
|
||||
RFC 3193 Securing L2TP using IPsec
|
||||
RFC 3301 Layer Two Tunnelling Protocol (L2TP): ATM access network
|
||||
RFC 3308 Layer Two Tunneling Protocol (L2TP) Differentiated Services
|
||||
RFC 3355 Layer Two Tunnelling Protocol (L2TP) Over ATM Adaptation Layer 5 (AAL5)
|
||||
RFC 3371 Layer Two Tunneling Protocol "L2TP" Management Information Base
|
||||
RFC 3437 Layer Two Tunneling Protocol Extensions for PPP Link Control Protocol Negotiation
|
||||
RFC 3438 Layer Two Tunneling Protocol (L2TP) Internet Assigned Numbers: Internet Assigned Numbers Authority (IANA) Considerations Update
|
||||
RFC 3573 Signaling of Modem-On-Hold status in Layer 2 Tunneling Protocol (L2TP)
|
||||
RFC 3817 Layer 2 Tunneling Protocol (L2TP) Active Discovery Relay for PPP over Ethernet (PPPoE)
|
||||
|
||||
RFC's on IPsec in relation to other protocols
|
||||
|
||||
RFC 2207 RSVP Extensions for IPSEC Data Flows
|
||||
RFC 2521 ICMP Security Failures Messages
|
||||
RFC 3104 RSIP Support for End-to-end IPsec
|
||||
RFC 3554 On the Use of Stream Control Transmission Protocol (SCTP) with IPsec
|
||||
RFC 3776 Using IPsec to Protect Mobile IPv6 Signaling Between Mobile Nodes and Home Agents
|
||||
RFC 3884 Use of IPsec Transport Mode for Dynamic Routing
|
||||
|
||||
RFCs that are not really in use or implemented across multiple vendors
|
||||
|
||||
RFC 2522 Photuris: Session-Key Management Protocol
|
||||
RFC 2523 Photuris: Extended Schemes and Attributes
|
||||
RFC 3456 Dynamic Host Configuration Protocol (DHCPv4) Configuration of IPsec Tunnel Mode
|
||||
Binary file not shown.
|
After 
(image error) Size: 13 KiB |
Binary file not shown.
|
After 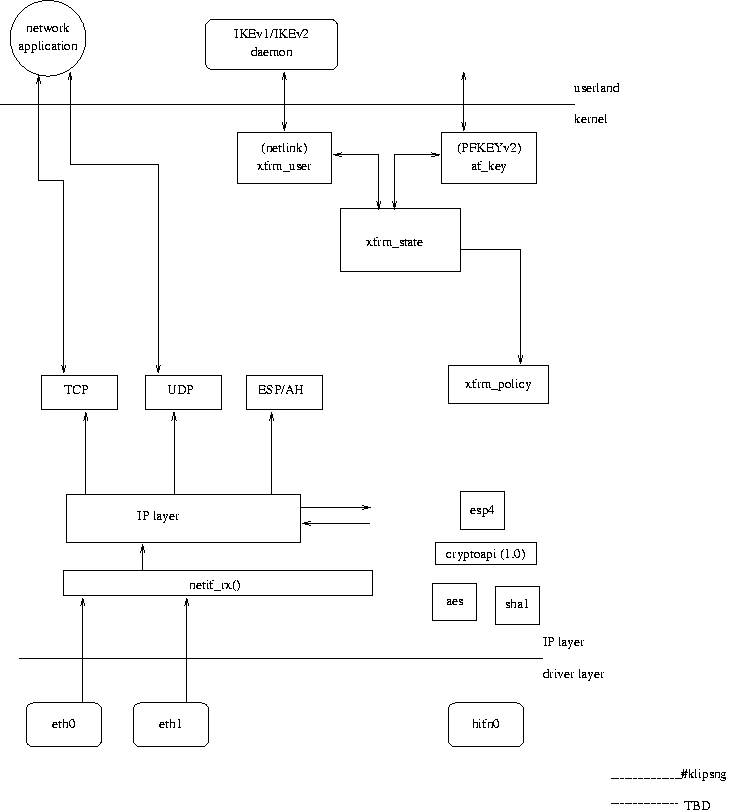
(image error) Size: 12 KiB |
|
|
@ -0,0 +1,45 @@
|
|||
# If you are using a hub-spoke scenario with NETKEY, you run into a
|
||||
# problems with ipsec policies because netkey overrides routes by design.
|
||||
# Example: Your head office is 10.0.0.0/8. Your branch offices
|
||||
# are all ranges taken from there, eg office1 is 10.0.1.0/24, office2 is
|
||||
# 10.0.2.0/24. etc
|
||||
|
||||
Your subnet conn will be something like:
|
||||
|
||||
conn office1-headoffice
|
||||
left=someip
|
||||
leftsubnet=10.0.1.0/24
|
||||
right=someip
|
||||
rightsubnet=10.0.0.0/8
|
||||
[...]
|
||||
|
||||
With NETKEY, since it enforces ipsec policy before routing, your ipsec
|
||||
gateway on 10.0.1.1 will now send packets for 10.0.1.2 over the VPN!
|
||||
In other words, you lose all connectivity with the LAN.
|
||||
|
||||
The work around is to add:
|
||||
|
||||
conn netkey-exclude
|
||||
left=10.0.1.1
|
||||
leftsubnet=10.0.1.0/24
|
||||
right=0.0.0.0
|
||||
rightsubnet=10.0.1.0/24
|
||||
authby=never
|
||||
type=passthrough
|
||||
auto=route
|
||||
|
||||
KLIPS does a longest prefix match first, and does not run into this problem.
|
||||
However, people tend to run netkey on the spokes, since otherwise they
|
||||
will need to update/compile klips for every new kernel release on all the
|
||||
spokes, which is an administrative burden.
|
||||
|
||||
Note that for multiple local LAN ranges, you will need multiple passthrough
|
||||
routes.
|
||||
|
||||
If you have a lan that is local but the libreswan server is not in it, but
|
||||
needs to route to it, then you need a different hack, contributed by
|
||||
Harald Scharf:
|
||||
|
||||
iptables -I PREROUTING -t mangle -j ROUTE -s <mysubnet1/cidr> \
|
||||
-d <myremotesubnet/cidr> -oif <interface to subnet with router>
|
||||
|
||||
|
|
@ -0,0 +1,38 @@
|
|||
# Example as taken from John Denker's IPv6 IPsec page at:
|
||||
# http://www.av8n.com/computer/htm/ipv6-howto.htm#htoc19
|
||||
#
|
||||
# Note that IPv6 only works with the NETKEY stack
|
||||
#
|
||||
# (keys have not been fully written out in the examples)
|
||||
|
||||
config setup
|
||||
protostack=netkey
|
||||
interfaces="%none"
|
||||
|
||||
conn ipv6-host-host
|
||||
auto=add
|
||||
#
|
||||
leftid="@sunset.example.net"
|
||||
left="2002:4a6b:e723:3:205:4eff:fe4b:c8cf"
|
||||
leftrsasigkey="0sAQNM....hIp"
|
||||
leftnexthop="fe80::201:2ff:fe29:564d"
|
||||
#
|
||||
rightid="east.example.net"
|
||||
right="2002:4387:d370::"
|
||||
rightrsasigkey="0sAQP....LMsP"
|
||||
|
||||
conn ipv6-subnet-subnet
|
||||
auto=add
|
||||
#
|
||||
leftid="@sunset.example.net"
|
||||
left="2002:4a6b:e723:3:205:4eff:fe4b:c8cf"
|
||||
leftrsasigkey="0sAQNM....hIp"
|
||||
leftnexthop="fe80::201:2ff:fe29:564d"
|
||||
leftsubnet="2002:4a6b:e723:8003:205:4eff:fe4b:c8cf/128"
|
||||
leftsourceip="2002:4a6b:e723:8003:205:4eff:fe4b:c8cf"
|
||||
#
|
||||
rightid="east.example.net"
|
||||
right="2002:4387:d370::"
|
||||
rightrsasigkey="0sAQP....LMsP"
|
||||
rightsubnet="2002:4387:d370:8000::/128"
|
||||
|
||||
|
|
@ -0,0 +1,58 @@
|
|||
conn l2tp-X.509
|
||||
#
|
||||
# Configuration for one user with any type of IPsec/L2TP client
|
||||
# including the updated Windows 2000/XP (MS KB Q818043), but
|
||||
# excluding the non-updated Windows 2000/XP.
|
||||
#
|
||||
#
|
||||
# Use a certificate. Disable Perfect Forward Secrecy.
|
||||
#
|
||||
authby=rsasig
|
||||
pfs=no
|
||||
auto=add
|
||||
# we cannot rekey for %any, let client rekey
|
||||
rekey=no
|
||||
# Apple iOS doesn't send delete notify so we need dead peer detection
|
||||
# to detect vanishing clients
|
||||
dpddelay=10
|
||||
dpdtimeout=90
|
||||
dpdaction=clear
|
||||
# Set ikelifetime and keylife to same defaults windows has
|
||||
ikelifetime=8h
|
||||
keylife=1h
|
||||
# l2tp-over-ipsec is transport mode
|
||||
# See http://bugs.xelerance.com/view.php?id=466
|
||||
type=transport
|
||||
#
|
||||
left=YourServerIP
|
||||
leftid=%fromcert
|
||||
leftrsasigkey=%cert
|
||||
leftcert=/etc/ipsec.d/certs/YourGatewayCertHere.pem
|
||||
leftprotoport=17/1701
|
||||
#
|
||||
# The remote user.
|
||||
#
|
||||
right=%any
|
||||
rightca=%same
|
||||
rightrsasigkey=%cert
|
||||
# Using the magic port of "%any" means "any one single port". This is
|
||||
# a work around required for Apple OSX clients that use a randomly
|
||||
# high port.
|
||||
rightprotoport=17/%any
|
||||
rightsubnet=vhost:%priv,%no
|
||||
|
||||
# Normally, KLIPS drops all plaintext traffic from IP's it has a crypted
|
||||
# connection with. With L2TP clients behind NAT, that's not really what
|
||||
# you want. The connection below allows both l2tp/ipsec and plaintext
|
||||
# connections from behind the same NAT router.
|
||||
# The l2tpd use a leftprotoport, so they are more specific and will be used
|
||||
# first. Then, packets for the host on different ports and protocols (eg ssh)
|
||||
# will match this passthrough conn.
|
||||
conn passthrough-for-non-l2tp
|
||||
type=passthrough
|
||||
left=YourServerIP
|
||||
leftnexthop=YourGwIP
|
||||
right=0.0.0.0
|
||||
rightsubnet=0.0.0.0/0
|
||||
auto=route
|
||||
|
||||
|
|
@ -0,0 +1,61 @@
|
|||
conn L2TP-PSK-NAT
|
||||
rightsubnet=vhost:%priv
|
||||
also=L2TP-PSK-noNAT
|
||||
|
||||
conn L2TP-PSK-noNAT
|
||||
#
|
||||
# Configuration for one user with any type of IPsec/L2TP client
|
||||
# including the updated Windows 2000/XP (MS KB Q818043), but
|
||||
# excluding the non-updated Windows 2000/XP.
|
||||
#
|
||||
#
|
||||
# Use a Preshared Key. Disable Perfect Forward Secrecy.
|
||||
#
|
||||
# PreSharedSecret needs to be specified in /etc/ipsec.secrets as
|
||||
# YourIPAddress %any: "sharedsecret"
|
||||
authby=secret
|
||||
pfs=no
|
||||
auto=add
|
||||
keyingtries=3
|
||||
# we cannot rekey for %any, let client rekey
|
||||
rekey=no
|
||||
# Apple iOS doesn't send delete notify so we need dead peer detection
|
||||
# to detect vanishing clients
|
||||
dpddelay=10
|
||||
dpdtimeout=90
|
||||
dpdaction=clear
|
||||
# Set ikelifetime and keylife to same defaults windows has
|
||||
ikelifetime=8h
|
||||
keylife=1h
|
||||
# l2tp-over-ipsec is transport mode
|
||||
type=transport
|
||||
#
|
||||
left=YourGatewayIP
|
||||
#
|
||||
# For updated Windows 2000/XP clients,
|
||||
# to support old clients as well, use leftprotoport=17/%any
|
||||
leftprotoport=17/1701
|
||||
#
|
||||
# The remote user.
|
||||
#
|
||||
right=%any
|
||||
# Using the magic port of "%any" means "any one single port". This is
|
||||
# a work around required for Apple OSX clients that use a randomly
|
||||
# high port.
|
||||
rightprotoport=17/%any
|
||||
|
||||
# Normally, KLIPS drops all plaintext traffic from IP's it has a crypted
|
||||
# connection with. With L2TP clients behind NAT, that's not really what
|
||||
# you want. The connection below allows both l2tp/ipsec and plaintext
|
||||
# connections from behind the same NAT router.
|
||||
# The l2tpd use a leftprotoport, so they are more specific and will be used
|
||||
# first. Then, packets for the host on different ports and protocols (eg ssh)
|
||||
# will match this passthrough conn.
|
||||
conn passthrough-for-non-l2tp
|
||||
type=passthrough
|
||||
left=YourServerIP
|
||||
leftnexthop=YourGwIP
|
||||
right=0.0.0.0
|
||||
rightsubnet=0.0.0.0/0
|
||||
auto=route
|
||||
|
||||
|
|
@ -0,0 +1,19 @@
|
|||
conn linux-to-linux
|
||||
#
|
||||
# Simple use raw RSA keys
|
||||
# After starting libreswan, run: ipsec showhostkey --left (or --right)
|
||||
# and fill in the connection similarly to the example below.
|
||||
#
|
||||
left=1.2.3.4
|
||||
# optional
|
||||
# leftsubnet=10.0.1.0/24
|
||||
leftid=@bofh.xelerance.com
|
||||
leftrsasigkey=0sAQPWTXt8DDlEhTZJ91ngNMxTSyuos6JZxXQmtRcwUl6ppUCcuuWvjXrF/qiz6eiL1LMlpGJyG1oVhtFhTaFJl7ZkF/4J1B9LCFzYxvYI97AnLuC0op5pVAZ1SZx29+aRjeMcKC4zbZ6dMMjUdn9H1gqG9rpE0MBEFNSVLEu9U8rtlz14RfxQAQ9ePj64HnGLfgJlDB0VYhKEIcRihy72bvjZ4eoX16S1EY1FgnHyrveZPxRi8sgn6Q19RytEzSmUAlGjvMDhNfenq6WCSYMeqgj0jFSArTNBQmR2QBkUG6NSOXfb+18c6jDPicGmbmWfoRx/PUJo46WiRF4RRmsxnFpbHpklILFzEJ+/k6qHVAekpVfp
|
||||
# The remote user.
|
||||
#
|
||||
right=5.6.7.8
|
||||
rightid=@tla.xelerance.com
|
||||
# optional
|
||||
# rightsubnet=10.0.2.0/24
|
||||
rightrsasigkey=0sAQNxf6caKULJklYZycuo66Ko0U+iHaJUDr0QZHnG4MJ9IRNYi5H6kPxcwKIXkg+OGo+NeUyyWDEc+ox27BFYViAHQNEyBRLZu0kyE681h+cHm7lfCSy0AOEBSCyZF3aGcL8GWxVhtimpJQ4tNxXZg7tLX5sfYw8mZnUBjkHvyccIred/q3cNWbDlq2WU4TL+NBb5FnxXi9Hk/SRV7sMe56fvZuXkcJu4e2C7uocltzzF1b0BZx7yeXwHjzqAWnW/UA54fbSTvzgnrpSC+FMuhWTI1EdxcqGaOFIjGWWGV2nxg/QaPU9i8vpwFwrEEdCJTiqlbYYNudblg4vYthnVNez0/RkfZHfhAaHdbJRSaQzOu88h
|
||||
auto=start
|
||||
|
|
@ -0,0 +1,58 @@
|
|||
config setup
|
||||
# assumes 192.168.1.0/24 is our L2TP range
|
||||
interfaces="%defaultroute"
|
||||
protostack=mast
|
||||
# T-Mobile and Rogers/FIDO now use 25/8 as "private space" too :(
|
||||
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%v4:!192.168.1.0/24
|
||||
|
||||
conn L2TP-PSK-NAT
|
||||
rightsubnet=vhost:%priv
|
||||
also=L2TP-PSK-noNAT
|
||||
|
||||
conn L2TP-PSK-noNAT
|
||||
#
|
||||
# Configuration for one user with any type of IPsec/L2TP client
|
||||
# including the updated Windows 2000/XP (MS KB Q818043), but
|
||||
# excluding the non-updated Windows 2000/XP.
|
||||
#
|
||||
#
|
||||
# Use a Preshared Key. Disable Perfect Forward Secrecy.
|
||||
#
|
||||
# PreSharedSecret needs to be specified in /etc/ipsec.secrets as
|
||||
# YourIPAddress %any: "sharedsecret"
|
||||
authby=secret
|
||||
pfs=no
|
||||
auto=add
|
||||
keyingtries=3
|
||||
# we cannot rekey for %any, let client rekey
|
||||
rekey=no
|
||||
# Apple iOS doesn't send delete notify so we need dead peer detection
|
||||
# to detect vanishing clients
|
||||
dpddelay=10
|
||||
dpdtimeout=90
|
||||
dpdaction=clear
|
||||
# Set ikelifetime and keylife to same defaults windows has
|
||||
ikelifetime=8h
|
||||
keylife=1h
|
||||
# l2tp-over-ipsec is transport mode
|
||||
type=transport
|
||||
#
|
||||
# MAST parameters - requires
|
||||
# ipsec saref = yes in /etc/xl2tpd/xl2tpd.conf
|
||||
sareftrack=yes
|
||||
overlapip=yes
|
||||
#
|
||||
left=YourGatewayIP
|
||||
#
|
||||
# For updated Windows 2000/XP clients,
|
||||
# to support old clients as well, use leftprotoport=17/%any
|
||||
leftprotoport=17/1701
|
||||
#
|
||||
# The remote user.
|
||||
#
|
||||
right=%any
|
||||
# Using the magic port of "%any" means "any one single port". This is
|
||||
# a work around required for Apple OSX clients that use a randomly
|
||||
# high port.
|
||||
rightprotoport=17/%any
|
||||
|
||||
|
|
@ -0,0 +1,69 @@
|
|||
# /etc/ipsec.d/oe-authnull.conf
|
||||
#
|
||||
# Example file for Opportunstic Encryption using Auth NULL
|
||||
# During negotiation, hold traffic. On IKE Auth NULL failure, fail open
|
||||
# Traffic is held until IKE has failed or succeeded
|
||||
# Because it uses Auth NULL, there is no protection against active MITM attacks
|
||||
#
|
||||
# See also oe-upgrade-authnull.conf
|
||||
|
||||
conn clear
|
||||
type=passthrough
|
||||
# temp workaround
|
||||
#authby=never
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%group
|
||||
auto=route
|
||||
|
||||
conn clear-or-private
|
||||
type=tunnel
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%opportunisticgroup
|
||||
negotiationshunt=hold
|
||||
failureshunt=passthrough
|
||||
ikev2=insist
|
||||
# add, not route - because this policy is only for incoming IKE packets
|
||||
auto=add
|
||||
|
||||
conn private-or-clear
|
||||
type=tunnel
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%opportunisticgroup
|
||||
negotiationshunt=hold
|
||||
failureshunt=passthrough
|
||||
ikev2=insist
|
||||
auto=route
|
||||
keyingtries=1
|
||||
retransmit-timeout=2s
|
||||
|
||||
conn private
|
||||
type=tunnel
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%opportunisticgroup
|
||||
negotiationshunt=hold
|
||||
failureshunt=drop
|
||||
ikev2=insist
|
||||
auto=route
|
||||
|
||||
conn block
|
||||
type=reject
|
||||
# temp workaround
|
||||
#authby=never
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%group
|
||||
auto=route
|
||||
|
|
@ -0,0 +1,31 @@
|
|||
|
||||
conn private-or-clear
|
||||
rightauth=rsasig
|
||||
right=%opportunisticgroup
|
||||
rightrsasigkey=%dnsondemand
|
||||
left=%defaultroute
|
||||
leftid=%null
|
||||
leftauth=null
|
||||
leftmodecfgclient=yes
|
||||
leftcat=yes
|
||||
narrowing=yes
|
||||
negotiationshunt=passthrough
|
||||
failureshunt=passthrough
|
||||
type=tunnel
|
||||
ikev2=insist
|
||||
auto=ondemand
|
||||
keyingtries=1
|
||||
retransmit-timeout=2s
|
||||
|
||||
|
||||
conn block
|
||||
type=reject
|
||||
# temp workaround
|
||||
#authby=never
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%group
|
||||
auto=route
|
||||
|
||||
|
|
@ -0,0 +1,22 @@
|
|||
|
||||
# Opportunistic IPsec using DNSSEC and supporting an address
|
||||
# pool for clients behind NAT (Client Address Translation, cat)
|
||||
#
|
||||
conn clear-or-private
|
||||
leftckaid=YourCKAID
|
||||
left=%defaultroute
|
||||
leftaddresspool=100.64.0.1-100.64.255.254
|
||||
leftid=@YOURFQDN
|
||||
leftauth=rsasig
|
||||
leftmodecfgclient=yes
|
||||
leftcat=yes
|
||||
right=%opportunisticgroup
|
||||
rightauth=null
|
||||
rightid=%null
|
||||
#narrowing=yes
|
||||
negotiationshunt=passthrough
|
||||
failureshunt=passthrough
|
||||
ikev2=insist
|
||||
type=tunnel
|
||||
auto=add
|
||||
|
||||
|
|
@ -0,0 +1,9 @@
|
|||
conn let-my-dns-go
|
||||
left=%defaultroute
|
||||
leftnexthop=%defaultroute
|
||||
leftprotoport=17/%any
|
||||
right=0.0.0.0
|
||||
rightsubnet=0.0.0.0/0
|
||||
rightprotoport=17/53
|
||||
type=passthrough
|
||||
auto=route
|
||||
|
|
@ -0,0 +1,31 @@
|
|||
|
||||
Instructions for running Opportunistic IPsec with Letsencrypt
|
||||
|
||||
# Install libreswan 3.19oe2 via rpm or srpm listed here
|
||||
# Install the Letsencrypt related certificates:
|
||||
mkdir letsencrypt
|
||||
cd letsencrypt
|
||||
wget https://letsencrypt.org/certs/lets-encrypt-x4-cross-signed.pem
|
||||
wget https://letsencrypt.org/certs/lets-encrypt-x3-cross-signed.pem
|
||||
wget https://letsencrypt.org/certs/isrgrootx1.pem
|
||||
# based on https://www.identrust.com/certificates/trustid/root-download-x3.html
|
||||
wget https://nohats.ca/LE/identrust-x3.pem
|
||||
#
|
||||
certutil -A -i lets-encrypt-x3-cross-signed.pem -n lets-encrypt-x3 -t CT,, -d sql:/etc/ipsec.d
|
||||
certutil -A -i lets-encrypt-x4-cross-signed.pem -n lets-encrypt-x4 -t CT,, -d sql:/etc/ipsec.d
|
||||
certutil -A -i isrgrootx1.pem -n isrgrootx1 -t CT,, -d sql:/etc/ipsec.d
|
||||
certutil -A -i identrust-x3.pem -n identrust-x3 -t CT,, -d sql:/etc/ipsec.d
|
||||
#
|
||||
# configure libreswan for letsencrypt
|
||||
cd /etc/ipsec.d
|
||||
wget https://nohats.ca/LE/oe-letsencrypt-client.conf
|
||||
echo "193.110.157.131/32" >> /etc/ipsec.d/policies/private-or-clear
|
||||
# if you want to enable it for all remote servers, put 0.0.0.0/0 in private-or-clear
|
||||
# restart libreswan
|
||||
ipsec restart
|
||||
# [wait 2 seconds]
|
||||
ping letsencrypt.libreswan.org
|
||||
ipsec whack --trafficstatus
|
||||
# check if it was encrypting using
|
||||
# tcpdump -n host letsencrypt.libreswan.org
|
||||
|
||||
|
|
@ -0,0 +1,27 @@
|
|||
|
||||
# See https://libreswan.org/wiki/HOWTO:_Opportunistic_IPsec_using_LetsEncrypt
|
||||
#
|
||||
conn private-or-clear
|
||||
rightid=%fromcert
|
||||
rightrsasigkey=%cert
|
||||
rightauth=rsasig
|
||||
right=%opportunisticgroup
|
||||
rightmodecfgclient=yes
|
||||
rightcat=yes
|
||||
# Any CA will do because we only load the LetsEncrypt CA
|
||||
rightca=%any
|
||||
#
|
||||
left=%defaultroute
|
||||
leftid=%null
|
||||
leftauth=null
|
||||
leftmodecfgclient=yes
|
||||
leftcat=yes
|
||||
#
|
||||
narrowing=yes
|
||||
type=tunnel
|
||||
ikev2=insist
|
||||
negotiationshunt=drop
|
||||
failureshunt=passthrough
|
||||
keyingtries=1
|
||||
retransmit-timeout=3s
|
||||
auto=ondemand
|
||||
|
|
@ -0,0 +1,21 @@
|
|||
|
||||
conn clear-or-private
|
||||
leftid=%fromcert
|
||||
leftrsasigkey=%cert
|
||||
# nickname of your letsencrypt certificate imported to NSS
|
||||
leftcert=letsencrypt.libreswan.org
|
||||
leftauth=rsasig
|
||||
left=%defaultroute
|
||||
leftaddresspool=100.64.0.1-100.64.255.254
|
||||
leftmodecfgclient=yes
|
||||
#
|
||||
rightid=%null
|
||||
rightauth=null
|
||||
right=%opportunisticgroup
|
||||
#
|
||||
negotiationshunt=passthrough
|
||||
failureshunt=passthrough
|
||||
type=tunnel
|
||||
ikev2=insist
|
||||
sendca=issuer
|
||||
auto=add
|
||||
|
|
@ -0,0 +1,74 @@
|
|||
# /etc/ipsec.d/oe-upgrade-authnull.conf
|
||||
#
|
||||
# Example file for Opportunstic Encryption using Auth NULL
|
||||
# Traffic should flow in the clear until IKE succeeds. Fail open.
|
||||
# This makes IPsec encryption "nice to have - not required"
|
||||
# Because it uses Auth NULL, there is no protection against active MITM attacks
|
||||
#
|
||||
# See also oe.authnull.conf
|
||||
|
||||
conn clear
|
||||
type=passthrough
|
||||
# temp workaround
|
||||
#authby=never
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%group
|
||||
auto=route
|
||||
|
||||
conn clear-or-private
|
||||
type=tunnel
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%opportunisticgroup
|
||||
negotiationshunt=passthrough
|
||||
failureshunt=passthrough
|
||||
ikev2=insist
|
||||
# add, not route - because this policy is only for incoming IKE packets
|
||||
auto=add
|
||||
|
||||
conn private-or-clear
|
||||
type=tunnel
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%opportunisticgroup
|
||||
negotiationshunt=passthrough
|
||||
failureshunt=passthrough
|
||||
ikev2=insist
|
||||
auto=route
|
||||
keyingtries=1
|
||||
retransmit-timeout=2s
|
||||
# To support being behind NAT
|
||||
leftmodecfgclient=yes
|
||||
leftcat=yes
|
||||
narrowing=yes
|
||||
|
||||
conn private
|
||||
type=tunnel
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%opportunisticgroup
|
||||
# if we fail hard, we might as well hold traffic during IKE too
|
||||
negotiationshunt=hold
|
||||
failureshunt=drop
|
||||
ikev2=insist
|
||||
auto=route
|
||||
|
||||
conn block
|
||||
type=reject
|
||||
# temp workaround
|
||||
#authby=never
|
||||
authby=null
|
||||
leftid=%null
|
||||
rightid=%null
|
||||
left=%defaultroute
|
||||
right=%group
|
||||
auto=route
|
||||
|
|
@ -0,0 +1,53 @@
|
|||
|
||||
# example entries for /etc/sysctl.conf
|
||||
# forwarding is needed for subnet or l2tp connections
|
||||
net.ipv4.ip_forward = 1
|
||||
|
||||
# rp_filter protects against packets "appearing out of nowhere". It is not
|
||||
# always clear to the kernel that a packet appeared as a result of decryption.
|
||||
# One such case is using KLIPS or MAST IPsec stacks, as they receive on one
|
||||
# interface but inject the packet on another interface. Another known case is
|
||||
# "appendix mode" using the XFRM/NETKEY stack. Here, packets are receiving,
|
||||
# decrypted and sent onwards on the same single interface. (these can also cause
|
||||
# bad redirects, see below
|
||||
net.ipv4.conf.default.rp_filter = 0
|
||||
net.ipv4.conf.all.rp_filter = 0
|
||||
|
||||
# when using 1 interface for two networks when using NETKEY, the kernel
|
||||
# kernel thinks it can be clever by sending a redirect (cause it cannot
|
||||
# tell an encrypted packet came in, but a decrypted packet came out),
|
||||
# so it sends a bogus ICMP redirect
|
||||
net.ipv4.conf.all.send_redirects = 0
|
||||
net.ipv4.conf.default.send_redirects = 0
|
||||
net.ipv4.icmp_ignore_bogus_error_responses = 1
|
||||
net.ipv4.conf.default.log_martians = 0
|
||||
net.ipv4.conf.all.log_martians = 0
|
||||
# seems the martian settings are not always enough. If not receiving packets
|
||||
# try running this:
|
||||
# for n in eth0 mast0 ipsec0 ipsec1 all default ; do
|
||||
# sysctl net.ipv4.conf.$n.rp_filter=0;
|
||||
# done
|
||||
#
|
||||
|
||||
# these are non-ipsec specific security policies you should use
|
||||
net.ipv4.conf.default.accept_source_route = 0
|
||||
net.ipv6.conf.default.accept_source_route = 0
|
||||
net.ipv4.conf.all.accept_redirects = 0
|
||||
net.ipv6.conf.all.accept_redirects = 0
|
||||
net.ipv4.conf.default.accept_redirects = 0
|
||||
net.ipv6.conf.default.accept_redirects = 0
|
||||
|
||||
# When using KLIPS in some situations, you will see errors like:
|
||||
# [ 8648.409997] __ratelimit: 168 messages suppressed
|
||||
# [ 8648.410009] Neighbour table overflow.
|
||||
# Especially when on large cable networks, though we've also
|
||||
# seen it when using combinations of xen/bridging/VM's.
|
||||
# If you do, and you are SURE there are no routing loops,
|
||||
# you can try these below:
|
||||
#
|
||||
net.ipv4.neigh.default.gc_thresh1 = 1024
|
||||
net.ipv4.neigh.default.gc_thresh2 = 2048
|
||||
net.ipv4.neigh.default.gc_thresh3 = 4096
|
||||
|
||||
# for enableing core dumps, see
|
||||
# http://fcp.surfsite.org/modules/smartfaq/faq.php?faqid=2746
|
||||
|
|
@ -0,0 +1,31 @@
|
|||
conn xauthserver
|
||||
#
|
||||
left=1.2.3.4
|
||||
leftcert=/etc/ipsec.d/certs/xauthserver.pem
|
||||
leftxauthserver=yes
|
||||
leftmodecfgserver=yes
|
||||
#
|
||||
right=%any
|
||||
rightxauthclient=yes
|
||||
rightmodecfgclient=yes
|
||||
#
|
||||
auto=add
|
||||
rekey=yes
|
||||
modecfgpull=yes
|
||||
modecfgdns1.2.3.4,5.6.7.8
|
||||
|
||||
conn xauthclient
|
||||
#
|
||||
left=1.2.3.4
|
||||
leftxauthserver=yes
|
||||
leftmodecfgserver=yes
|
||||
#
|
||||
right=%defaultroute
|
||||
rightxauthclient=yes
|
||||
rightmodecfgclient=yes
|
||||
#
|
||||
auto=add
|
||||
# you probably can not rekey, it requires xauth password, and libreswan does not
|
||||
# cache it for you. Other clients might cache it and rekey to an libreswan server
|
||||
rekey=no
|
||||
modecfgpull=yes
|
||||
Binary file not shown.
|
After 
(image error) Size: 160 KiB |
|
|
@ -0,0 +1,3 @@
|
|||
mast.4: mast.xml
|
||||
xmlto man mast.xml
|
||||
|
||||
|
|
@ -0,0 +1,187 @@
|
|||
.\"Generated by db2man.xsl. Don't modify this, modify the source.
|
||||
.de Sh \" Subsection
|
||||
.br
|
||||
.if t .Sp
|
||||
.ne 5
|
||||
.PP
|
||||
\fB\\$1\fR
|
||||
.PP
|
||||
..
|
||||
.de Sp \" Vertical space (when we can't use .PP)
|
||||
.if t .sp .5v
|
||||
.if n .sp
|
||||
..
|
||||
.de Ip \" List item
|
||||
.br
|
||||
.ie \\n(.$>=3 .ne \\$3
|
||||
.el .ne 3
|
||||
.IP "\\$1" \\$2
|
||||
..
|
||||
.TH "MAST" 4 "" "" ""
|
||||
.SH NAME
|
||||
mast \- pseudo-driver for attaching tunnelling protocols
|
||||
.SH "SYNOPSIS"
|
||||
.ad l
|
||||
.hy 0
|
||||
|
||||
|
||||
#include <net/mast.h>
|
||||
|
||||
.sp
|
||||
.HP 27
|
||||
struct\ device\ *\fBmast_init\fR\ (int\ \fIfamily\fR, struct\ mast_callbacks\ *\fIcallbacks\fR, unsigned\ int\ \fIflags\fR, char\ *\fIunit\fR, unsigned\ int\ \fImax_flowref\fR, void\ *\fIcontext\fR);
|
||||
.HP 18
|
||||
int\ \fBpacket_encap\fR\ (struct\ device\ *\fImast\fR, void\ *\fIcontext\fR, struct\ skb\ *\fIskb\fR, int\ \fIflowref\fR);
|
||||
.HP 18
|
||||
int\ \fBlink_inquire\fR\ (struct\ device\ *\fImast\fR, void\ *\fIcontext\fR);
|
||||
.HP 19
|
||||
int\ \fBmast_linkstat\fR\ (struct\ device\ *\fImast\fR, int\ \fIflowref\fR, int\ \fIstatus\fR);
|
||||
.HP 23
|
||||
int\ \fBmast_setreference\fR\ (struct\ device\ *\fImast\fR, int\ \fIdefault_flowref\fR);
|
||||
.HP 23
|
||||
int\ \fBmast_setneighbour\fR\ (struct\ device\ *\fImast\fR, struct\ sockaddr\ *\fIsource\fR, struct\ sockaddr\ *\fIdestination\fR, int\ \fIflowref\fR);
|
||||
.ad
|
||||
.hy
|
||||
|
||||
.SH "DESCRIPTION"
|
||||
|
||||
.PP
|
||||
The mast network interface is a pseudo device that allows tunnelling protocols to be attached to the base of the device, and routing protocols and daemons to the top. The metaphor is that of a blimp attached to a mooring post or mast.
|
||||
|
||||
.PP
|
||||
mast stands for Mooring And Status Tunnel.
|
||||
|
||||
.PP
|
||||
The network interfaces are named anything that can fit in 16 printable characters. We suggest \fBmast0\fR, \fBmast1\fR and so on, as many as desired, but they could also be named \fBmast\-rome\fR or even \fBvpn\-rome\fR or other more descriptive names. The names should be unique in the namespace of the network devices.
|
||||
|
||||
.PP
|
||||
They are created with the "ip tncfg" command.
|
||||
|
||||
.PP
|
||||
The mast device provides a way to anchor routing daemon to virtual topologies. It provides a consistent abstraction to various kinds of tunnelling technology: IP\-encap (protocol 4), IPv6 (protocol 41), GRE (protocol 47), ESP (protocol 50), AH (protocol 51), IPIP (protocol 94) and ENCAP (protocol 98).
|
||||
|
||||
.PP
|
||||
There are three ways that a mast can be used. They correspond to how additional information (i.e. policy) is attached to the packets that are directed toward the device. mast devices are bi\-directional devices, but the flow of the packets that emerge do so in a uniform manner.
|
||||
|
||||
.PP
|
||||
The first way is called the PPP method. A mast is considered to be portal to which packets that need a predefined kind of encapsulation may be sent. The mast acts as a point to point device \- a virtual leased line \- sending all packets into the an underlying tunnel mechanism, having attached a default security policy to each packet. (As is described under "SECURITY POLICY", the nfmark is used). A mast device used in this way should be indistinguishable from a SLIP interface \- it has no layer two protocol. The layer two link status of the mast device may reflect the state of the dead peer detection status for the remote end point, if this feature has been enabled.
|
||||
|
||||
.PP
|
||||
The second way that a mast device may be used is as an entry into a non\-broadcast, multiple access encapsulation media. The is the NFMARK method. The choice of a particular tunnel is indicated by setting bits in the control structure (the skb). This is described under "SECURITY POLICY".
|
||||
|
||||
.PP
|
||||
The third way that a mast device may be used is with a virtual link layer. This is the NMBA method. This is the This is a variation of the previous method \- the device is still a non\-broadcast, multiple access device, except that the mast device supports a layer two similar to ARP. The layer two information that the network stack attaches to each packet will be used to determine which tunnel will be used. The mast device will keep the neighbour cache updated with liveness info. If the tunnel to a given neighbour is known to be down (such as, because of a lack of a key, or expiration of such), then the neighbour cache entry will be removed.
|
||||
|
||||
.PP
|
||||
Packets that are sent upwards (in the direction of decapsulation) from the mast device will be marked by the tunnel on which the packet was received. The choice of which mast device to emerge from is also defined by the tunnel decapsulation mechanism. Typically, a unique device will be created per major policy category. This is done to simplify the firewall rules.
|
||||
|
||||
.PP
|
||||
The PPP method is most appropriate for use on the client side of a road warrior configuration, or when there is a sufficiently small number of VPN tunnels that it is practical (or desirable) for each tunnel to have its own device associated with it. The simplification of firewall rules for output is the primary benefit of this mode.
|
||||
|
||||
.PP
|
||||
The NFMARK mechanism is used by more traditional VPN topologies, and by Opportunistic Encryption. These two categories of use mandate a different output device per major policy. Both would use specific setting of policy bits (skb\->nfmark) for selection of outgoing policy.
|
||||
|
||||
.PP
|
||||
The NMBA mechanism, where an ARP\-like layer two is maintained, is most appropriate for layered systems like the xbone, where there may be too many tunnels for it to be practical to create a device per tunnel. At the same time, the reachability information that the layer\-two tables provide can be used by routing systems to determine the optimal path.
|
||||
|
||||
.PP
|
||||
The mast device permits kernel code to create them with:
|
||||
|
||||
.nf
|
||||
|
||||
struct device *mast;
|
||||
|
||||
mast = mast_init(family, callbacks, flags,
|
||||
unit, max_flowref, context)
|
||||
|
||||
.fi
|
||||
|
||||
|
||||
.PP
|
||||
A new mast device is create per address family. This is not strictly necessary, but may simplify policy checks as well.
|
||||
|
||||
.TP
|
||||
\fIfamily\fR
|
||||
is AF_INET or AF_INET6.
|
||||
|
||||
.TP
|
||||
\fIflags\fR
|
||||
is one of
|
||||
|
||||
MAST_PPP:the device will operate only as a point to point device ignoring any bits set in the nfmark field.
|
||||
|
||||
MAST_NFMARK: the device will examine the nfmark field, extracting bits from this field to form an SArefence, which is passed to the encapsulation routine.
|
||||
|
||||
MAST_NBMA: the device will examine virtual layer two information pointed to by the skb\->mac.raw field.
|
||||
|
||||
.TP
|
||||
\fIunit\fR
|
||||
is an integer X, the unit number, and results in the creation of the appropriate mastX device. If this unit number is in use, then an error will result, and NULL will be returned.
|
||||
|
||||
.TP
|
||||
\fImax_flowref\fR
|
||||
is the theoretical highest flowref that can be assigned. It is recorded for sanity checking. It may also be used for scaling of virtual layer\-2 structures.
|
||||
|
||||
.TP
|
||||
\fIcallbacks\fR
|
||||
The callback is a structure containing function pointers for \fBpacket_encap\fR and \fBlink_inquire\fR.
|
||||
|
||||
.TP
|
||||
\fIcontext\fR
|
||||
The context contains mast sub\-type\-specific information.
|
||||
|
||||
.TP
|
||||
\fImast\fR
|
||||
The mast is a struct device * previously created by \fBmast_init\fR.
|
||||
|
||||
.TP
|
||||
\fIskb\fR
|
||||
The skb is a struct sk_buff * passed down for processing.
|
||||
|
||||
.TP
|
||||
\fIflowref\fR
|
||||
The flowref is a reference to a policy to be used for packet processing.
|
||||
|
||||
.TP
|
||||
\fIstatus\fR
|
||||
The status is a flag indicating the link state.
|
||||
|
||||
.TP
|
||||
\fIdefault_flowref\fR
|
||||
The default_flowref is a reference to a default policy to be used for packet processing.
|
||||
|
||||
.TP
|
||||
\fIsource\fR and \fIdestination\fR
|
||||
The source and destination are IPv4 or IPv6 addresses.
|
||||
|
||||
.PP
|
||||
The \fBpacket_encap\fR callback is called by the mast device when a packet has been forwarded into the mast device in some fashion. The function will be called with the \fIcontext\fR that was provided in the \fBmast_init\fR call.
|
||||
|
||||
.PP
|
||||
The packet to be processed will be passed in the \fIskb\fR parameter. The flow reference will have been extracted and passed in the \fIflowref\fR parameter.
|
||||
|
||||
.PP
|
||||
The link_inquire() function is a request from the mast device to have its link status updated by the tunnel apparatus. Link status can be updated with the \fBmast_linkstat\fR function.
|
||||
|
||||
.PP
|
||||
In the link_inquire call(), status is up==1/down==0. Some mast devices may maintain per\-flowref link status (in the pseudo\-ARP case), in which case the flowref should be provided. A flowref of \-1 updates the global link status.
|
||||
|
||||
.PP
|
||||
A mast device may have its default flow reference set via the \fBmast_setflowref\fR function.
|
||||
|
||||
.PP
|
||||
A mast device examines packets that it receives, looks at the appropriate parts of the nfmark and turns that into the reference #. If these bits are zero, then the default flow reference is used. If the default flow reference is not set, then the packet is dropped as a transmit error.
|
||||
|
||||
.PP
|
||||
The \fBmast_setneighbour\fR function will be filled out at a later time.
|
||||
|
||||
.SH "SECURITY POLICY"
|
||||
|
||||
.PP
|
||||
When the mast device is configured to be in \fBMAST_NFMARK\fR mode, it will examine the skb\->nfmark field of each incoming packet. The upper 24 bits of the nfmark will be extracted. If bit 31 is set, then the nfmark will be considered to be have been initialized. Bits 8 through 30 are then shifted to the right, resulting in a 23 bit number. This is considered the flowref.
|
||||
|
||||
.PP
|
||||
If the bit is not set, then the packet will have the default flow reference applied to it.
|
||||
|
||||
.SH AUTHOR
|
||||
Michael Richardson <mcr@sandelman.ottawa.on.ca>.
|
||||
|
|
@ -0,0 +1,444 @@
|
|||
<?xml version='1.0'?> <!-- -*- docbook -*- -->
|
||||
<!DOCTYPE article PUBLIC "-//OASIS//DTD DocBook XML V4.2//EN"
|
||||
"http://www.oasis-open.org/docbook/xml/4.2/docbookx.dtd">
|
||||
|
||||
<article>
|
||||
<articleinfo>
|
||||
<title>mast</title>
|
||||
|
||||
<author>
|
||||
<firstname>Michael</firstname>
|
||||
<surname>Richardson</surname>
|
||||
<affiliation>
|
||||
<address><email>mcr@sandelman.ottawa.on.ca</email></address>
|
||||
</affiliation>
|
||||
</author>
|
||||
|
||||
<copyright>
|
||||
<year>2003</year>
|
||||
<holder>Michael Richardson</holder>
|
||||
</copyright>
|
||||
</articleinfo>
|
||||
|
||||
<section>
|
||||
<title>Reference</title>
|
||||
|
||||
<refentry id="mast">
|
||||
|
||||
<refmeta>
|
||||
<refentrytitle>mast</refentrytitle>
|
||||
<manvolnum>4</manvolnum>
|
||||
</refmeta>
|
||||
|
||||
<refnamediv>
|
||||
<refname>mast</refname>
|
||||
<refpurpose>pseudo-driver for attaching tunnelling protocols</refpurpose>
|
||||
</refnamediv>
|
||||
|
||||
<refsynopsisdiv>
|
||||
|
||||
<funcsynopsis>
|
||||
<funcsynopsisinfo>
|
||||
#include <net/mast.h>
|
||||
</funcsynopsisinfo>
|
||||
<funcprototype>
|
||||
<funcdef>struct device *<function>mast_init</function></funcdef>
|
||||
<paramdef>int <parameter>family</parameter></paramdef>
|
||||
<paramdef>struct mast_callbacks *<parameter>callbacks</parameter></paramdef>
|
||||
<paramdef>unsigned int <parameter>flags</parameter></paramdef>
|
||||
<paramdef>char *<parameter>unit</parameter></paramdef>
|
||||
<paramdef>unsigned int <parameter>max_flowref</parameter></paramdef>
|
||||
<paramdef>void *<parameter>context</parameter></paramdef>
|
||||
</funcprototype>
|
||||
|
||||
<funcprototype>
|
||||
<funcdef>int <function>packet_encap</function></funcdef>
|
||||
<paramdef>struct device *<parameter>mast</parameter></paramdef>
|
||||
<paramdef>void *<parameter>context</parameter></paramdef>
|
||||
<paramdef>struct skb *<parameter>skb</parameter></paramdef>
|
||||
<paramdef>int <parameter>flowref</parameter></paramdef>
|
||||
</funcprototype>
|
||||
|
||||
<funcprototype>
|
||||
<funcdef>int <function>link_inquire</function></funcdef>
|
||||
<paramdef>struct device *<parameter>mast</parameter></paramdef>
|
||||
<paramdef>void *<parameter>context</parameter></paramdef>
|
||||
</funcprototype>
|
||||
|
||||
<funcprototype>
|
||||
<funcdef>int <function>mast_linkstat</function></funcdef>
|
||||
<paramdef>struct device *<parameter>mast</parameter></paramdef>
|
||||
<paramdef>int <parameter>flowref</parameter></paramdef>
|
||||
<paramdef>int <parameter>status</parameter></paramdef>
|
||||
</funcprototype>
|
||||
|
||||
<funcprototype>
|
||||
<funcdef>int <function>mast_setreference</function></funcdef>
|
||||
<paramdef>struct device *<parameter>mast</parameter></paramdef>
|
||||
<paramdef>int <parameter>default_flowref</parameter></paramdef>
|
||||
</funcprototype>
|
||||
|
||||
<funcprototype>
|
||||
<funcdef>int <function>mast_setneighbour</function></funcdef>
|
||||
<paramdef>struct device *<parameter>mast</parameter></paramdef>
|
||||
<paramdef>struct sockaddr *<parameter>source</parameter></paramdef>
|
||||
<paramdef>struct sockaddr *<parameter>destination</parameter></paramdef>
|
||||
<paramdef>int <parameter>flowref</parameter></paramdef>
|
||||
</funcprototype>
|
||||
|
||||
</funcsynopsis>
|
||||
|
||||
</refsynopsisdiv>
|
||||
|
||||
<refsect1><title>Description</title>
|
||||
<para>
|
||||
The
|
||||
<application>mast</application>
|
||||
network interface is a pseudo device that allows tunnelling protocols to
|
||||
be attached to the base of the device, and routing protocols and daemons to
|
||||
the top. The metaphor is that of a blimp attached to a mooring post or mast.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
<application>mast</application> stands for Mooring And Status Tunnel.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The network interfaces are named anything that can fit in 16 printable characters. We suggest
|
||||
<function>mast0</function>, <function>mast1</function>
|
||||
and so on, as many as desired, but they could also be named
|
||||
<function>mast-rome</function> or even <function>vpn-rome</function>
|
||||
or other more descriptive names. The names should be unique in the namespace
|
||||
of the network devices.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
They are created with the "ip tunnel" command. (XXX? are they. Maybe, maybe not.)
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The <application>mast</application> device provides a way to anchor routing daemon to virtual
|
||||
topologies. It provides a consistent abstraction to various kinds of tunnelling
|
||||
technology: IP-encap (protocol 4), IPv6 (protocol 41), GRE (protocol 47),
|
||||
ESP (protocol 50), AH (protocol 51), IPIP (protocol 94) and ENCAP (protocol 98).
|
||||
</para>
|
||||
|
||||
<para>
|
||||
There are three ways that a <application>mast</application> can be used. They
|
||||
correspond to how additional
|
||||
information (i.e. policy) is attached to the packets that are directed toward
|
||||
the device. <application>mast</application> devices are bi-directional
|
||||
devices, but the flow of the packets that emerge do so in a uniform manner.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The first way is called the PPP method.
|
||||
A <application>mast</application> is considered to
|
||||
be portal to which
|
||||
packets that need a predefined kind of encapsulation may be sent.
|
||||
The <application>mast</application>
|
||||
acts as a point to point device - a virtual leased line - sending all packets
|
||||
into the an underlying tunnel mechanism, having attached a default security
|
||||
policy to each packet. (As is described under "SECURITY POLICY", the
|
||||
nfmark is used).
|
||||
A <application>mast</application> device used in this way should be
|
||||
indistinguishable from a SLIP
|
||||
interface - it has no layer two protocol. The layer two link status of
|
||||
the <application>mast</application>
|
||||
device may reflect the state of the dead peer detection status for the remote
|
||||
end point, if this feature has been enabled.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The second way that a <application>mast</application> device may be used is
|
||||
as an entry into a
|
||||
non-broadcast, multiple access encapsulation media. The is the NFMARK
|
||||
method. The choice of a
|
||||
particular tunnel is indicated by setting bits in the control structure (the
|
||||
skb). This is described under "SECURITY POLICY".
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The third way that a <application>mast</application> device may be used is
|
||||
with a virtual link
|
||||
layer. This is the NMBA method.
|
||||
This is the This is a variation of the previous method - the device is still a
|
||||
non-broadcast, multiple access device, except that the <application>mast</application> device
|
||||
supports a layer two similar to ARP. The layer two information that the network
|
||||
stack attaches to each packet will be used to determine which tunnel will be
|
||||
used. The <application>mast</application> device will keep the neighbour cache updated with liveness
|
||||
info. If the tunnel to a given neighbour is known to be down (such as,
|
||||
because of a lack of a key, or expiration of such), then the neighbour cache
|
||||
entry will be removed.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
Packets that are sent upwards (in the direction of decapsulation) from
|
||||
the <application>mast</application> device will be marked by the tunnel on
|
||||
which the packet was received.
|
||||
The choice of which <application>mast</application> device to emerge from
|
||||
is also defined by the tunnel decapsulation mechanism. Typically, a unique
|
||||
device will be created per major policy category. This is done to simplify the
|
||||
firewall rules.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The PPP method is most appropriate for use on the client side of a road
|
||||
warrior configuration, or when there is a sufficiently small number of VPN tunnels
|
||||
that it is practical (or desirable) for each tunnel to have its own device
|
||||
associated with it. The simplification of firewall rules for output is the
|
||||
primary benefit of this mode.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The NFMARK mechanism is used by more traditional VPN topologies, and by
|
||||
Opportunistic Encryption. These two categories of use mandate a different
|
||||
output device per major policy. Both would use specific setting of policy
|
||||
bits (skb->nfmark) for selection of outgoing policy.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The NMBA mechanism, where an ARP-like layer two is maintained, is most
|
||||
appropriate for layered systems like the xbone, where there may be too many
|
||||
tunnels for it to be practical to create a device per tunnel. At the same
|
||||
time, the reachability information that the layer-two tables provide can be
|
||||
used by routing systems to determine the optimal path.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The <application>mast</application> device permits kernel code
|
||||
to create them with:
|
||||
<programlisting>
|
||||
struct device *mast;
|
||||
|
||||
mast = mast_init(family, callbacks, flags,
|
||||
unit, max_flowref, context)
|
||||
</programlisting>
|
||||
</para>
|
||||
|
||||
<para>
|
||||
A new <application>mast</application> device is create per address family.
|
||||
This is not strictly necessary, but may simplify policy checks as well.
|
||||
</para>
|
||||
|
||||
<variablelist>
|
||||
<varlistentry><term><parameter>family</parameter></term>
|
||||
<listitem>
|
||||
<para>
|
||||
is AF_INET or AF_INET6.
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<varlistentry><term><parameter>flags</parameter></term>
|
||||
<listitem>
|
||||
<para>
|
||||
is one of
|
||||
</para>
|
||||
|
||||
<para>
|
||||
MAST_PPP:the device will operate only as a point to point device
|
||||
ignoring any bits set in the
|
||||
<structname>nfmark</structname> field.
|
||||
</para>
|
||||
|
||||
<para>MAST_NFMARK:
|
||||
the device will examine the <structname>nfmark</structname> field,
|
||||
extracting bits from this field to form an SArefence,
|
||||
which is passed to the encapsulation routine.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
MAST_NBMA:
|
||||
the device will examine virtual layer two information
|
||||
pointed to by the <structname>skb->mac.raw</structname> field.
|
||||
</para>
|
||||
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<varlistentry><term><parameter>unit</parameter></term>
|
||||
<listitem>
|
||||
<para>is an integer X, the unit number, and results in the creation
|
||||
of the appropriate mastX device. If this unit number is
|
||||
in use, then an error will result, and NULL will be returned.
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<varlistentry><term><parameter>max_flowref</parameter></term>
|
||||
<listitem>
|
||||
<para>is the theoretical highest flowref that can be assigned. It
|
||||
is recorded for sanity checking. It may also be used for scaling
|
||||
of virtual layer-2 structures.
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<varlistentry><term><parameter>callbacks</parameter></term>
|
||||
<listitem>
|
||||
<para>
|
||||
The callback is a structure containing function pointers for
|
||||
<function>packet_encap</function> and <function>link_inquire</function>.
|
||||
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<varlistentry><term><parameter>context</parameter></term>
|
||||
<listitem>
|
||||
<para>
|
||||
The context contains mast sub-type-specific information.
|
||||
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<programlisting>
|
||||
int packet_encap (struct device *mast, void *context,
|
||||
struct skb *skb, int flowref);
|
||||
</programlisting>
|
||||
|
||||
<varlistentry><term><parameter>mast</parameter></term>
|
||||
<listitem>
|
||||
<para>
|
||||
The mast is a struct device * previously
|
||||
created by <function>mast_init</function>.
|
||||
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<varlistentry><term><parameter>skb</parameter></term>
|
||||
<listitem>
|
||||
<para>
|
||||
The skb is a struct sk_buff * passed down for processing.
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<varlistentry><term><parameter>flowref</parameter></term>
|
||||
<listitem>
|
||||
<para>
|
||||
The flowref is a reference to a policy to be used for packet
|
||||
processing.
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<programlisting>
|
||||
int mast_linkstat (struct device *mast, int flowref,
|
||||
int status);
|
||||
</programlisting>
|
||||
|
||||
<varlistentry><term><parameter>status</parameter></term>
|
||||
<listitem>
|
||||
<para>
|
||||
The status is a flag indicating the link state.
|
||||
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<varlistentry><term><parameter>default_flowref</parameter></term>
|
||||
<listitem>
|
||||
<para>
|
||||
The default_flowref is a reference to a default policy to be used for packet processing.
|
||||
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
<programlisting>
|
||||
int mast_setneighbour (struct device *mast,
|
||||
struct sockaddr *source,
|
||||
struct sockaddr *destination,
|
||||
int flowref);
|
||||
</programlisting>
|
||||
|
||||
<varlistentry><term><parameter>source</parameter> and <parameter>destination</parameter></term>
|
||||
<listitem>
|
||||
<para>
|
||||
The source and destination are IPv4 or IPv6 addresses.
|
||||
</para>
|
||||
</listitem>
|
||||
</varlistentry>
|
||||
|
||||
</variablelist>
|
||||
|
||||
<para>
|
||||
The <function>packet_encap</function> callback is called by the mast
|
||||
device when a packet has been forwarded into the <application>mast</application> device in some
|
||||
fashion. The function will be called with the
|
||||
<parameter>context</parameter> that was provided in the
|
||||
<function>mast_init</function> call.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The packet to be processed will be passed in the
|
||||
<parameter>skb</parameter> parameter. The flow reference
|
||||
will have been extracted and passed in the
|
||||
<parameter>flowref</parameter> parameter.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The link_inquire() function is a request from
|
||||
the <application>mast</application> device to have its
|
||||
link status updated by the tunnel apparatus. Link status can be
|
||||
updated with the <function>mast_linkstat</function> function.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
In the link_inquire call(), status is up==1/down==0.
|
||||
Some <application>mast</application> devices may maintain per-flowref link
|
||||
status (in the pseudo-ARP case), in which case the flowref should be
|
||||
provided. A flowref of -1 updates the global link status.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
A <application>mast</application> device may have its default
|
||||
flow reference set via the
|
||||
<function>mast_setflowref</function> function.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
A <application>mast</application> device examines packets that
|
||||
it receives, looks at the appropriate
|
||||
parts of the nfmark and turns that into the reference #. If these bits are
|
||||
zero, then the default flow reference is used. If the default
|
||||
flow reference is not
|
||||
set, then the packet is dropped as a transmit error.
|
||||
</para>
|
||||
|
||||
<para>
|
||||
The <function>mast_setneighbour</function> function will be filled out at a later time.
|
||||
</para>
|
||||
|
||||
</refsect1>
|
||||
|
||||
<refsect1><title>SECURITY POLICY</title>
|
||||
<para>
|
||||
When the <application>mast</application> device is configured to be
|
||||
in <constant>MAST_NFMARK</constant> mode, it will examine the
|
||||
<structname>skb->nfmark</structname> field of each incoming
|
||||
packet. The upper 24 bits of the <structname>nfmark</structname> will
|
||||
be extracted. If bit 31 is set, then the
|
||||
<structname>nfmark</structname> will be considered to be have been
|
||||
initialized. Bits 8 through 30 are then shifted to the right, resulting
|
||||
in a 23 bit number. This is considered the flowref.
|
||||
</para>
|
||||
|
||||
<para>If the bit is not set, then the packet will have the default flow reference
|
||||
applied to it.
|
||||
</para>
|
||||
|
||||
</refsect1>
|
||||
</refentry>
|
||||
</section>
|
||||
</article>
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
Binary file not shown.
|
After 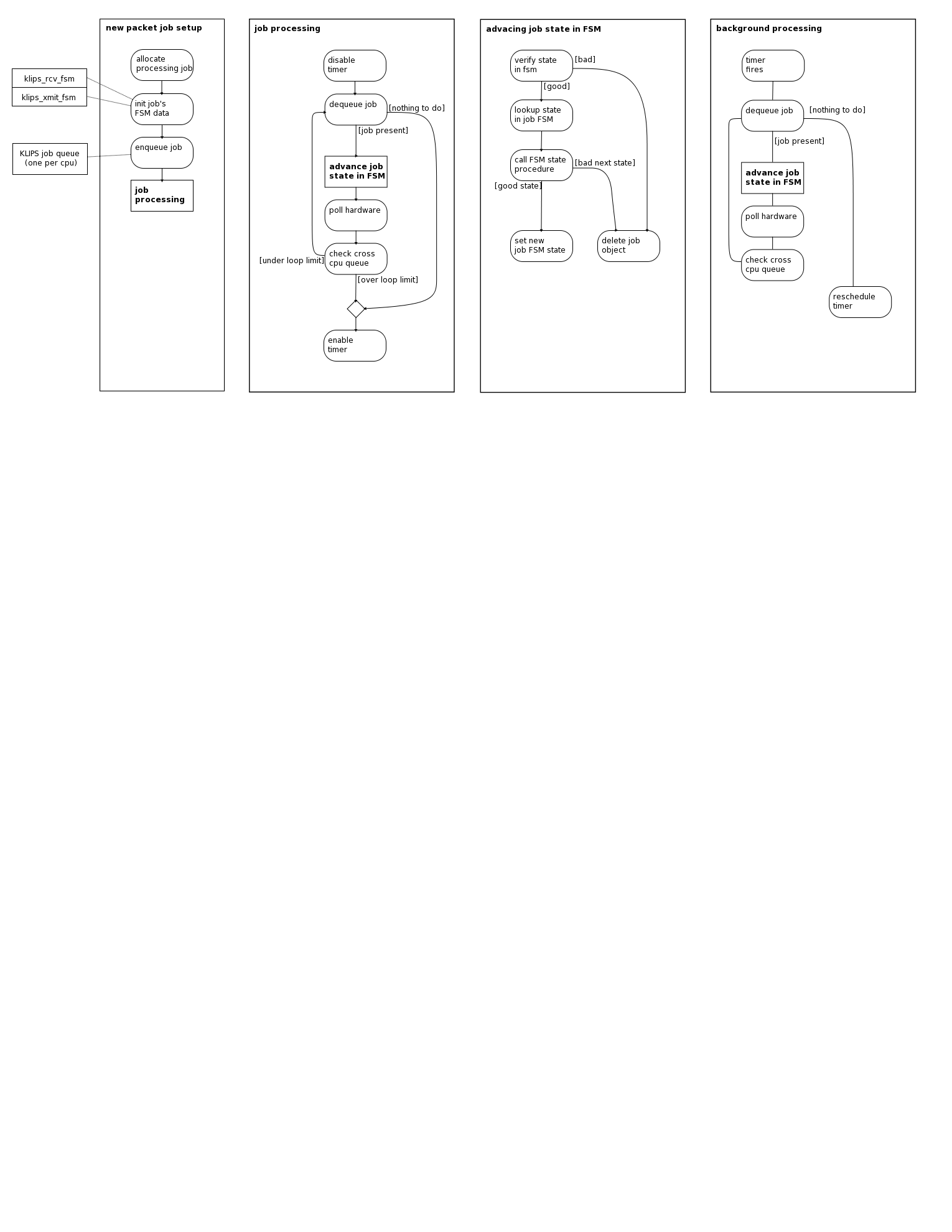
(image error) Size: 64 KiB |
File diff suppressed because it is too large
Load Diff
|
After (image error) Size: 41 KiB |
Binary file not shown.
|
After 
(image error) Size: 84 KiB |
File diff suppressed because it is too large
Load Diff
|
After (image error) Size: 75 KiB |
|
|
@ -0,0 +1,11 @@
|
|||
IP 20
|
||||
UDP 14
|
||||
ESP spi 4
|
||||
iv 8
|
||||
auth 12
|
||||
pad 8
|
||||
total 36
|
||||
UDP 14
|
||||
L2TP 8
|
||||
PPP 2
|
||||
|
||||
|
|
@ -0,0 +1,137 @@
|
|||
#########################################################################
|
||||
# Scenario: To setup ipsec with certs in tunnel mode using NSS
|
||||
#########################################################################
|
||||
|
||||
GW Mahine 1: w1.x1.y1.z1
|
||||
GW Mahine 2: w2.x2.y2.z2
|
||||
|
||||
w1.x1.y1.z1 <---> w2.x2.y2.z2
|
||||
|
||||
Note: In this example setup, both machines are using NSS. If you want to use NSS only at one machine, say machine 1, you can use the following procedure only at machine 1, and you can use traditional ipsec setup at machine 2.
|
||||
|
||||
1. Create a new (if not already) nss db on both machines as follows:
|
||||
|
||||
certutil -N -d sql:<path-to-ipsec.d dir>/ipsec.d (please note "sql:" in the beginning of all the path).
|
||||
|
||||
2. Creating CA certs at both machines:
|
||||
|
||||
On machine 1:
|
||||
certutil -S -k rsa -n cacert1 -s "CN=cacert1" -v 12 -d . -t "C,C,C" -x -d
|
||||
sql:<path-to-ipsec.d dir>/ipsec.d
|
||||
|
||||
As we want to use the same certificate "cacert1" at machine 2, it needs to be
|
||||
exported first. To export the cacert1, do the following at machine 1:
|
||||
|
||||
pk12util -o cacert1.p12 -n cacert1 -d sql:/etc/ipsec.d
|
||||
|
||||
Copy the file "cacert1.p12" to the machine2 in "/etc/ipsec.d" directory.
|
||||
|
||||
On machine 2:
|
||||
Import the "cacert1" as follows:
|
||||
|
||||
cd /etc/ipsec.d
|
||||
pk12util -i cacert1.p12 -d sql:/etc/ipsec.d
|
||||
certutil -M -n cacert1 -t "C, C, C" -d sql:/etc/ipsec.d
|
||||
|
||||
Now machine 2 also has the CA certificates "cacert1" in its NSS database.
|
||||
|
||||
3. Creating user certs at both machines:
|
||||
|
||||
On machine 1:
|
||||
certutil -S -k rsa -c cacert1 -n usercert1 -s "CN=usercert1" -v 12 -t "u,u,u"
|
||||
-d sql:/etc/ipsec.d
|
||||
(Note this cert is signed by "cacert1")
|
||||
|
||||
On machine 2:
|
||||
certutil -S -k rsa -c cacert1 -n usercert2 -s "CN=usercert2" -v 12 -t "u,u,u"
|
||||
-d sql:/etc/ipsec.d
|
||||
(Note this cert is signed by "cacert1" too)
|
||||
|
||||
|
||||
4. Preparing ipsec.conf at both machines
|
||||
|
||||
ipsec.conf at machine 1:
|
||||
|
||||
|
||||
conn pluto-1-2
|
||||
left=w1.x1.y1.z1
|
||||
leftid="CN=usercert1"
|
||||
leftsourceip=w1.x1.y1.z1
|
||||
leftrsasigkey=%cert
|
||||
leftcert=usercert1
|
||||
leftnexthop=w2.x2.y2.z2
|
||||
right=w2.x2.y2.z2
|
||||
rightid="CN=usercert2"
|
||||
rightsourceip=w2.x2.y2.z2
|
||||
rightrsasigkey=%cert
|
||||
rightnexthop=w1.x1.y1.z1
|
||||
rekey=no
|
||||
esp="aes-sha1"
|
||||
ike="aes-sha1"
|
||||
auto=add
|
||||
|
||||
|
||||
ipsec.conf at machine 2:
|
||||
|
||||
|
||||
conn pluto-1-2
|
||||
left=w2.x2.y2.z2
|
||||
leftid="CN=usercert2"
|
||||
leftsourceip=w2.x2.y2.z2
|
||||
leftrsasigkey=%cert
|
||||
leftcert=usercert2
|
||||
leftnexthop=w1.x1.y1.z1
|
||||
right=w1.x1.y1.z1
|
||||
rightid="CN=usercert1"
|
||||
rightsourceip=w1.x1.y1.z1
|
||||
rightrsasigkey=%cert
|
||||
rightnexthop=w2.x2.y2.z2
|
||||
rekey=no
|
||||
esp="aes-sha1"
|
||||
ike="aes-sha1"
|
||||
auto=add
|
||||
|
||||
5. Preparing ipsec.secrets at both machines
|
||||
|
||||
ipsec.secrets at machine 1:
|
||||
|
||||
: RSA usercert1
|
||||
|
||||
|
||||
ipsec.secrets at machine 1:
|
||||
|
||||
: RSA usercert2
|
||||
|
||||
|
||||
#########################################################################
|
||||
# Import certificates
|
||||
#########################################################################
|
||||
This example show how to import certificates in nss.
|
||||
Is useful if you want to migrate from openswan to libreswan.
|
||||
|
||||
Import a CA:
|
||||
certutil -A -i <ca_cert_file> -n "<ca_cert_alias>" -t "C,C,C" -d /etc/ipsec.d/
|
||||
example: certutil -A -i /etc/ipsec.d/cacerts/CaCert.pem -n "CaCert" -t "C,C,C" -d /etc/ipsec.d/
|
||||
|
||||
|
||||
|
||||
Import a cert:
|
||||
certutil -A -i <cert_file> -n "<cert_alias>" -t "C,C,C" -d /etc/ipsec.d/
|
||||
example: certutil -A -i /etc/ipsec.d/certs/serverCert.pemm -n "serverCert" -t "C,C,C" -d /etc/ipsec.d/
|
||||
|
||||
|
||||
|
||||
Import a client cert:
|
||||
certutil -A -i <cert_file> -n "<cert_alias>" -t "u,u,u" -d /etc/ipsec.d/
|
||||
example: certutil -A -i /etc/ipsec.d/certs/userCert.pem -n "userCert" -t "u,u,u" -d /etc/ipsec.d/
|
||||
Convert key:
|
||||
openssl pkcs12 -export -in /etc/ipsec.d/certs/userCert.pem -inkey /etc/ipsec.d/private/userKey.pem -name "userCert" -out /etc/ipsec.d/private/userKey.p12
|
||||
Import Key:
|
||||
pk12util -i /etc/ipsec.d/private/userKey.p12 -d /etc/ipsec.d
|
||||
In your secret file you can use:
|
||||
: RSA "userCert"
|
||||
|
||||
|
||||
|
||||
Show a list of the current certificates and trust attributes in a certificate database:
|
||||
certutil -L -d /etc/ipsec.d/
|
||||
File diff suppressed because it is too large
Load Diff
File diff suppressed because it is too large
Load Diff
|
|
@ -0,0 +1,329 @@
|
|||
Routing and Erouting in Pluto
|
||||
=============================
|
||||
|
||||
This is meant as internal documentation for Pluto. As such, it
|
||||
presumes some understanding of Pluto's code.
|
||||
|
||||
It also describes KLIPS 1 erouting, including details not otherwise
|
||||
documented. KLIPS 1 documentation would be better included in KLIPS.
|
||||
|
||||
Routing and erouting are complicated enough that the Pluto code needs
|
||||
a guide. This document is meant to be that guide.
|
||||
|
||||
|
||||
Mechanisms available to Pluto
|
||||
-----------------------------
|
||||
|
||||
All outbound packets that are to be processed by KLIPS 1 must be
|
||||
routed to an ipsecN network interface. Pluto only uses normal routing
|
||||
(as opposed to "Advanced Routing"), so the selection of packets is
|
||||
made solely on the basis of the destination address. (Since the
|
||||
actual routing commands are in the updown script, they could be
|
||||
changed by the administrator, but Pluto needs to understand what is
|
||||
going on, and it currently assumes normal routing is used.)
|
||||
|
||||
When an outbound packet hits an ipsecN interface, KLIPS figures out
|
||||
how to process it by finding an eroute that applies to the source and
|
||||
destination addresses. Eroutes are global: they are not specific to a
|
||||
particular ipsecN interface (routing needs to get the packets to any
|
||||
ipsecN interface; erouting takes it from there, ignoring issues of
|
||||
source IP address and nexthop (because nobody knows!)). If multiple
|
||||
eroutes apply to the packet, among the ones with the most specific
|
||||
source subnet, the one with the most specific destination subset is
|
||||
chosen (RGB thinks). If no eroute is discovered, KLIPS acts as if it
|
||||
was covered by a DROP eroute (this is the default behaviour; it can be
|
||||
changed). At most one eroute can exist for a particular pair of
|
||||
client subnets.
|
||||
|
||||
There are fundamentally two kinds of eroutes: "shunt" eroutes and ones
|
||||
that specify that a packet is to be processed by a group of IPSEC SAs.
|
||||
Shunt eroutes specify what is to be done with the packet. Remember
|
||||
that these only apply to outbound packets.
|
||||
|
||||
- TRAP: notify Pluto of the packet (presumably to attempt to negotiate
|
||||
an appropriate group of IPSEC SAs). At the same time, KLIPS
|
||||
installs a HOLD shunt (see below) for the specific source and
|
||||
destination addresses from the packet and retains the packet
|
||||
for later reprocessing (KLIPS does not yet implement retention).
|
||||
Beware: if the TRAP's subnets both contained a single IP address
|
||||
then installing the HOLD would actually delete the TRAP.
|
||||
|
||||
- PASS: let the packet through in the clear
|
||||
|
||||
- DROP: discard the packet
|
||||
|
||||
- REJECT: discard the packet and notify the sender
|
||||
|
||||
- HOLD: (automatically created by KLIPS when a TRAP fires) block
|
||||
the packet, but retain it. If there is already a retained
|
||||
packet, drop the old one and retain the new. When the HOLD
|
||||
shunt is deleted or replaced, the retained packet is reinjected --
|
||||
there might now be a tunnel. Note that KLIPS doesn't yet
|
||||
implement the retention part, so HOLD is really like a DROP.
|
||||
|
||||
One consequence of there being only one eroute for a pair of clients
|
||||
is that KLIPS will only use one SA group for output for this pair,
|
||||
even though there could be several SA groups that are authorised and
|
||||
live. Pluto chooses to make this the youngest such group.
|
||||
|
||||
|
||||
|
||||
KLIPS lets through in the clear outbound UDP/500 packets that would
|
||||
otherwise be processed if they originate on this host and meet certain
|
||||
other conditions. The actual test is
|
||||
source == me
|
||||
&& (no_eroute || dest == eroute.dest || isanyaddr(eroute.dest))
|
||||
&& port == UDP/500
|
||||
The idea is that IKE packets between us and a peer should not be
|
||||
sent through an IPSEC tunnel negotiated between us. Furthermore,
|
||||
our shunt eroutes should not apply to our IKE packets (shunt eroutes
|
||||
will generally have an eroute.dest of 0.0.0.0 or its IPv6 equivalent).
|
||||
|
||||
Inbound behaviour is controlled in a quite different way. KLIPS
|
||||
processes only those inbound packets of ESP or AH protocol, with a
|
||||
destination address for this machine's ipsecN interfaces. The
|
||||
processing is as dictated by the SAs involved. Unfortunately, the
|
||||
decapsulated packet's source and destination address are not checked
|
||||
(part of "inbound policy checking").
|
||||
|
||||
To prevent clear packets being accepted, firewall rules must be put in
|
||||
place. This has nothing to do with KLIPS, but is nonetheless in
|
||||
important part of security. It isn't clear what firewalling makes
|
||||
sense when Opportunism is allowed.
|
||||
|
||||
|
||||
For routing and firewalling, Pluto invokes the updown script. Pluto
|
||||
installs eroutes via extended PF_KEY messages.
|
||||
|
||||
|
||||
Current Pluto Behaviour
|
||||
-----------------------
|
||||
|
||||
Data Structures:
|
||||
|
||||
Routes and most eroutes are associated with connections (struct
|
||||
connection, a potential connection description). The enum routing_t
|
||||
field "routing" in struct connection records the state of routing and
|
||||
erouting for that connection. The values are:
|
||||
RT_UNROUTED, /* unrouted */
|
||||
RT_UNROUTED_HOLD, /* unrouted, but HOLD shunt installed */
|
||||
RT_ROUTED_PROSPECTIVE, /* routed, and TRAP shunt installed */
|
||||
RT_ROUTED_HOLD, /* routed, and HOLD shunt installed */
|
||||
RT_ROUTED_FAILURE, /* routed, and failure-context shunt installed */
|
||||
RT_ROUTED_TUNNEL /* routed, and erouted to an IPSEC SA group */
|
||||
Notice that the routing and erouting are not independent: erouting
|
||||
(except for HOLD) implies that the connection is routed.
|
||||
|
||||
Several struct connections may have the same destination subnet. If
|
||||
they agree on what the route should be, they can share it -- any of
|
||||
them may have routing >= RT_ROUTED_PROSPECTIVE. If they disagree,
|
||||
they cannot simultaneously be routed.
|
||||
|
||||
invariant: for all struct connections c, d:
|
||||
(c.that.client == d.that.client
|
||||
&& c.routing >= RT_ROUTED_PROSPECTIVE
|
||||
&& d.routing >= RT_ROUTED_PROSPECTIVE)
|
||||
=> c.interface == d.interface && c.this.nexthop == d.this.nexthop
|
||||
|
||||
There are two kinds of eroutes: shunt eroutes and ones for an IPSEC SA
|
||||
Group. Most eroutes are associated with and are represeented in a
|
||||
connection. The exception is that some HOLD and PASS shunts do not
|
||||
correspond to connections; those are represented in the bare_shunt
|
||||
table.
|
||||
|
||||
An eroute for an IPSEC SA Group is associated with the state object
|
||||
for that Group. The existence of such an eroute is also represented
|
||||
by the "so_serial_t eroute_owner" field in the struct connection. The
|
||||
value is the serial number of the state object for the Group. The
|
||||
special value SOS_NOBODY means that there is no owner associated with
|
||||
this connection for the eroute and hence no normal eroute. At most
|
||||
one eroute owner may exist for a particular (source subnet,
|
||||
destination subnet) pair. A Pluto-managed eroute cannot be associated
|
||||
with an RT_UNROUTED connection.
|
||||
|
||||
invariant: for all struct connection c:
|
||||
c.routing == RT_EROUTED_TUNNEL || c.eroute_owner == SOS_NOBODY
|
||||
|
||||
invariant: for all struct connections c, d:
|
||||
c.this.client == d.this.client && c.that.client == d.that.client
|
||||
&& &c != &d
|
||||
=> c.routing == RT_UNROUTED || d.routing == RT_UNROUTED
|
||||
|
||||
If no normal eroute is set for a particular (source subnet,
|
||||
destination subnet) pair for which a connection is routed, then a
|
||||
shunt eroute would have been installed. This specifies what should
|
||||
happen to packets snared by the route.
|
||||
|
||||
When Pluto is notified by KLIPS of a packet that has been TRAPped,
|
||||
there is no connection with which to associate the HOLD. It is
|
||||
temporarily held in the "bare_shunt table". If Opportunism is
|
||||
attempted but DNS doesn't provide Security Gateway information, Pluto
|
||||
will replace the HOLD with a PASS shunt. Since this PASS isn't
|
||||
associated with a connection, it too will reside in the bare_shunt
|
||||
table. If the HOLD can be associated with a connection, it will be
|
||||
removed from the bare_shunt table and represented in the connection.
|
||||
|
||||
There are two contexts for which shunt eroutes are installed by Pluto
|
||||
for a particular connection. The first context is with the prospect
|
||||
of dealing with packets before any negotiation has been attempted. I
|
||||
call this context "prospective". Currently is a TRAP shunt, used to
|
||||
catch packets for initiate opportunistic negotiation. In the future,
|
||||
it might also be used to implement preordained PASS, DROP, or REJECT
|
||||
rules.
|
||||
|
||||
The second context is after a failed negotiation. I call this context
|
||||
"failure". At this point a different kind of shunt eroute is
|
||||
appropriate. Depending on policy, it could be PASS, DROP, or REJECT,
|
||||
but it is unlikely to be TRAP. The shunt eroute should have a
|
||||
lifetime (this isn't yet implemented). When the lifetime expires, the
|
||||
failure shunt eroute should be replaced by the prospective shunt
|
||||
eroute.
|
||||
|
||||
The kind and duration of a failure shunt eroute should perhaps depend
|
||||
on the nature of the failure, at least as imperfectly detected by
|
||||
Pluto. We haven't looked at this. In particular, the mapping from
|
||||
observations to robust respose isn't obvious.
|
||||
|
||||
The shunt eroute policies should be a function of the potential
|
||||
connection. The failure shunt eroute can be specified for a
|
||||
particular connection with the flags --pass and --drop in a connection
|
||||
definition. There are four combinations, and each has a distinct
|
||||
meaning. The failure shunt eroute is incompletely implemented and
|
||||
cannot be represented in /etc/ipsec.conf.
|
||||
|
||||
There is as yet no control over the prospective shunt eroute: it is
|
||||
always TRAP as far as Pluto is concerned. This is probably
|
||||
reasonable: any other fate suggests that no negotiation will be done,
|
||||
and so a connection definition is inappropriate. These should be
|
||||
implemented as manual conns. There remains the issue of whether Pluto
|
||||
should be aware of them -- currently it is not.
|
||||
|
||||
|
||||
Routines:
|
||||
|
||||
[in kernel.c]
|
||||
|
||||
bool do_command(struct connection *c, const char *verb)
|
||||
Run the updown script to perform such tasks as installing a route
|
||||
and adjust the firewall.
|
||||
|
||||
bool could_route(struct connection *c)
|
||||
Check to see whether we could route and eroute the connection.
|
||||
<- shunt_eroute_connection (to check if --route can be performed)
|
||||
<- install_inbound_ipsec_sa (to see if it will be possible
|
||||
to (later) install route and eroute the corresponding outbound SA)
|
||||
<- install_ipsec_sa (to see if the outbound SA can be routed and erouted)
|
||||
|
||||
bool trap_connection(struct connection *c)
|
||||
Install a TRAP shunt eroute for this connection. This implements
|
||||
"whack --route", the way an admin can specify that packets for a
|
||||
connection should be caught without first bringing it up.
|
||||
|
||||
void unroute_connection(struct connection *c)
|
||||
Delete any eroute for a connection and unroute it if route isn't shared.
|
||||
<- release_connection
|
||||
<- whack_handle (for "whack --unroute)
|
||||
|
||||
bool eroute_connection(struct connection *c
|
||||
, ipsec_spi_t spi, unsigned int proto, unsigned int satype
|
||||
, unsigned int op, const char *opname UNUSED)
|
||||
Issue PF_KEY commands to KLIPS to add, replace, or delete an eroute.
|
||||
The verb is specified by op and described (for logging) by opname.
|
||||
<- assign_hold
|
||||
<- sag_eroute
|
||||
<- shunt_eroute
|
||||
|
||||
bool assign_hold(struct connection *c
|
||||
, const ip_address *src, const ip_address *dst)
|
||||
Take a HOLD from the bare_shunt table and assign it to a connection.
|
||||
If the HOLD is broadened (i.e. the connection's source or destination
|
||||
subnets contain more than one IP address), this will involve replacing
|
||||
the HOLD with a different one.
|
||||
|
||||
bool sag_eroute(struct state *st, unsigned op, const char *opname)
|
||||
SA Group eroute manipulation. The SA Group concerned is
|
||||
identified with a state object.
|
||||
<- route_and_eroute several times
|
||||
|
||||
bool shunt_eroute(struct connection *c, unsigned int op, const char *opname)
|
||||
shunt eroute manipulation. Shunt eroutes are associated with
|
||||
connections.
|
||||
<- unroute_connection
|
||||
<- route_and_eroute
|
||||
<- delete_ipsec_sa
|
||||
|
||||
bool route_and_eroute(struct connection *c, struct state *st)
|
||||
Install a route and then a prospective shunt eroute or an SA group
|
||||
eroute. The code assumes that could_route had previously
|
||||
given the go-ahead. Any SA group to be erouted must already
|
||||
exist.
|
||||
<- shunt_eroute_connection
|
||||
<- install_ipsec_sa
|
||||
|
||||
void scan_proc_shunts(void)
|
||||
Every SHUNT_SCAN_INTERVAL scan /proc/net/ipsec_eroute.
|
||||
Delete any PASS eroute in the bare_shunt table that hasn't been used
|
||||
within the last SHUNT_PATIENCE seconds.
|
||||
For any HOLD for which Pluto hasn't received an ACQUIRE (possibly
|
||||
lost due to congestion), act as if an ACQUIRE were received.
|
||||
|
||||
[in connection.c]
|
||||
|
||||
struct connection *route_owner(struct connection *c, struct connection **erop)
|
||||
Find the connection to connection c's peer's client with the
|
||||
largest value of .routing. All other things being equal,
|
||||
preference is given to c. Return NULL if no connection is routed
|
||||
at all. If erop is non-null, sets it to a connection sharing both
|
||||
our client subnet and peer's client subnet with the largest value
|
||||
of .routing.
|
||||
The return value is used to find other connections sharing
|
||||
a route. The value of *erop is used to find other connections
|
||||
sharing an eroute.
|
||||
<- could_route (to find any conflicting routes or eroutes)
|
||||
<- unroute_connection (to find out if our route is still in use
|
||||
after this connection is finished with it)
|
||||
<- install_inbound_ipsec_sa (to find other IPSEC SAs for the
|
||||
same peer clients; when we find them WE KILL THEM; a
|
||||
kludge to deal with road warriors reconnecting)
|
||||
<- route_and_eroute (to find all the connections from which the
|
||||
route or eroute is being stolen)
|
||||
|
||||
Uses:
|
||||
|
||||
- setting up route & shunt eroute to TRAP packets for opportunism
|
||||
(whack --route). Perhaps also manually designating DROP, REJECT, or
|
||||
PASS for certain packets.
|
||||
|
||||
whack_handle() responds to --route; calls route_connection()
|
||||
|
||||
|
||||
- removing same (whack --unroute)
|
||||
|
||||
whack_handle() responds to --unroute; calls unroute_connection()
|
||||
|
||||
- installing route & normal eroute for a newly negotiated group of
|
||||
outbound IPSEC SAs
|
||||
|
||||
+ perhaps an (additional) route is not needed: if the negotiation
|
||||
was initiated by a TRAPped outgoing packet, then there must
|
||||
already have been a route that got the packet to ipsecN. Mind
|
||||
you, it could have been the wrong N!
|
||||
|
||||
install_ipsec_sa()
|
||||
|
||||
- updating a normal eroute when a new group of IPSEC SAs replaces
|
||||
an old one due to rekeying.
|
||||
|
||||
install_ipsec_sa()
|
||||
|
||||
- replacing an old eroute when a negotiation fails. But this is
|
||||
tricky. If this was a rekeying, we should just leave the old
|
||||
normal eroute be -- it might still work. Otherwise, this was
|
||||
an initial negotiation: we should replace the shunt eroute
|
||||
with one appropriate for the failure context.
|
||||
|
||||
- when a group of IPSEC SAs dies or is killed, and it had the eroute,
|
||||
its normal eroute should be replaced by a shunt eroute. If there
|
||||
was an attempt to replace the group, the replacement is in the
|
||||
failure context; otherwise the replacement is in the prospective
|
||||
context.
|
||||
|
|
@ -0,0 +1,141 @@
|
|||
#FIG 3.2
|
||||
Landscape
|
||||
Center
|
||||
Metric
|
||||
A4
|
||||
107.00
|
||||
Single
|
||||
-2
|
||||
1200 2
|
||||
6 2430 5355 3420 6120
|
||||
2 2 0 2 0 7 50 0 -1 0.000 0 0 -1 0 0 5
|
||||
2475 5400 3375 5400 3375 6075 2475 6075 2475 5400
|
||||
4 1 0 50 0 18 14 0.0000 4 165 735 2925 5850 JAPAN\001
|
||||
-6
|
||||
6 2430 3780 3645 4545
|
||||
2 4 0 2 0 7 50 0 -1 0.000 0 0 7 0 0 5
|
||||
3600 4500 3600 3825 2475 3825 2475 4500 3600 4500
|
||||
4 1 0 50 0 18 14 0.0000 4 150 705 3015 4275 sunset\001
|
||||
-6
|
||||
6 4230 4500 5220 5265
|
||||
2 2 0 2 0 7 50 0 -1 0.000 0 0 -1 0 0 5
|
||||
4275 4545 5175 4545 5175 5220 4275 5220 4275 4545
|
||||
4 1 0 50 0 18 14 0.0000 4 165 615 4725 4995 WEST\001
|
||||
-6
|
||||
6 9855 4500 10845 5265
|
||||
2 2 0 2 0 7 50 0 -1 0.000 0 0 -1 0 0 5
|
||||
9900 4545 10800 4545 10800 5220 9900 5220 9900 4545
|
||||
4 1 0 50 0 18 14 0.0000 4 165 555 10350 4995 EAST\001
|
||||
-6
|
||||
6 11700 3915 12915 4680
|
||||
2 4 0 2 0 7 50 0 -1 0.000 0 0 7 0 0 5
|
||||
12870 4635 12870 3960 11745 3960 11745 4635 12870 4635
|
||||
4 1 0 50 0 18 14 0.0000 4 165 780 12285 4410 sunrise\001
|
||||
-6
|
||||
6 6930 5355 8145 6120
|
||||
2 4 0 2 0 7 50 0 -1 0.000 0 0 7 0 0 5
|
||||
8100 6075 8100 5400 6975 5400 6975 6075 8100 6075
|
||||
4 1 0 50 0 18 14 0.0000 4 165 315 7515 5850 nic\001
|
||||
-6
|
||||
6 7110 1530 8325 2295
|
||||
2 4 0 2 0 7 50 0 -1 0.000 0 0 7 0 0 5
|
||||
8280 2250 8280 1575 7155 1575 7155 2250 8280 2250
|
||||
4 1 0 50 0 18 14 0.0000 4 210 450 7695 2025 pole\001
|
||||
-6
|
||||
6 7110 8505 8325 9270
|
||||
2 4 0 2 0 7 50 0 -1 0.000 0 0 7 0 0 5
|
||||
8280 9225 8280 8550 7155 8550 7155 9225 8280 9225
|
||||
4 1 0 50 0 18 14 0.0000 4 210 465 7695 9000 park\001
|
||||
-6
|
||||
6 10395 270 11025 815
|
||||
2 3 0 1 0 7 50 0 -1 0.000 0 0 0 0 0 7
|
||||
11004 543 10857 288 10563 288 10416 543 10563 797 10857 797
|
||||
11004 543
|
||||
4 1 0 50 0 18 7 0.0000 4 75 210 10710 584 beet\001
|
||||
-6
|
||||
6 10440 900 11025 1352
|
||||
2 2 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 5
|
||||
10467 927 10998 927 10998 1325 10467 1325 10467 927
|
||||
4 1 0 50 0 18 8 0.0000 4 90 435 10732 1192 JAPAN\001
|
||||
-6
|
||||
6 10440 1485 11083 1890
|
||||
2 4 0 1 0 7 50 0 -1 0.000 0 0 4 0 0 5
|
||||
11059 1866 11059 1509 10464 1509 10464 1866 11059 1866
|
||||
4 1 0 50 0 18 7 0.0000 4 75 330 10750 1747 sunset\001
|
||||
-6
|
||||
6 4950 5715 6795 7110
|
||||
2 3 0 2 0 7 50 0 -1 0.000 0 0 0 0 0 7
|
||||
6255 6525 5940 5979 5310 5979 4995 6525 5310 7071 5940 7071
|
||||
6255 6525
|
||||
4 0 0 50 0 18 14 0.0000 4 150 1140 5625 5895 192.1.2.129\001
|
||||
4 1 0 50 0 18 14 0.0000 4 165 450 5625 6615 beet\001
|
||||
-6
|
||||
6 9045 5715 10890 7110
|
||||
2 3 0 2 0 7 50 0 -1 0.000 0 0 0 0 0 7
|
||||
10350 6525 10035 5979 9405 5979 9090 6525 9405 7071 10035 7071
|
||||
10350 6525
|
||||
4 0 0 50 0 18 14 0.0000 4 150 1140 9720 5895 192.1.2.130\001
|
||||
4 1 0 50 0 18 14 0.0000 4 150 630 9720 6615 carrot\001
|
||||
-6
|
||||
6 7200 6750 8865 7875
|
||||
2 2 0 2 0 7 50 0 -1 0.000 0 0 -1 0 0 5
|
||||
7245 7020 8145 7020 8145 7695 7245 7695 7245 7020
|
||||
4 0 0 50 0 18 14 0.0000 4 150 1140 7695 7875 192.0.4.254\001
|
||||
4 0 0 50 0 18 14 0.0000 4 150 1020 7695 6930 192.1.4.44\001
|
||||
4 1 0 50 0 18 14 0.0000 4 165 765 7695 7470 SOUTH\001
|
||||
-6
|
||||
6 7200 2925 8865 4050
|
||||
2 2 0 2 0 7 50 0 -1 0.000 0 0 -1 0 0 5
|
||||
7245 3150 8145 3150 8145 3825 7245 3825 7245 3150
|
||||
4 0 0 50 0 18 14 0.0000 4 150 1020 7695 4050 192.1.3.33\001
|
||||
4 0 0 50 0 18 14 0.0000 4 150 1140 7695 3105 192.0.3.254\001
|
||||
4 1 0 50 0 18 14 0.0000 4 165 780 7695 3600 NORTH\001
|
||||
-6
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
7650 6975 7650 6075
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
3825 3375 3825 6300
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
3375 5625 3825 5625
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
11250 3375 11250 6300
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
7650 8550 7650 7695
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
10800 4860 11250 4860
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
3600 4185 3825 4185
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
7200 5355 7200 4905
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
5175 4905 9900 4905
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
3825 4860 4275 4860
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
11745 4185 11250 4185
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
7650 3825 7650 5400
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
7650 2250 7650 3150
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
9675 5985 9675 4905
|
||||
2 1 0 1 0 7 50 0 -1 0.000 0 0 -1 0 0 2
|
||||
5625 5940 5625 4905
|
||||
4 0 0 50 0 18 14 0.0000 4 150 900 3870 4275 192.0.1.1\001
|
||||
4 0 0 50 0 18 14 0.0000 4 150 900 3870 5715 192.0.1.2\001
|
||||
4 2 0 50 0 18 14 0.0000 4 150 1140 3735 4950 192.0.1.254\001
|
||||
4 0 0 50 0 18 14 0.0000 4 150 1140 11385 4950 192.0.2.254\001
|
||||
4 2 0 50 0 18 14 0.0000 4 150 900 11115 4275 192.0.2.1\001
|
||||
4 2 0 50 0 18 14 0.0000 4 150 1140 7200 5310 192.1.2.254\001
|
||||
4 2 0 50 0 18 14 0.0000 4 150 1020 9855 4860 192.1.2.23\001
|
||||
4 0 0 50 0 18 14 0.0000 4 150 1020 5310 4860 192.1.2.45\001
|
||||
4 0 0 50 0 18 14 0.0000 4 150 900 7695 2475 192.0.3.1\001
|
||||
4 0 0 50 0 18 14 0.0000 4 150 1140 7695 6300 192.1.4.254\001
|
||||
4 0 0 50 0 18 14 0.0000 4 150 1140 7695 5355 192.1.3.254\001
|
||||
4 0 0 50 0 18 14 0.0000 4 150 900 7695 8505 192.0.4.1\001
|
||||
4 0 0 50 0 18 14 0.0000 4 165 1440 11160 675 DNS SERVER\001
|
||||
4 0 0 50 0 18 14 0.0000 4 165 1245 11160 1170 FREESWAN\001
|
||||
4 0 0 50 0 18 14 0.0000 4 165 1350 11250 1800 PLAIN NODE\001
|
||||
4 0 0 50 0 18 14 0.0000 4 210 3300 4275 675 FreeSWAN testing network map\001
|
||||
4 2 0 50 0 18 8 0.0000 4 120 3045 13230 9315 $Id: testnet.fig,v 1.6 2002/11/12 04:11:52 mcr Exp $\001
|
||||
4 2 0 50 0 18 8 0.0000 4 120 1935 13230 9045 freeswan/testing/doc/testnet.fig\001
|
||||
Binary file not shown.
|
After 
(image error) Size: 12 KiB |
|
|
@ -0,0 +1,115 @@
|
|||
The Libreswan IKE daemon has been ported to work on CYGWIN32.
|
||||
|
||||
It presently has no kernel component, so it is useful only to those who want
|
||||
to do some kind of testing using IKE using a Windows 2000/XP platform.
|
||||
|
||||
It assumed that a CYGWIN32 compiler environment exists.
|
||||
|
||||
The code cross compiles, and has passed approximately 90% of our test
|
||||
cases as of this time.
|
||||
|
||||
The major change is that the IKE daemon ("pluto") normally discovers
|
||||
it's list of interfaces and local IP addresses automatically. That code
|
||||
does not port well, so for the moment, we require manual configuration
|
||||
in ipsec.conf. See the "ipsec.win2k.conf" file in the
|
||||
programs/_confread/ipsec.win2k.conf in the source tree.
|
||||
|
||||
You may need to do:
|
||||
mount -f -u -b "C:/cygwin/local" "/usr/local"
|
||||
|
||||
to mark the /usr/local area as executable for cygwin.
|
||||
|
||||
You need to install GNU AWK, GNU SED, to run.
|
||||
|
||||
You will need a program, "logger" installed into /bin:
|
||||
|
||||
bash-3.00$ cat /bin/logger
|
||||
#!/bin/sh
|
||||
|
||||
while [ $# -gt 0 ]
|
||||
do
|
||||
opt=$1; shift;
|
||||
case $opt in
|
||||
-s) ;;
|
||||
-p) shift;;
|
||||
-t) shift;;
|
||||
esac
|
||||
done
|
||||
|
||||
if [ $# -gt 0 ]
|
||||
then
|
||||
echo "$@"
|
||||
else
|
||||
cat -
|
||||
fi
|
||||
exit 0
|
||||
|
||||
bash-3.00$ chmod +x /bin/logger
|
||||
|
||||
To start up libreswan, you can do:
|
||||
|
||||
bash-3.00% ipsec setup start
|
||||
|
||||
note that "ipsec setup stop" does not quite function as yet. The "ps"
|
||||
program does not quite behave.
|
||||
|
||||
To BUILD
|
||||
========
|
||||
|
||||
Extract the tar.gz file in some place that is convenient.
|
||||
|
||||
Type "make programs"
|
||||
Type "make install"
|
||||
|
||||
You will need appropriate tools installed on cygwin:
|
||||
|
||||
Package Version Status
|
||||
bash 3.0-11 OK
|
||||
binutils 20050610-1 OK
|
||||
bison 20030307-1 OK
|
||||
bzip2 1.0.3-1 OK
|
||||
crypt 1.1-1 OK
|
||||
findutils 20041227-1 OK
|
||||
flex 2.5.4a-3 OK
|
||||
gawk 3.1.5-1 OK
|
||||
gcc 3.4.4-1 OK
|
||||
gcc-core 3.4.4-1 OK
|
||||
gcc-g++ 3.4.4-1 OK
|
||||
gdb 20041228-3 OK
|
||||
gmp 4.1.4-2 OK
|
||||
grep 2.5.1a-2 OK
|
||||
groff 1.18.1-2 OK
|
||||
gzip 1.3.5-1 OK
|
||||
make 3.80-1 OK
|
||||
man 1.5p-1 OK
|
||||
minires 1.00-1 OK
|
||||
minires-devel 1.00-1 OK
|
||||
sed 4.1.4-1 OK
|
||||
sharutils 4.3.80-1 OK
|
||||
swig 1.3.24-1 OK
|
||||
tar 1.13.25-7 OK
|
||||
tcltk 20030901-1 OK
|
||||
zip 2.3-6 OK
|
||||
zlib 1.2.2-2 OK
|
||||
|
||||
|
||||
TESTING
|
||||
=======
|
||||
|
||||
To run the tests:
|
||||
0) add the following IP aliases:
|
||||
128.95.7.1
|
||||
128.95.7.2
|
||||
128.95.7.3
|
||||
128.95.7.4
|
||||
|
||||
(On Linux we added 127... but Windows won't let us do that)
|
||||
You will only to do this once.
|
||||
|
||||
1) start up a cygwin bash shell
|
||||
set MYBOX to source tree
|
||||
cd /0g/sandboxes/win2k
|
||||
MYBOX=`pwd` export MYBOX
|
||||
|
||||
2) sh $MYBOX/testing/pluto/pluto-unit-01/pluto_unit_tests.sh
|
||||
|
||||
|
|
@ -0,0 +1,112 @@
|
|||
WHAT I DID.
|
||||
|
||||
{In the course of this, I think that cygwin copied binutils CVS into the
|
||||
winsup CVS. Maybe I'm crazy. The CVS logs shows a full history, so...
|
||||
But, binutils isn't needed anymore}
|
||||
|
||||
Pick a directory to build in. In my case /0g/sandboxes
|
||||
|
||||
0) download, ./configure, make and install cocom from
|
||||
http://cocom.sourceforge.net/
|
||||
(They have an RPM, but I didn't find a .deb)
|
||||
This gets you the "shakli" program. It is a program to help create
|
||||
fast parsers. I think it is used for the fs emulation layer.
|
||||
|
||||
a) extract gcc-4.0.1
|
||||
b) check out winsup as told on:
|
||||
http://cygwin.com/cvs.html
|
||||
|
||||
d) cd winsup
|
||||
ln -s ../gcc-4.0.1/fixincludes .
|
||||
ln -s ../gcc-4.0.1/gcc .
|
||||
ln -s ../gcc-4.0.1/libcpp .
|
||||
ln -s ../gcc-4.0.1/libstdc++-v3 .
|
||||
rm -rf winsup/mingw # has CC_FOR_TARGET/CC mixups
|
||||
rm -rf sid # has some problem,and we don't need it
|
||||
rm -rf rda # has dependency on intl, which
|
||||
# doesn't get built.
|
||||
|
||||
|
||||
MAKE SURE THAT "." is not in your PATH.
|
||||
Some symlinks are made by the name "as" which can screw things up.
|
||||
|
||||
e) cd ..
|
||||
mkdir build
|
||||
cd build
|
||||
|
||||
../../winsup/configure --prefix=/xelerance/cross/win2k --target=i686-pc-cygwin --without-headers --with-newlib --disable-shared --enable-languages=c,c++
|
||||
make
|
||||
mkdir -p /xelerance/cross/win2k/lib/gcc/i686-pc-cygwin/4.0.1/install-tools/include
|
||||
make install
|
||||
|
||||
f) cat hello/hello.c
|
||||
#include <stdio.h>
|
||||
|
||||
main(int argc, char *argv[])
|
||||
{
|
||||
printf("hello there\n");
|
||||
}
|
||||
|
||||
cd hello
|
||||
PATH=/xelerance/cross/win2k/bin:$PATH export PATH
|
||||
make CC=i686-pc-cygwin-gcc hello
|
||||
scp hello win2kmachine:
|
||||
ssh win2kmachine ./hello
|
||||
|
||||
g) build your favorite stuff, e.g:
|
||||
extract libgmp4,
|
||||
mkdir build/gmp4
|
||||
cd build/gmp4
|
||||
PATH=/xelerance/cross/win2k/bin:$PATH export PATH
|
||||
CC=i686-pc-cygwin-gcc ../../gmp-4.1.2/configure --prefix=/xelerance/cross/win2k/i686-pc-cygwin/include --host=i686-pc-cygwin --with-pic
|
||||
|
||||
(--with-pic gets rid of some issues that I had with the assembly,
|
||||
at a cost of some performance)
|
||||
|
||||
|
||||
WHAT I FIXED
|
||||
============
|
||||
|
||||
CC and CC_FOR_TARGET are confused a lot in the winsup makefiles.
|
||||
CC is only when building stuff you need to run on the local machine.
|
||||
The patch is attached against CVS from 2005-08-03.
|
||||
|
||||
I had an issue with cp-demangle.c. I never resolved it. I don't get it.
|
||||
I later found that it was because I had linked libstdc++ to the gcc-3.4.3
|
||||
version rather than the gcc-4.0.1 version.
|
||||
|
||||
I "fixed" it by doing:
|
||||
|
||||
In winsup/cygwin/Makefile.in, the build of cygwin0.dll (aka ${TEST_DLL_NAME}),
|
||||
has to reference -lcygwin, which hasn't been built/installed yet. (it is in
|
||||
. as libcygwin.a)
|
||||
|
||||
I actually don't think we should -lcygwin at all. Two possible solutions are:
|
||||
|
||||
a) -nostdlib -lstdc++ -luser32 -lkernel32 -ladvapi32 -lshell32 -lgcc
|
||||
b) -L.
|
||||
|
||||
I prefer (a), because we shouldn't be referencing it all.
|
||||
|
||||
I was not able to build mingw, which is why I move it aside in (d).
|
||||
I did not investigate this deeply, since I don't care about native code for
|
||||
the moment.
|
||||
|
||||
WHAT I DID WRONG
|
||||
================
|
||||
|
||||
The first time, I tried building binutils separately.
|
||||
This failed when building GCC 3.x. The problem is that the AR_FOR_TARGET
|
||||
macros used in the makefiles for gcc are, it seems expanded a variable number
|
||||
of times in different paths, and the t=/echo $$t stuff got expanded by MAKE
|
||||
rather than by the shell script.
|
||||
|
||||
I rebuilt again with the ln-s for binutils, and this didn't happen, because
|
||||
one never gets to that part of the condition for AR_FOR_TARGET. So there is
|
||||
still a bug there, but I didn't manage to fix it.
|
||||
|
||||
--
|
||||
] Michael Richardson Xelerance Corporation, Ottawa, ON | firewalls [
|
||||
] mcr @ xelerance.com Now doing IPsec training, see |net architect[
|
||||
] http://www.sandelman.ca/mcr/ www.xelerance.com/training/ |device driver[
|
||||
] I'm a dad: http://www.sandelman.ca/lrmr/ [
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue